mirror of
https://github.com/open5gs/open5gs.git
synced 2025-11-02 21:13:40 +00:00
Compare commits
399 Commits
v2.7.1
...
a22dc21448
| Author | SHA1 | Date | |
|---|---|---|---|
|
|
a22dc21448 | ||
|
|
6d63440b8f | ||
|
|
d2956187ea | ||
|
|
82d7487eef | ||
|
|
be765fe2b0 | ||
|
|
3978db2fa6 | ||
|
|
9d8e94f176 | ||
|
|
05b6af91c1 | ||
|
|
a9955e34d4 | ||
|
|
8669094586 | ||
|
|
994eaa2c9a | ||
|
|
0bf649226b | ||
|
|
8254f12d82 | ||
|
|
548ffff1ff | ||
|
|
f3efd37103 | ||
|
|
9dbc0cffb5 | ||
|
|
edfdd3d126 | ||
|
|
fc42f3039c | ||
|
|
606877bf11 | ||
|
|
a8eec6e9e6 | ||
|
|
0a045eeb12 | ||
|
|
12eb5bbc3d | ||
|
|
62f961bfbf | ||
|
|
5d7d3e755f | ||
|
|
59391d8d5c | ||
|
|
f7889f2be3 | ||
|
|
b11350f969 | ||
|
|
1bdbaa4ef2 | ||
|
|
da27d6eab9 | ||
|
|
a1a42c4e50 | ||
|
|
fb3cba40e5 | ||
|
|
0c56903c98 | ||
|
|
417f6e0e56 | ||
|
|
d787589889 | ||
|
|
f23d7a5e95 | ||
|
|
4e21cff6e6 | ||
|
|
ad80da3060 | ||
|
|
38ab9de5c4 | ||
|
|
f73d81f3be | ||
|
|
66bc558e41 | ||
|
|
60a9707b8e | ||
|
|
a850c4d1d2 | ||
|
|
64bb567aa2 | ||
|
|
753523033d | ||
|
|
e3c3a911fa | ||
|
|
0516e01903 | ||
|
|
d9d3abdd48 | ||
|
|
c58b8f0819 | ||
|
|
b9ec94a0d2 | ||
|
|
c917760a47 | ||
|
|
7b75746fe8 | ||
|
|
f21bc06054 | ||
|
|
fc38ede6a2 | ||
|
|
7575a7be13 | ||
|
|
701505102f | ||
|
|
cf63dd6319 | ||
|
|
f168f7586a | ||
|
|
f47f2bd4f7 | ||
|
|
ae5fda2620 | ||
|
|
345800ba94 | ||
|
|
bca0a7b6e0 | ||
|
|
465e90f45b | ||
|
|
1f30edac27 | ||
|
|
8e5fed1611 | ||
|
|
c86f9150ec | ||
|
|
94cf8ee0e0 | ||
|
|
932101b919 | ||
|
|
67ba7f92bb | ||
|
|
53e9e059ed | ||
|
|
db0196cba7 | ||
|
|
f64a65843a | ||
|
|
8852fbada0 | ||
|
|
52ca325ed5 | ||
|
|
a538e31bed | ||
|
|
ceb764b65f | ||
|
|
245fcda14d | ||
|
|
f0005164a2 | ||
|
|
9f5d133657 | ||
|
|
2daa44adab | ||
|
|
db1887035a | ||
|
|
78bdd63984 | ||
|
|
799103257b | ||
|
|
ae4d8433eb | ||
|
|
e93bc6b5c8 | ||
|
|
73976c938b | ||
|
|
8ec8832318 | ||
|
|
3c1117d4fd | ||
|
|
a35b5af124 | ||
|
|
3e6b7e961d | ||
|
|
78ea40881c | ||
|
|
3a91d2aa3f | ||
|
|
9ce109a9e1 | ||
|
|
8e286b67f1 | ||
|
|
a82a63bb1f | ||
|
|
cfa4457502 | ||
|
|
62cb997552 | ||
|
|
9a524df8c0 | ||
|
|
aab6940cd5 | ||
|
|
3b53144ca5 | ||
|
|
2231e48870 | ||
|
|
c145fc88aa | ||
|
|
e0dc936016 | ||
|
|
3706479582 | ||
|
|
ca61a901d5 | ||
|
|
7b40d5a3f1 | ||
|
|
4c2f40d2c2 | ||
|
|
fba00abd75 | ||
|
|
d3edce9e91 | ||
|
|
cd80aa432e | ||
|
|
90cb00ced3 | ||
|
|
31d3f575d2 | ||
|
|
726b588d76 | ||
|
|
1182a99d04 | ||
|
|
d66d6f868a | ||
|
|
46f74c8019 | ||
|
|
9217889f8a | ||
|
|
6af18a15c3 | ||
|
|
bf1cb6a024 | ||
|
|
51acc388a6 | ||
|
|
7dfd9a3964 | ||
|
|
b326b99f28 | ||
|
|
33fb33be45 | ||
|
|
555395a8e8 | ||
|
|
ae6cedf8e8 | ||
|
|
704083db3b | ||
|
|
1d46a0e475 | ||
|
|
e16a8fc42e | ||
|
|
708f789792 | ||
|
|
a5510f1870 | ||
|
|
fa3edde329 | ||
|
|
63d26667bc | ||
|
|
10b161fbb9 | ||
|
|
9e6b86b84e | ||
|
|
49c5a280da | ||
|
|
8f008c8440 | ||
|
|
7ad40395a0 | ||
|
|
106a9accd4 | ||
|
|
e3dd98cd29 | ||
|
|
70310979c5 | ||
|
|
1abc3b6d5f | ||
|
|
ec7c9a80c1 | ||
|
|
cb2359dca0 | ||
|
|
4012f572ed | ||
|
|
d187ce245b | ||
|
|
6c67863971 | ||
|
|
6fe6b88d9b | ||
|
|
8cae6112cc | ||
|
|
8bdfdcf5df | ||
|
|
f98d0a780d | ||
|
|
1b21eba81e | ||
|
|
6a2225bb68 | ||
|
|
ba05380f5b | ||
|
|
68c6310717 | ||
|
|
b32b1e981b | ||
|
|
f1e1f4a2a9 | ||
|
|
8715915469 | ||
|
|
600a7629ad | ||
|
|
90afca821b | ||
|
|
056b50c9c8 | ||
|
|
e31e9965f0 | ||
|
|
07cb42110e | ||
|
|
e5545669fc | ||
|
|
59f64970dd | ||
|
|
bbfd462406 | ||
|
|
9c36fa5ccd | ||
|
|
350bc271fa | ||
|
|
32cf4daf3a | ||
|
|
b1462f7236 | ||
|
|
81f69b436c | ||
|
|
3f38d66790 | ||
|
|
df11b05a1e | ||
|
|
aaa950e6cf | ||
|
|
9c370ff89a | ||
|
|
ba6a84d1b3 | ||
|
|
78a993c486 | ||
|
|
49d2f76fe1 | ||
|
|
2e68706f1e | ||
|
|
13585a34e3 | ||
|
|
d181ab54cc | ||
|
|
8ff1d1b666 | ||
|
|
df079b48d8 | ||
|
|
ff917e9436 | ||
|
|
04ec945e1d | ||
|
|
90cd67fcca | ||
|
|
c331207233 | ||
|
|
34a9816c7b | ||
|
|
a38530f4f5 | ||
|
|
fce22ca069 | ||
|
|
f04497ac31 | ||
|
|
be5a7e1ded | ||
|
|
3f6f2a8846 | ||
|
|
35a14b595d | ||
|
|
33960bbb66 | ||
|
|
2ce9f2b27e | ||
|
|
badbefe7b3 | ||
|
|
68375f6c35 | ||
|
|
08b9e7c55f | ||
|
|
4016293214 | ||
|
|
3b7654061f | ||
|
|
33532a5858 | ||
|
|
b0bfd35c63 | ||
|
|
b44d159c7b | ||
|
|
6ffd7c978f | ||
|
|
92515a9721 | ||
|
|
531e301f4d | ||
|
|
7e00910bfc | ||
|
|
1b167ef44d | ||
|
|
43bcf08d51 | ||
|
|
525695501e | ||
|
|
e5f50f53f6 | ||
|
|
f780f9af45 | ||
|
|
76060ff22b | ||
|
|
e690005a24 | ||
|
|
c67bddd2b4 | ||
|
|
b8208464a2 | ||
|
|
c3dccf13fc | ||
|
|
02e1729ca6 | ||
|
|
df83767653 | ||
|
|
3358e5128f | ||
|
|
0bbbd0166e | ||
|
|
b47bad8b84 | ||
|
|
f5de72b996 | ||
|
|
f03e220761 | ||
|
|
5ebb2eb76e | ||
|
|
cfff6d28aa | ||
|
|
1c2098bf71 | ||
|
|
1fa8e5468e | ||
|
|
dd7217acde | ||
|
|
1519f73f0f | ||
|
|
85bb717bf6 | ||
|
|
51fd59e7cf | ||
|
|
70c888f4c9 | ||
|
|
e227d57972 | ||
|
|
421126682e | ||
|
|
ae2a3255a5 | ||
|
|
c888e2d62a | ||
|
|
2031f7d8a1 | ||
|
|
1f42ddace1 | ||
|
|
bc02e48d1a | ||
|
|
ce36143f5c | ||
|
|
151275d708 | ||
|
|
0e441cf710 | ||
|
|
e3790b45b4 | ||
|
|
a50c313b81 | ||
|
|
5dc3905c39 | ||
|
|
063fa42a28 | ||
|
|
f82fc85cc2 | ||
|
|
606788361c | ||
|
|
55e5fc92dd | ||
|
|
cf4bbe83fc | ||
|
|
af85bc0a66 | ||
|
|
6834bdf819 | ||
|
|
6d80d4322a | ||
|
|
0c348cac68 | ||
|
|
3d3f18e342 | ||
|
|
778d0cbc59 | ||
|
|
787e555501 | ||
|
|
7bf057ce00 | ||
|
|
95e885bfba | ||
|
|
34220b94cf | ||
|
|
219cda9b4f | ||
|
|
3e154f9571 | ||
|
|
5b66e3159a | ||
|
|
b2f56b9641 | ||
|
|
7293b5f3e4 | ||
|
|
9db907a56e | ||
|
|
a37a2099fc | ||
|
|
902a602a2b | ||
|
|
4308ba7f37 | ||
|
|
91674ffa8a | ||
|
|
36d2fb3ebb | ||
|
|
7fb0690950 | ||
|
|
9cabb279c0 | ||
|
|
b5d1e8ac61 | ||
|
|
9e87c6b1c6 | ||
|
|
34c922a857 | ||
|
|
b530221dea | ||
|
|
dab131d375 | ||
|
|
1a344aeb65 | ||
|
|
8c293bc710 | ||
|
|
5cf92c9851 | ||
|
|
ed68d0b016 | ||
|
|
deef017dfe | ||
|
|
9d83eba550 | ||
|
|
51aca2826f | ||
|
|
5b0a0bf6cf | ||
|
|
c1fb688f15 | ||
|
|
ad80448c11 | ||
|
|
561a55f790 | ||
|
|
b6ddd7fffb | ||
|
|
19f6e0cf96 | ||
|
|
8305c4d50e | ||
|
|
4953628275 | ||
|
|
28f9de4b41 | ||
|
|
591f0a2fca | ||
|
|
9d878d255d | ||
|
|
b6d80cb244 | ||
|
|
d57bb9423b | ||
|
|
681115c4e5 | ||
|
|
2d2e03507b | ||
|
|
0a58a5bcc2 | ||
|
|
ecbe26d8d9 | ||
|
|
3f36e2b8f2 | ||
|
|
62ddcd8757 | ||
|
|
b0c3dbe4dd | ||
|
|
1efdcd6dfd | ||
|
|
333d3fe1c6 | ||
|
|
ed482784b9 | ||
|
|
06df59e654 | ||
|
|
a328f9a2f5 | ||
|
|
cba4479c5c | ||
|
|
d2e9583d77 | ||
|
|
96a64d7c43 | ||
|
|
11e51846d7 | ||
|
|
a7d594c2b7 | ||
|
|
1a22479977 | ||
|
|
90475696f6 | ||
|
|
d7126f98ac | ||
|
|
37430970f7 | ||
|
|
43fa4857cc | ||
|
|
5697cd792e | ||
|
|
d3a17338a0 | ||
|
|
b35dee9327 | ||
|
|
d9a3132400 | ||
|
|
c5025ec64c | ||
|
|
9828509668 | ||
|
|
3f23d332bf | ||
|
|
455f164c60 | ||
|
|
919176a9ab | ||
|
|
2b793b3534 | ||
|
|
08a9291da1 | ||
|
|
8d2d037314 | ||
|
|
a9a60135f9 | ||
|
|
bc3823edc8 | ||
|
|
0af9db84f8 | ||
|
|
3df4447049 | ||
|
|
eebbfd28b3 | ||
|
|
1b82ff08b6 | ||
|
|
6f73a74690 | ||
|
|
b98731de96 | ||
|
|
9ed06f1da1 | ||
|
|
d2ca1dbd13 | ||
|
|
3134bcc5e8 | ||
|
|
ed0c1f4efb | ||
|
|
8c97ccf570 | ||
|
|
be68ea7b04 | ||
|
|
c920f53d39 | ||
|
|
d6cc83bae0 | ||
|
|
3e10963168 | ||
|
|
a5d4254141 | ||
|
|
133fafa395 | ||
|
|
555c20c4c5 | ||
|
|
976f2473b0 | ||
|
|
ab8e46a03d | ||
|
|
c151e4fbce | ||
|
|
253de8ee25 | ||
|
|
c1110573d6 | ||
|
|
6cb518539b | ||
|
|
40e146d45a | ||
|
|
b26f1f310f | ||
|
|
dc2e167a8f | ||
|
|
71e263c0a1 | ||
|
|
2e180796e4 | ||
|
|
9e19d28c4b | ||
|
|
d0f6288484 | ||
|
|
f0206c79f6 | ||
|
|
0de416e43f | ||
|
|
cf7af787dd | ||
|
|
53a63e1b40 | ||
|
|
1111b06ac4 | ||
|
|
7062b9c0d6 | ||
|
|
2a4d8db72e | ||
|
|
4f7f4ec6e5 | ||
|
|
c6c73c1f70 | ||
|
|
f401e7df14 | ||
|
|
87d9cdf569 | ||
|
|
02d302b15a | ||
|
|
15ff23de75 | ||
|
|
b1bf2b10e2 | ||
|
|
bd4d925f0f | ||
|
|
5f425445a8 | ||
|
|
05deed616c | ||
|
|
4599b273fa | ||
|
|
bba0ebe6a4 | ||
|
|
80ab4c4a1b | ||
|
|
95de14c72b | ||
|
|
7a9fea8aec | ||
|
|
9d8d560be7 | ||
|
|
eb28c514ea | ||
|
|
f16f6e3c6c | ||
|
|
190b39a75c | ||
|
|
87b4e4535c | ||
|
|
b57722178a | ||
|
|
7ea82cb87b | ||
|
|
e89aa79efe | ||
|
|
048a74005b | ||
|
|
f6c0ded7b4 | ||
|
|
819861be2f | ||
|
|
4c00edd839 |
2
.github/ISSUE_TEMPLATE/bugreport.yaml
vendored
2
.github/ISSUE_TEMPLATE/bugreport.yaml
vendored
@@ -18,7 +18,7 @@ body:
|
||||
attributes:
|
||||
label: Open5GS Release, Revision, or Tag
|
||||
description: Please check if your issue has been resolved in the latest release.
|
||||
placeholder: v2.6.0
|
||||
placeholder: v2.7.1
|
||||
validations:
|
||||
required: true
|
||||
- type: textarea
|
||||
|
||||
48
.github/ISSUE_TEMPLATE/feature_request.yaml
vendored
48
.github/ISSUE_TEMPLATE/feature_request.yaml
vendored
@@ -1,48 +0,0 @@
|
||||
name: Feature request
|
||||
description: Propose an enhancement to Open5GS
|
||||
labels: ['Enhancement', 'triage']
|
||||
body:
|
||||
- type: markdown
|
||||
attributes:
|
||||
value: >
|
||||
## Feature request
|
||||
Please submit your feature request using the form. If your proposal is not sufficiently
|
||||
well formed, we may request further clarification and expansion. If you're unsure about
|
||||
how to formulate your request, please start a [discussion instead](https://github.com/open5gs/open5gs/dicsussions/).
|
||||
|
||||
- type: input
|
||||
attributes:
|
||||
label: Open5GS Release, Revision, or Tag
|
||||
placeholder: v2.6.0
|
||||
validations:
|
||||
required: true
|
||||
|
||||
- type: input
|
||||
attributes:
|
||||
label: Components and subsystems
|
||||
description: Which subsystems and components would this feature be relevant to?
|
||||
validations:
|
||||
required: true
|
||||
|
||||
- type: textarea
|
||||
attributes:
|
||||
label: Proposed functionality
|
||||
description: >
|
||||
Provide a detailed description of the feature or behaviour you are proposing. Please include any
|
||||
Please include any relevant 3GPP standards and references and include any specific changes to
|
||||
current protocols, processing pipelines, DIAMETER requests/responses, and interfaces. The more detail
|
||||
you provide, the greater the chance your proposal has of being discussed.
|
||||
|
||||
If your feature request does not include anything actionable or sufficient details, you may be asked
|
||||
to provide further clarification or your request may be rejected.
|
||||
validations:
|
||||
required: true
|
||||
|
||||
- type: textarea
|
||||
attributes:
|
||||
label: External dependencies
|
||||
description: >
|
||||
Please detail any new dependencies or implementations that this feature might introduce. e.g. Does the
|
||||
proposal require the installation of additional packages? Are there further external nodes which may be
|
||||
required for integration testing? (Not all feature requests will introduce new dependencies)
|
||||
|
||||
4
.github/workflows/cifuzz.yml
vendored
4
.github/workflows/cifuzz.yml
vendored
@@ -19,14 +19,14 @@ jobs:
|
||||
fuzz-seconds: 300
|
||||
output-sarif: true
|
||||
- name: Upload Crash
|
||||
uses: actions/upload-artifact@v3
|
||||
uses: actions/upload-artifact@v4
|
||||
if: failure() && steps.build.outcome == 'success'
|
||||
with:
|
||||
name: artifacts
|
||||
path: ./out/artifacts
|
||||
- name: Upload Sarif
|
||||
if: always() && steps.build.outcome == 'success'
|
||||
uses: github/codeql-action/upload-sarif@v2
|
||||
uses: github/codeql-action/upload-sarif@v3
|
||||
with:
|
||||
# Path to SARIF file relative to the root of the repository
|
||||
sarif_file: cifuzz-sarif/results.sarif
|
||||
|
||||
88
.github/workflows/meson-ci.yml
vendored
88
.github/workflows/meson-ci.yml
vendored
@@ -2,51 +2,51 @@ name: Meson Continuous Integration
|
||||
on: [push, pull_request]
|
||||
|
||||
jobs:
|
||||
macos-latest:
|
||||
name: Build and Test on MacOS Latest
|
||||
runs-on: macos-latest
|
||||
steps:
|
||||
# - name: Install MongoDB with Package Manager
|
||||
# macos-latest:
|
||||
# name: Build and Test on MacOS Latest
|
||||
# runs-on: macos-latest
|
||||
# steps:
|
||||
## - name: Install MongoDB with Package Manager
|
||||
## run: |
|
||||
## brew tap mongodb/brew
|
||||
## brew install mongodb-community
|
||||
## brew services start mongodb-community
|
||||
# - name: Create the TUN device with the interface name `ogstun`.
|
||||
# run: |
|
||||
# brew tap mongodb/brew
|
||||
# brew install mongodb-community
|
||||
# brew services start mongodb-community
|
||||
- name: Create the TUN device with the interface name `ogstun`.
|
||||
run: |
|
||||
sudo ifconfig lo0 alias 127.0.0.2 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.3 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.4 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.5 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.5 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.6 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.7 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.8 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.9 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.10 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.11 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.12 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.13 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.14 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.15 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.16 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.17 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.18 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.19 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.0.20 netmask 255.255.255.255
|
||||
sudo ifconfig lo0 alias 127.0.1.10 netmask 255.255.255.255
|
||||
- name: Install the dependencies for building the source code.
|
||||
run: brew install mongo-c-driver libidn libmicrohttpd nghttp2 bison libusrsctp libtins talloc meson
|
||||
- name: Check out repository code
|
||||
uses: actions/checkout@main
|
||||
- name: Setup Meson Build
|
||||
run: PATH="/usr/local/opt/bison/bin:$PATH" PKG_CONFIG_PATH="/usr/local/opt/openssl/lib/pkgconfig:$PKG_CONFIG_PATH" meson setup build
|
||||
env:
|
||||
CC: gcc
|
||||
- name : Build Open5GS
|
||||
run: ninja -C build
|
||||
- name: Test Open5GS
|
||||
run: sudo meson test -C build -v crypt unit
|
||||
|
||||
# sudo ifconfig lo0 alias 127.0.0.2 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.3 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.4 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.5 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.5 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.6 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.7 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.8 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.9 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.10 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.11 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.12 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.13 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.14 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.15 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.16 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.17 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.18 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.19 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.0.20 netmask 255.255.255.255
|
||||
# sudo ifconfig lo0 alias 127.0.1.10 netmask 255.255.255.255
|
||||
# - name: Install the dependencies for building the source code.
|
||||
# run: brew install mongo-c-driver libidn libmicrohttpd nghttp2 bison libusrsctp libtins talloc meson
|
||||
# - name: Check out repository code
|
||||
# uses: actions/checkout@main
|
||||
# - name: Setup Meson Build
|
||||
# run: PATH="/usr/local/opt/bison/bin:$PATH" PKG_CONFIG_PATH="/usr/local/opt/openssl/lib/pkgconfig:$PKG_CONFIG_PATH" meson setup build
|
||||
# env:
|
||||
# CC: gcc
|
||||
# - name : Build Open5GS
|
||||
# run: ninja -C build
|
||||
# - name: Test Open5GS
|
||||
# run: sudo meson test -C build -v crypt unit
|
||||
#
|
||||
ubuntu-latest:
|
||||
name: Build and Test on Ubuntu Latest
|
||||
runs-on: ubuntu-latest
|
||||
|
||||
@@ -37,4 +37,8 @@ If you're contributing through a pull request to Open5GS project on GitHub, plea
|
||||
## License
|
||||
|
||||
- Open5GS Open Source files are made available under the terms of the GNU Affero General Public License ([GNU AGPL v3.0](https://www.gnu.org/licenses/agpl-3.0.html)).
|
||||
- [Commercial licenses](https://open5gs.org/open5gs/support/) are also available from [NeoPlane](https://neoplane.io/)
|
||||
- [Commercial licenses](https://open5gs.org/open5gs/support/) are also available from [NewPlane](https://newplane.io/) at [sales@newplane.io](mailto:sales@newplane.io).
|
||||
|
||||
## Support
|
||||
|
||||
Technical support and customized services for Open5GS are provided by [NewPlane](https://newplane.io/) at [support@newplane.io](mailto:support@newplane.io).
|
||||
|
||||
335
configs/attach.yaml.in
Normal file
335
configs/attach.yaml.in
Normal file
@@ -0,0 +1,335 @@
|
||||
db_uri: mongodb://localhost/open5gs
|
||||
|
||||
logger:
|
||||
|
||||
test:
|
||||
serving:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
|
||||
global:
|
||||
parameter:
|
||||
# no_nrf: true
|
||||
# no_scp: true
|
||||
no_sepp: true
|
||||
# no_amf: true
|
||||
# no_smf: true
|
||||
# no_upf: true
|
||||
# no_ausf: true
|
||||
# no_udm: true
|
||||
# no_pcf: true
|
||||
# no_nssf: true
|
||||
# no_bsf: true
|
||||
# no_udr: true
|
||||
# no_mme: true
|
||||
# no_sgwc: true
|
||||
# no_sgwu: true
|
||||
# no_pcrf: true
|
||||
# no_hss: true
|
||||
|
||||
mme:
|
||||
freeDiameter:
|
||||
identity: mme.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.0.2
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: hss.localdomain
|
||||
address: 127.0.0.8
|
||||
|
||||
s1ap:
|
||||
server:
|
||||
- address: 127.0.0.2
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.0.2
|
||||
client:
|
||||
sgwc:
|
||||
- address: 127.0.0.3
|
||||
smf:
|
||||
- address: 127.0.0.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.2
|
||||
port: 9090
|
||||
gummei:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
mme_gid: 2
|
||||
mme_code: 1
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
tac: 1
|
||||
security:
|
||||
integrity_order : [ EIA2, EIA1, EIA0 ]
|
||||
ciphering_order : [ EEA0, EEA1, EEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
time:
|
||||
t3412:
|
||||
value: 540
|
||||
|
||||
sgwc:
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.0.3
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.0.3
|
||||
client:
|
||||
sgwu:
|
||||
- address: 127.0.0.6
|
||||
|
||||
smf:
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.4
|
||||
# port: 7777
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
client:
|
||||
upf:
|
||||
- address: 127.0.0.7
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
port: 9090
|
||||
session:
|
||||
- subnet: 10.45.0.0/16
|
||||
gateway: 10.45.0.1
|
||||
- subnet: 2001:db8:cafe::/48
|
||||
gateway: 2001:db8:cafe::1
|
||||
dns:
|
||||
- 8.8.8.8
|
||||
- 8.8.4.4
|
||||
- 2001:4860:4860::8888
|
||||
- 2001:4860:4860::8844
|
||||
mtu: 1400
|
||||
freeDiameter:
|
||||
identity: smf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.0.4
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: pcrf.localdomain
|
||||
address: 127.0.0.9
|
||||
|
||||
amf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
ngap:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
port: 9090
|
||||
guami:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
amf_id:
|
||||
region: 2
|
||||
set: 1
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
tac: 1
|
||||
plmn_support:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
s_nssai:
|
||||
- sst: 1
|
||||
security:
|
||||
integrity_order : [ NIA2, NIA1, NIA0 ]
|
||||
ciphering_order : [ NEA0, NEA1, NEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
amf_name: open5gs-amf0
|
||||
time:
|
||||
t3512:
|
||||
value: 540 # 9 mintues * 60 = 540 seconds
|
||||
|
||||
sgwu:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.0.6
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.0.6
|
||||
|
||||
upf:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
session:
|
||||
- subnet: 10.45.0.0/16
|
||||
gateway: 10.45.0.1
|
||||
- subnet: 2001:db8:cafe::/48
|
||||
gateway: 2001:db8:cafe::1
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
port: 9090
|
||||
|
||||
hss:
|
||||
freeDiameter:
|
||||
identity: hss.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.0.8
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: mme.localdomain
|
||||
address: 127.0.0.2
|
||||
pcrf:
|
||||
freeDiameter:
|
||||
identity: pcrf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.0.9
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: smf.localdomain
|
||||
address: 127.0.0.4
|
||||
|
||||
nrf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.10
|
||||
port: 7777
|
||||
|
||||
scp:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.200
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
|
||||
ausf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.11
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
udm:
|
||||
hnet:
|
||||
- id: 1
|
||||
scheme: 1
|
||||
key: @build_configs_dir@/open5gs/hnet/curve25519-1.key
|
||||
- id: 2
|
||||
scheme: 2
|
||||
key: @build_configs_dir@/open5gs/hnet/secp256r1-2.key
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.12
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
pcf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.13
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.13
|
||||
port: 9090
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.14
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
nsi:
|
||||
- uri: http://127.0.0.10:7777
|
||||
s_nssai:
|
||||
sst: 1
|
||||
bsf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.15
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.20
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
@@ -59,7 +59,7 @@ mme:
|
||||
smf:
|
||||
- address: 127.0.0.4
|
||||
sgsap:
|
||||
server:
|
||||
client:
|
||||
- address: 127.0.0.2
|
||||
map:
|
||||
tai:
|
||||
|
||||
530
configs/examples/5gc-no-scp-sepp1-999-70.yaml.in
Normal file
530
configs/examples/5gc-no-scp-sepp1-999-70.yaml.in
Normal file
@@ -0,0 +1,530 @@
|
||||
db_uri: mongodb://localhost/open5gs
|
||||
|
||||
logger:
|
||||
|
||||
global:
|
||||
parameter:
|
||||
# no_nrf: true
|
||||
no_scp: true
|
||||
# no_sepp: true
|
||||
# no_amf: true
|
||||
# no_smf: true
|
||||
# no_upf: true
|
||||
# no_ausf: true
|
||||
# no_udm: true
|
||||
# no_pcf: true
|
||||
# no_nssf: true
|
||||
# no_bsf: true
|
||||
# no_udr: true
|
||||
no_mme: true
|
||||
no_sgwc: true
|
||||
no_sgwu: true
|
||||
no_pcrf: true
|
||||
no_hss: true
|
||||
|
||||
mme:
|
||||
freeDiameter:
|
||||
identity: mme.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.1.2
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: hss.localdomain
|
||||
address: 127.0.1.8
|
||||
|
||||
s1ap:
|
||||
server:
|
||||
- address: 127.0.1.2
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.1.2
|
||||
client:
|
||||
sgwc:
|
||||
- address: 127.0.1.3
|
||||
smf:
|
||||
- address: 127.0.1.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.1.2
|
||||
port: 9090
|
||||
gummei:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
mme_gid: 2
|
||||
mme_code: 1
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
tac: 1
|
||||
security:
|
||||
integrity_order : [ EIA2, EIA1, EIA0 ]
|
||||
ciphering_order : [ EEA0, EEA1, EEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
time:
|
||||
t3412:
|
||||
value: 3240
|
||||
|
||||
sgwc:
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.1.3
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.1.3
|
||||
client:
|
||||
sgwu:
|
||||
- address: 127.0.1.6
|
||||
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.1.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.1.4
|
||||
client:
|
||||
upf:
|
||||
- address: 127.0.1.7
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.1.4
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.1.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.1.4
|
||||
port: 9090
|
||||
session:
|
||||
- subnet: 10.45.0.0/16
|
||||
gateway: 10.45.0.1
|
||||
- subnet: 2001:db8:cafe::/48
|
||||
gateway: 2001:db8:cafe::1
|
||||
dns:
|
||||
- 8.8.8.8
|
||||
- 8.8.4.4
|
||||
- 2001:4860:4860::8888
|
||||
- 2001:4860:4860::8844
|
||||
mtu: 1400
|
||||
freeDiameter:
|
||||
identity: smf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.1.4
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: pcrf.localdomain
|
||||
address: 127.0.1.9
|
||||
|
||||
amf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.5
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
ngap:
|
||||
server:
|
||||
- address: 127.0.1.5
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.1.5
|
||||
port: 9090
|
||||
access_control:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
guami:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
amf_id:
|
||||
region: 2
|
||||
set: 1
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
tac: 1
|
||||
plmn_support:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
s_nssai:
|
||||
- sst: 1
|
||||
security:
|
||||
integrity_order : [ NIA2, NIA1, NIA0 ]
|
||||
ciphering_order : [ NEA0, NEA1, NEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
amf_name: open5gs-amf0
|
||||
time:
|
||||
t3512:
|
||||
value: 540 # 9 mintues * 60 = 540 seconds
|
||||
|
||||
sgwu:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.1.6
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.1.6
|
||||
|
||||
upf:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.1.7
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.1.7
|
||||
session:
|
||||
- subnet: 10.45.0.0/16
|
||||
gateway: 10.45.0.1
|
||||
- subnet: 2001:db8:cafe::/48
|
||||
gateway: 2001:db8:cafe::1
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.1.7
|
||||
port: 9090
|
||||
|
||||
hss:
|
||||
freeDiameter:
|
||||
identity: hss.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.1.8
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: mme.localdomain
|
||||
address: 127.0.1.2
|
||||
pcrf:
|
||||
freeDiameter:
|
||||
identity: pcrf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.1.9
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: smf.localdomain
|
||||
address: 127.0.1.4
|
||||
|
||||
nrf:
|
||||
serving:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.1.10
|
||||
# port: 7777
|
||||
- address: nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
|
||||
sepp:
|
||||
default:
|
||||
tls:
|
||||
server:
|
||||
private_key: @build_configs_dir@/open5gs/tls/sepp1.key
|
||||
cert: @build_configs_dir@/open5gs/tls/sepp1.crt
|
||||
client:
|
||||
cacert: @build_configs_dir@/open5gs/tls/ca.crt
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.250
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
n32:
|
||||
server:
|
||||
- sender: sepp1.localdomain
|
||||
address: 127.0.1.251
|
||||
port: 7777
|
||||
n32f:
|
||||
address: 127.0.1.252
|
||||
port: 7777
|
||||
client:
|
||||
sepp:
|
||||
- receiver: sepp2.localdomain
|
||||
uri: http://127.0.2.251:7777
|
||||
n32f:
|
||||
uri: http://127.0.2.252:7777
|
||||
- receiver: sepp3.localdomain
|
||||
uri: http://127.0.3.251:7777
|
||||
n32f:
|
||||
uri: http://127.0.3.252:7777
|
||||
|
||||
ausf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.1.11
|
||||
# port: 7777
|
||||
- address: ausf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
|
||||
udm:
|
||||
hnet:
|
||||
- id: 1
|
||||
scheme: 1
|
||||
key: @build_configs_dir@/open5gs/hnet/curve25519-1.key
|
||||
- id: 2
|
||||
scheme: 2
|
||||
key: @build_configs_dir@/open5gs/hnet/secp256r1-2.key
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.1.12
|
||||
# port: 7777
|
||||
- address: udm.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
|
||||
pcf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.13
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.1.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.1.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
nsi:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
s_nssai:
|
||||
sst: 1
|
||||
bsf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.15
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.20
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
532
configs/examples/5gc-no-scp-sepp2-001-01.yaml.in
Normal file
532
configs/examples/5gc-no-scp-sepp2-001-01.yaml.in
Normal file
@@ -0,0 +1,532 @@
|
||||
db_uri: mongodb://localhost/open5gs
|
||||
|
||||
logger:
|
||||
|
||||
global:
|
||||
parameter:
|
||||
# no_nrf: true
|
||||
no_scp: true
|
||||
# no_sepp: true
|
||||
# no_amf: true
|
||||
# no_smf: true
|
||||
# no_upf: true
|
||||
# no_ausf: true
|
||||
# no_udm: true
|
||||
# no_pcf: true
|
||||
# no_nssf: true
|
||||
# no_bsf: true
|
||||
# no_udr: true
|
||||
no_mme: true
|
||||
no_sgwc: true
|
||||
no_sgwu: true
|
||||
no_pcrf: true
|
||||
no_hss: true
|
||||
|
||||
mme:
|
||||
freeDiameter:
|
||||
identity: mme.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.2.2
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: hss.localdomain
|
||||
address: 127.0.2.8
|
||||
|
||||
s1ap:
|
||||
server:
|
||||
- address: 127.0.2.2
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.2.2
|
||||
client:
|
||||
sgwc:
|
||||
- address: 127.0.2.3
|
||||
smf:
|
||||
- address: 127.0.2.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.2.2
|
||||
port: 9090
|
||||
gummei:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
mme_gid: 2
|
||||
mme_code: 1
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
tac: 1
|
||||
security:
|
||||
integrity_order : [ EIA2, EIA1, EIA0 ]
|
||||
ciphering_order : [ EEA0, EEA1, EEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
time:
|
||||
t3412:
|
||||
value: 3240
|
||||
|
||||
sgwc:
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.2.3
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.2.3
|
||||
client:
|
||||
sgwu:
|
||||
- address: 127.0.2.6
|
||||
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.2.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.2.4
|
||||
client:
|
||||
upf:
|
||||
- address: 127.0.2.7
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.2.4
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.2.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.2.4
|
||||
port: 9090
|
||||
session:
|
||||
- subnet: 10.46.0.0/16
|
||||
gateway: 10.46.0.1
|
||||
- subnet: 2001:db8:babe::/48
|
||||
gateway: 2001:db8:babe::1
|
||||
dns:
|
||||
- 8.8.8.8
|
||||
- 8.8.4.4
|
||||
- 2001:4860:4860::8888
|
||||
- 2001:4860:4860::8844
|
||||
mtu: 1400
|
||||
freeDiameter:
|
||||
identity: smf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.2.4
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: pcrf.localdomain
|
||||
address: 127.0.2.9
|
||||
|
||||
amf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.5
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
ngap:
|
||||
server:
|
||||
- address: 127.0.2.5
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.2.5
|
||||
port: 9090
|
||||
access_control:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
guami:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
amf_id:
|
||||
region: 2
|
||||
set: 1
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
tac: 1
|
||||
plmn_support:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
s_nssai:
|
||||
- sst: 1
|
||||
security:
|
||||
integrity_order : [ NIA2, NIA1, NIA0 ]
|
||||
ciphering_order : [ NEA0, NEA1, NEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
amf_name: open5gs-amf0
|
||||
time:
|
||||
t3512:
|
||||
value: 540 # 9 mintues * 60 = 540 seconds
|
||||
|
||||
sgwu:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.2.6
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.2.6
|
||||
|
||||
upf:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.2.7
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.2.7
|
||||
session:
|
||||
- subnet: 10.46.0.0/16
|
||||
gateway: 10.46.0.1
|
||||
dev: ogstun2
|
||||
- subnet: 2001:db8:babe::/48
|
||||
gateway: 2001:db8:babe::1
|
||||
dev: ogstun2
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.2.7
|
||||
port: 9090
|
||||
|
||||
hss:
|
||||
freeDiameter:
|
||||
identity: hss.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.2.8
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: mme.localdomain
|
||||
address: 127.0.2.2
|
||||
pcrf:
|
||||
freeDiameter:
|
||||
identity: pcrf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.2.9
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: smf.localdomain
|
||||
address: 127.0.2.4
|
||||
|
||||
nrf:
|
||||
serving:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.2.10
|
||||
# port: 7777
|
||||
- address: nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
|
||||
sepp:
|
||||
default:
|
||||
tls:
|
||||
server:
|
||||
private_key: @build_configs_dir@/open5gs/tls/sepp2.key
|
||||
cert: @build_configs_dir@/open5gs/tls/sepp2.crt
|
||||
client:
|
||||
cacert: @build_configs_dir@/open5gs/tls/ca.crt
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.250
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
n32:
|
||||
server:
|
||||
- sender: sepp2.localdomain
|
||||
address: 127.0.2.251
|
||||
port: 7777
|
||||
n32f:
|
||||
address: 127.0.2.252
|
||||
port: 7777
|
||||
client:
|
||||
sepp:
|
||||
- receiver: sepp1.localdomain
|
||||
uri: http://127.0.1.251:7777
|
||||
n32f:
|
||||
uri: http://127.0.1.252:7777
|
||||
- receiver: sepp3.localdomain
|
||||
uri: http://127.0.3.251:7777
|
||||
n32f:
|
||||
uri: http://127.0.3.252:7777
|
||||
|
||||
ausf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.2.11
|
||||
# port: 7777
|
||||
- address: ausf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
|
||||
udm:
|
||||
hnet:
|
||||
- id: 1
|
||||
scheme: 1
|
||||
key: @build_configs_dir@/open5gs/hnet/curve25519-1.key
|
||||
- id: 2
|
||||
scheme: 2
|
||||
key: @build_configs_dir@/open5gs/hnet/secp256r1-2.key
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.2.12
|
||||
# port: 7777
|
||||
- address: udm.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
|
||||
pcf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.13
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.2.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.2.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
nsi:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
s_nssai:
|
||||
sst: 1
|
||||
bsf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.15
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.20
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
532
configs/examples/5gc-no-scp-sepp3-315-010.yaml.in
Normal file
532
configs/examples/5gc-no-scp-sepp3-315-010.yaml.in
Normal file
@@ -0,0 +1,532 @@
|
||||
db_uri: mongodb://localhost/open5gs
|
||||
|
||||
logger:
|
||||
|
||||
global:
|
||||
parameter:
|
||||
# no_nrf: true
|
||||
no_scp: true
|
||||
# no_sepp: true
|
||||
# no_amf: true
|
||||
# no_smf: true
|
||||
# no_upf: true
|
||||
# no_ausf: true
|
||||
# no_udm: true
|
||||
# no_pcf: true
|
||||
# no_nssf: true
|
||||
# no_bsf: true
|
||||
# no_udr: true
|
||||
no_mme: true
|
||||
no_sgwc: true
|
||||
no_sgwu: true
|
||||
no_pcrf: true
|
||||
no_hss: true
|
||||
|
||||
mme:
|
||||
freeDiameter:
|
||||
identity: mme.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.3.2
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: hss.localdomain
|
||||
address: 127.0.3.8
|
||||
|
||||
s1ap:
|
||||
server:
|
||||
- address: 127.0.3.2
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.3.2
|
||||
client:
|
||||
sgwc:
|
||||
- address: 127.0.3.3
|
||||
smf:
|
||||
- address: 127.0.3.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.3.2
|
||||
port: 9090
|
||||
gummei:
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
mme_gid: 2
|
||||
mme_code: 1
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
tac: 1
|
||||
security:
|
||||
integrity_order : [ EIA2, EIA1, EIA0 ]
|
||||
ciphering_order : [ EEA0, EEA1, EEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
time:
|
||||
t3412:
|
||||
value: 3240
|
||||
|
||||
sgwc:
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.3.3
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.3.3
|
||||
client:
|
||||
sgwu:
|
||||
- address: 127.0.3.6
|
||||
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.3.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.3.4
|
||||
client:
|
||||
upf:
|
||||
- address: 127.0.3.7
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.3.4
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.3.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.3.4
|
||||
port: 9090
|
||||
session:
|
||||
- subnet: 10.47.0.0/16
|
||||
gateway: 10.47.0.1
|
||||
- subnet: 2001:db8:face::/48
|
||||
gateway: 2001:db8:face::1
|
||||
dns:
|
||||
- 8.8.8.8
|
||||
- 8.8.4.4
|
||||
- 2001:4860:4860::8888
|
||||
- 2001:4860:4860::8844
|
||||
mtu: 1400
|
||||
freeDiameter:
|
||||
identity: smf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.3.4
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: pcrf.localdomain
|
||||
address: 127.0.3.9
|
||||
|
||||
amf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.5
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
ngap:
|
||||
server:
|
||||
- address: 127.0.3.5
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.3.5
|
||||
port: 9090
|
||||
access_control:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
guami:
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
amf_id:
|
||||
region: 2
|
||||
set: 1
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
tac: 1
|
||||
plmn_support:
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
s_nssai:
|
||||
- sst: 1
|
||||
security:
|
||||
integrity_order : [ NIA2, NIA1, NIA0 ]
|
||||
ciphering_order : [ NEA0, NEA1, NEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
amf_name: open5gs-amf0
|
||||
time:
|
||||
t3512:
|
||||
value: 540 # 9 mintues * 60 = 540 seconds
|
||||
|
||||
sgwu:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.3.6
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.3.6
|
||||
|
||||
upf:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.3.7
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.3.7
|
||||
session:
|
||||
- subnet: 10.47.0.0/16
|
||||
gateway: 10.47.0.1
|
||||
dev: ogstun3
|
||||
- subnet: 2001:db8:face::/48
|
||||
gateway: 2001:db8:face::1
|
||||
dev: ogstun3
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.3.7
|
||||
port: 9090
|
||||
|
||||
hss:
|
||||
freeDiameter:
|
||||
identity: hss.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.3.8
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: mme.localdomain
|
||||
address: 127.0.3.2
|
||||
pcrf:
|
||||
freeDiameter:
|
||||
identity: pcrf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.3.9
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: smf.localdomain
|
||||
address: 127.0.3.4
|
||||
|
||||
nrf:
|
||||
serving:
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.3.10
|
||||
# port: 7777
|
||||
- address: nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
|
||||
sepp:
|
||||
default:
|
||||
tls:
|
||||
server:
|
||||
private_key: @build_configs_dir@/open5gs/tls/sepp3.key
|
||||
cert: @build_configs_dir@/open5gs/tls/sepp3.crt
|
||||
client:
|
||||
cacert: @build_configs_dir@/open5gs/tls/ca.crt
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.250
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
n32:
|
||||
server:
|
||||
- sender: sepp3.localdomain
|
||||
address: 127.0.3.251
|
||||
port: 7777
|
||||
n32f:
|
||||
address: 127.0.3.252
|
||||
port: 7777
|
||||
client:
|
||||
sepp:
|
||||
- receiver: sepp1.localdomain
|
||||
uri: http://127.0.1.251:7777
|
||||
n32f:
|
||||
uri: http://127.0.1.252:7777
|
||||
- receiver: sepp2.localdomain
|
||||
uri: http://127.0.2.251:7777
|
||||
n32f:
|
||||
uri: http://127.0.2.252:7777
|
||||
|
||||
ausf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.3.11
|
||||
# port: 7777
|
||||
- address: ausf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
|
||||
udm:
|
||||
hnet:
|
||||
- id: 1
|
||||
scheme: 1
|
||||
key: @build_configs_dir@/open5gs/hnet/curve25519-1.key
|
||||
- id: 2
|
||||
scheme: 2
|
||||
key: @build_configs_dir@/open5gs/hnet/secp256r1-2.key
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.3.12
|
||||
# port: 7777
|
||||
- address: udm.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
|
||||
pcf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.13
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.3.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
# - address: 127.0.3.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
nsi:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
s_nssai:
|
||||
sst: 1
|
||||
bsf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.15
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.20
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://nrf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
@@ -90,8 +90,9 @@ sgwc:
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.4
|
||||
port: 7777
|
||||
# - address: 127.0.1.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.1.200:7777
|
||||
@@ -350,9 +351,9 @@ pcf:
|
||||
- address: 127.0.1.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
- supi_range:
|
||||
- 001010000000001-001019999999999
|
||||
- 315010000000001-315010999999999
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
@@ -428,90 +429,12 @@ pcf:
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.14
|
||||
port: 7777
|
||||
# - address: 127.0.1.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.1.200:7777
|
||||
|
||||
@@ -90,8 +90,9 @@ sgwc:
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.4
|
||||
port: 7777
|
||||
# - address: 127.0.2.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.2.200:7777
|
||||
@@ -351,9 +352,9 @@ pcf:
|
||||
- address: 127.0.2.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
- supi_range:
|
||||
- 999700000000001-999709999999999
|
||||
- 315010000000001-315010999999999
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
@@ -429,90 +430,12 @@ pcf:
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.14
|
||||
port: 7777
|
||||
# - address: 127.0.2.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.2.200:7777
|
||||
|
||||
@@ -90,8 +90,9 @@ sgwc:
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.4
|
||||
port: 7777
|
||||
# - address: 127.0.3.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.3.200:7777
|
||||
@@ -351,9 +352,9 @@ pcf:
|
||||
- address: 127.0.3.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
- supi_range:
|
||||
- 999700000000001-999709999999999
|
||||
- 001010000000001-001019999999999
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
@@ -429,90 +430,12 @@ pcf:
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.14
|
||||
port: 7777
|
||||
# - address: 127.0.3.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.3.200:7777
|
||||
|
||||
@@ -91,8 +91,9 @@ sgwc:
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.4
|
||||
port: 7777
|
||||
# - address: 127.0.1.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.1.200:7777
|
||||
@@ -355,9 +356,9 @@ pcf:
|
||||
- address: 127.0.1.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
- supi_range:
|
||||
- 001010000000001-001019999999999
|
||||
- 315010000000001-315010999999999
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
@@ -433,90 +434,12 @@ pcf:
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.1.14
|
||||
port: 7777
|
||||
# - address: 127.0.1.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc070.mcc999.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.1.200:7777
|
||||
|
||||
@@ -91,8 +91,9 @@ sgwc:
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.4
|
||||
port: 7777
|
||||
# - address: 127.0.2.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.2.200:7777
|
||||
@@ -356,9 +357,9 @@ pcf:
|
||||
- address: 127.0.2.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
- supi_range:
|
||||
- 999700000000001-999709999999999
|
||||
- 315010000000001-315010999999999
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
@@ -434,90 +435,12 @@ pcf:
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 315
|
||||
mnc: 010
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.14
|
||||
port: 7777
|
||||
# - address: 127.0.2.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc001.mcc001.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.2.200:7777
|
||||
|
||||
@@ -91,8 +91,9 @@ sgwc:
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.4
|
||||
port: 7777
|
||||
# - address: 127.0.3.4
|
||||
# port: 7777
|
||||
- address: smf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.3.200:7777
|
||||
@@ -356,9 +357,9 @@ pcf:
|
||||
- address: 127.0.3.13
|
||||
port: 9090
|
||||
policy:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
- supi_range:
|
||||
- 999700000000001-999709999999999
|
||||
- 001010000000001-001010999999999
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
@@ -434,90 +435,12 @@ pcf:
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- plmn_id:
|
||||
mcc: 001
|
||||
mnc: 01
|
||||
slice:
|
||||
- sst: 1 # 1,2,3,4
|
||||
default_indicator: true
|
||||
session:
|
||||
- name: internet
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3
|
||||
qos:
|
||||
index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
- name: ims
|
||||
type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
ambr:
|
||||
downlink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 1
|
||||
unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
qos:
|
||||
index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
pcc_rule:
|
||||
- qos:
|
||||
index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 82
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
- qos:
|
||||
index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
arp:
|
||||
priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
mbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
gbr:
|
||||
downlink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
uplink:
|
||||
value: 802
|
||||
unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.3.14
|
||||
port: 7777
|
||||
# - address: 127.0.3.14
|
||||
# port: 7777
|
||||
- address: nssf.5gc.mnc010.mcc315.3gppnetwork.org
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.3.200:7777
|
||||
|
||||
@@ -325,6 +325,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.2.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -325,6 +325,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.3.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -320,6 +320,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.1.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -325,6 +325,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.2.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -320,6 +320,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.3.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -325,6 +325,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.1.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -325,6 +325,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.2.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -325,6 +325,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.3.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -320,6 +320,15 @@ bsf:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
af:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.16
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.1.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
|
||||
@@ -19,6 +19,9 @@ examples_conf = '''
|
||||
5gc-sepp1-999-70.yaml
|
||||
5gc-sepp2-001-01.yaml
|
||||
5gc-sepp3-315-010.yaml
|
||||
5gc-no-scp-sepp1-999-70.yaml
|
||||
5gc-no-scp-sepp2-001-01.yaml
|
||||
5gc-no-scp-sepp3-315-010.yaml
|
||||
5gc-tls-sepp1-999-70.yaml
|
||||
5gc-tls-sepp2-001-01.yaml
|
||||
5gc-tls-sepp3-315-010.yaml
|
||||
|
||||
@@ -32,6 +32,7 @@ conf_data.set('build_subprojects_freeDiameter_extensions_dir',
|
||||
|
||||
example_conf = '''
|
||||
sample.yaml
|
||||
attach.yaml
|
||||
310014.yaml
|
||||
csfb.yaml
|
||||
volte.yaml
|
||||
@@ -39,6 +40,8 @@ example_conf = '''
|
||||
slice.yaml
|
||||
srsenb.yaml
|
||||
non3gpp.yaml
|
||||
transfer.yaml
|
||||
transfer-error-case.yaml
|
||||
'''.split()
|
||||
|
||||
foreach file : example_conf
|
||||
|
||||
@@ -59,43 +59,83 @@ amf:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-amf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-amf.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: amf.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.5 and advertise as open5gs-amf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.5
|
||||
# port: 7777
|
||||
# advertise: open5gs-amf.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.5
|
||||
# port: 7777
|
||||
# advertise: open5gs-amf.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
################################################################################
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect communication with delegated discovery
|
||||
# o Indirect Communication by Delegating to SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect communication without delegated discovery
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# discovery:
|
||||
# delegated: no
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: no # Directly communicate NRF discovery
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegated Discovery
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: yes # Delegate discovery to SCP
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -117,6 +157,27 @@ amf:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/amf.key
|
||||
# cert: @sysconfdir@/open5gs/tls/amf.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/amf-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/amf-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: amf.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -22,43 +22,83 @@ ausf:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-ausf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-ausf.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: ausf.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.11 and advertise as open5gs-ausf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.11
|
||||
# port: 7777
|
||||
# advertise: open5gs-ausf.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.11
|
||||
# port: 7777
|
||||
# advertise: open5gs-ausf.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
################################################################################
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect communication with delegated discovery
|
||||
# o Indirect Communication by Delegating to SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect communication without delegated discovery
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# discovery:
|
||||
# delegated: no
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: no # Directly communicate NRF discovery
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegated Discovery
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: yes # Delegate discovery to SCP
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -80,6 +120,27 @@ ausf:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/ausf.key
|
||||
# cert: @sysconfdir@/open5gs/tls/ausf.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/ausf-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/ausf-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: ausf.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -22,43 +22,83 @@ bsf:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-bsf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-bsf.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: bsf.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.15 and advertise as open5gs-bsf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.15
|
||||
# port: 7777
|
||||
# advertise: open5gs-bsf.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.15
|
||||
# port: 7777
|
||||
# advertise: open5gs-bsf.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
################################################################################
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect communication with delegated discovery
|
||||
# o Indirect Communication by Delegating to SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect communication without delegated discovery
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# discovery:
|
||||
# delegated: no
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: no # Directly communicate NRF discovery
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegated Discovery
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: yes # Delegate discovery to SCP
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -80,6 +120,27 @@ bsf:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/bsf.key
|
||||
# cert: @sysconfdir@/open5gs/tls/bsf.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/bsf-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/bsf-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: bsf.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -11,5 +11,9 @@ global:
|
||||
|
||||
hss:
|
||||
freeDiameter: @sysconfdir@/freeDiameter/hss.conf
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.8
|
||||
port: 9090
|
||||
# sms_over_ims: "sip:smsc.mnc001.mcc001.3gppnetwork.org:7060;transport=tcp"
|
||||
# use_mongodb_change_stream: true
|
||||
|
||||
@@ -164,8 +164,9 @@ mme:
|
||||
################################################################################
|
||||
# o MSC/VLR
|
||||
# sgsap:
|
||||
# server:
|
||||
# - address: 127.0.0.2
|
||||
# client:
|
||||
# - address: msc.open5gs.org # SCTP server address configured on the MSC/VLR
|
||||
# local_address: 127.0.0.2 # SCTP local IP addresses to be bound in the MME
|
||||
# map:
|
||||
# tai:
|
||||
# plmn_id:
|
||||
@@ -188,7 +189,15 @@ mme:
|
||||
# mcc: 002
|
||||
# mnc: 02
|
||||
# lac: 43692
|
||||
# - address: msc.open5gs.org
|
||||
# - address: # SCTP server address configured on the MSC/VLR
|
||||
# - 127.0.0.88
|
||||
# - 10.0.0.88
|
||||
# - 172.16.0.88
|
||||
# - 2001:db8:babe::88
|
||||
# local_address: # SCTP local IP addresses to be bound in the MME
|
||||
# - 127.0.0.2
|
||||
# - 192.168.1.4
|
||||
# - 2001:db8:cafe::2
|
||||
# map:
|
||||
# tai:
|
||||
# plmn_id:
|
||||
@@ -277,5 +286,23 @@ mme:
|
||||
# mcc: 999
|
||||
# mnc: 70
|
||||
#
|
||||
# o HSS Selection
|
||||
# o realm and host are optional
|
||||
# o realm will be generated from plmn_id if not provided
|
||||
# o host will not be used if not provided
|
||||
# hss_map:
|
||||
# - plmn_id:
|
||||
# mcc: 001
|
||||
# mnc: 01
|
||||
# - plmn_id:
|
||||
# mcc: 002
|
||||
# mnc: 02
|
||||
# realm: epc.mnc002.mcc002.3gppnetwork.org
|
||||
# - plmn_id:
|
||||
# mcc: 999
|
||||
# mnc: 70
|
||||
# realm: localdomain
|
||||
# host: hss.localdomain
|
||||
#
|
||||
# o Relative Capacity
|
||||
# relative_capacity: 100
|
||||
|
||||
@@ -21,18 +21,31 @@ nrf:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-nrf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-nrf.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: nrf.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.10 and advertise as open5gs-nrf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.10
|
||||
# port: 7777
|
||||
# advertise: open5gs-nrf.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.10
|
||||
# port: 7777
|
||||
# advertise: open5gs-nrf.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -51,6 +64,24 @@ nrf:
|
||||
# server:
|
||||
# - address: nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/nrf.key
|
||||
# cert: @sysconfdir@/open5gs/tls/nrf.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/nrf-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/nrf-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -25,18 +25,31 @@ nssf:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-nssf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-nssf.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: nssf.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.14 and advertise as open5gs-nssf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.14
|
||||
# port: 7777
|
||||
# advertise: open5gs-nssf.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.14
|
||||
# port: 7777
|
||||
# advertise: open5gs-nssf.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
@@ -64,27 +77,55 @@ nssf:
|
||||
# sst: 1
|
||||
# sd: 009000
|
||||
#
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect communication with delegated discovery
|
||||
# o Indirect Communication by Delegating to SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect communication without delegated discovery
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# discovery:
|
||||
# delegated: no
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: no # Directly communicate NRF discovery
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegated Discovery
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: yes # Delegate discovery to SCP
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -110,6 +151,31 @@ nssf:
|
||||
# s_nssai:
|
||||
# sst: 1
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/nssf.key
|
||||
# cert: @sysconfdir@/open5gs/tls/nssf.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/nssf-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/nssf-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: nssf.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
# nsi:
|
||||
# - uri: https://nrf.localdomain
|
||||
# s_nssai:
|
||||
# sst: 1
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -25,73 +25,85 @@ pcf:
|
||||
port: 9090
|
||||
|
||||
################################################################################
|
||||
# Locally configured policy
|
||||
# - The PCF in the VPLMN uses locally configured policies
|
||||
# according to the roaming agreement with the HPLMN operator
|
||||
# as input for PCC Rule generation.
|
||||
# PCF Policy Configuration: UE Home PLMN and SUPI Range Based Policies
|
||||
################################################################################
|
||||
#
|
||||
# o You don't have to use MongoDB if you use the policy configuration as below.
|
||||
# This configuration applies policies based on the UE's home PLMN ID and
|
||||
# SUPI range. When both supi_range and plmn_id are specified in a policy,
|
||||
# the policy is applied only if both conditions are met.
|
||||
#
|
||||
# supi_range: Specifies one or more ranges of SUPIs. A maximum of 16 ranges
|
||||
# can be defined.
|
||||
# plmn_id : Specifies the UE's home PLMN using MCC and MNC.
|
||||
#
|
||||
# Example:
|
||||
#
|
||||
# policy:
|
||||
# - plmn_id:
|
||||
# - supi_range: # Filter policies by SUPI
|
||||
# - 999700000000001-999709999999999
|
||||
# - 315010000000001-315010999999999
|
||||
# plmn_id: # Filter policies by home PLMN-ID
|
||||
# mcc: 999
|
||||
# mnc: 70
|
||||
# slice:
|
||||
# - sst: 1 # 1,2,3,4
|
||||
# slice: # Specify slice configuration
|
||||
# - sst: 1 # Allowed values: 1, 2, 3, 4
|
||||
# default_indicator: true
|
||||
# session:
|
||||
# session: # Define session based on DNN
|
||||
# - name: internet
|
||||
# type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
# type: 3 # 1: IPv4, 2: IPv6, 3: IPv4v6
|
||||
# ambr:
|
||||
# downlink:
|
||||
# value: 1
|
||||
# unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 3 # 0: bps, 1: Kbps, 2: Mbps, 3: Gbps, 4: Tbps
|
||||
# uplink:
|
||||
# value: 1
|
||||
# unit: 3
|
||||
# qos:
|
||||
# index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# index: 9 # Allowed values: 1,2,3,4,65,66,67,75,71,72,
|
||||
# # 73,74,76,5,6,7,8,9,69,70,79,80,82,83,
|
||||
# # 84,85,86
|
||||
# arp:
|
||||
# priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
# priority_level: 8 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2: Enabled
|
||||
# - name: ims
|
||||
# type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
# type: 3 # 1: IPv4, 2: IPv6, 3: IPv4v6
|
||||
# ambr:
|
||||
# downlink:
|
||||
# value: 1
|
||||
# unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 3 # 0: bps, 1: Kbps, 2: Mbps, 3: Gbps, 4: Tbps
|
||||
# uplink:
|
||||
# value: 1
|
||||
# unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 3
|
||||
# qos:
|
||||
# index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# index: 5 # Allowed values: 1,2,3,4,65,66,67,75,71,72,
|
||||
# # 73,74,76,5,6,7,8,9,69,70,79,80,82,83,
|
||||
# # 84,85,86
|
||||
# arp:
|
||||
# priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
# priority_level: 1 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2: Enabled
|
||||
# pcc_rule:
|
||||
# - qos:
|
||||
# index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# index: 1 # Allowed values as above
|
||||
# arp:
|
||||
# priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
# priority_level: 1 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2: Enabled
|
||||
# mbr:
|
||||
# downlink:
|
||||
# value: 82
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 1 # 0: bps, 1: Kbps, 2: Mbps, 3: Gbps, 4: Tbps
|
||||
# uplink:
|
||||
# value: 82
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 1
|
||||
# gbr:
|
||||
# downlink:
|
||||
# value: 82
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 1
|
||||
# uplink:
|
||||
# value: 82
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 1
|
||||
# flow:
|
||||
# - direction: 2
|
||||
# description: "permit out icmp from any to assigned"
|
||||
@@ -102,89 +114,129 @@ pcf:
|
||||
# - direction: 1
|
||||
# description: "permit out udp from 10.200.136.98/32 1-65535 to assigned 50021"
|
||||
# - qos:
|
||||
# index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# index: 2 # Allowed values as above
|
||||
# arp:
|
||||
# priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
# priority_level: 4 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 2 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 2 # 1: Disabled, 2: Enabled
|
||||
# mbr:
|
||||
# downlink:
|
||||
# value: 802
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 1
|
||||
# uplink:
|
||||
# value: 802
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 1
|
||||
# gbr:
|
||||
# downlink:
|
||||
# value: 802
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 1
|
||||
# uplink:
|
||||
# value: 802
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# - plmn_id:
|
||||
# mcc: 001
|
||||
# mnc: 01
|
||||
# slice:
|
||||
# - sst: 1 # 1,2,3,4
|
||||
# unit: 1
|
||||
#
|
||||
# - supi_range: # Filter policies by SUPI only
|
||||
# - 001010000000001-001019999999999
|
||||
# slice: # Specify slice configuration
|
||||
# - sst: 1 # Allowed values: 1, 2, 3, 4
|
||||
# sd: 000001
|
||||
# default_indicator: true
|
||||
# session:
|
||||
# session: # Define session based on DNN
|
||||
# - name: internet
|
||||
# type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
# type: 3 # 1: IPv4, 2: IPv6, 3: IPv4v6
|
||||
# ambr:
|
||||
# downlink:
|
||||
# value: 1
|
||||
# unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# unit: 3 # 0: bps, 1: Kbps, 2: Mbps, 3: Gbps, 4: Tbps
|
||||
# uplink:
|
||||
# value: 1
|
||||
# unit: 3
|
||||
# qos:
|
||||
# index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# index: 9 # Allowed values as above
|
||||
# arp:
|
||||
# priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
# priority_level: 8 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2: Enabled
|
||||
#
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-pcf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-pcf.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: pcf.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.13 and advertise as open5gs-pcf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.13
|
||||
# port: 7777
|
||||
# advertise: open5gs-pcf.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.13
|
||||
# port: 7777
|
||||
# advertise: open5gs-pcf.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
################################################################################
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect communication with delegated discovery
|
||||
# o Indirect Communication by Delegating to SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect communication without delegated discovery
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# discovery:
|
||||
# delegated: no
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: no # Directly communicate NRF discovery
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegated Discovery
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: yes # Delegate discovery to SCP
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -206,6 +258,27 @@ pcf:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/pcf.key
|
||||
# cert: @sysconfdir@/open5gs/tls/pcf.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/pcf-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/pcf-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: pcf.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -10,92 +10,125 @@ global:
|
||||
# peer: 64
|
||||
pcrf:
|
||||
freeDiameter: @sysconfdir@/freeDiameter/pcrf.conf
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.9
|
||||
port: 9090
|
||||
|
||||
################################################################################
|
||||
# Locally configured policy
|
||||
# PCRF Policy Configuration: SUPI Range Based Policies
|
||||
################################################################################
|
||||
#
|
||||
# o You don't have to use MongoDB if you use the policy configuration as below.
|
||||
# This configuration applies policies based solely on the UE's SUPI range.
|
||||
#
|
||||
# session:
|
||||
# - name: internet
|
||||
# type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
# ambr:
|
||||
# downlink:
|
||||
# value: 1
|
||||
# unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# uplink:
|
||||
# value: 1
|
||||
# unit: 3
|
||||
# qos:
|
||||
# index: 9 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# arp:
|
||||
# priority_level: 8 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
# - name: ims
|
||||
# type: 3 # 1:IPv4, 2:IPv6, 3:IPv4v6
|
||||
# ambr:
|
||||
# downlink:
|
||||
# value: 1
|
||||
# unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# uplink:
|
||||
# value: 1
|
||||
# unit: 3 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# qos:
|
||||
# index: 5 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# arp:
|
||||
# priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
# pcc_rule:
|
||||
# - qos:
|
||||
# index: 1 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# arp:
|
||||
# priority_level: 1 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2:Enabled
|
||||
# mbr:
|
||||
# downlink:
|
||||
# value: 82
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# uplink:
|
||||
# value: 82
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# gbr:
|
||||
# downlink:
|
||||
# value: 82
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# uplink:
|
||||
# value: 82
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# flow:
|
||||
# - direction: 2
|
||||
# description: "permit out icmp from any to assigned"
|
||||
# - direction: 1
|
||||
# description: "permit out icmp from any to assigned"
|
||||
# - direction: 2
|
||||
# description: "permit out udp from 10.200.136.98/32 23455 to assigned 1-65535"
|
||||
# - direction: 1
|
||||
# description: "permit out udp from 10.200.136.98/32 1-65535 to assigned 50021"
|
||||
# - qos:
|
||||
# index: 2 # 1, 2, 3, 4, 65, 66, 67, 75, 71, 72, 73, 74, 76, 5, 6, 7, 8, 9, 69, 70, 79, 80, 82, 83, 84, 85, 86
|
||||
# arp:
|
||||
# priority_level: 4 # 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
|
||||
# pre_emption_vulnerability: 2 # 1: Disabled, 2:Enabled
|
||||
# pre_emption_capability: 2 # 1: Disabled, 2:Enabled
|
||||
# mbr:
|
||||
# downlink:
|
||||
# value: 802
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# uplink:
|
||||
# value: 802
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# gbr:
|
||||
# downlink:
|
||||
# value: 802
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# uplink:
|
||||
# value: 802
|
||||
# unit: 1 # 0:bps, 1:Kbps, 2:Mbps, 3:Gbps, 4:Tbps
|
||||
# supi_range: Specifies one or more ranges of SUPIs.
|
||||
# session: Defines the session configuration for each DNN.
|
||||
#
|
||||
# Example:
|
||||
#
|
||||
# policy:
|
||||
# - supi_range: # Filter policies by SUPI
|
||||
# - 999700000000001-999709999999999
|
||||
# - 315010000000001-315010999999999
|
||||
# session: # Define session based on DNN
|
||||
# - name: internet
|
||||
# type: 3 # 1: IPv4, 2: IPv6, 3: IPv4v6
|
||||
# ambr:
|
||||
# downlink:
|
||||
# value: 1
|
||||
# unit: 3 # 0: bps, 1: Kbps, 2: Mbps, 3: Gbps, 4: Tbps
|
||||
# uplink:
|
||||
# value: 1
|
||||
# unit: 3
|
||||
# qos:
|
||||
# index: 9 # Allowed values: 1,2,3,4,65,66,67,75,71,72,
|
||||
# # 73,74,76,5,6,7,8,9,69,70,79,80,82,83,
|
||||
# # 84,85,86
|
||||
# arp:
|
||||
# priority_level: 8 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2: Enabled
|
||||
# - name: ims
|
||||
# type: 3 # 1: IPv4, 2: IPv6, 3: IPv4v6
|
||||
# ambr:
|
||||
# downlink:
|
||||
# value: 1
|
||||
# unit: 3
|
||||
# uplink:
|
||||
# value: 1
|
||||
# unit: 3
|
||||
# qos:
|
||||
# index: 5 # Allowed values as above
|
||||
# arp:
|
||||
# priority_level: 1 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2: Enabled
|
||||
# pcc_rule:
|
||||
# - qos:
|
||||
# index: 1 # Allowed values as above
|
||||
# arp:
|
||||
# priority_level: 1
|
||||
# pre_emption_vulnerability: 1
|
||||
# pre_emption_capability: 1
|
||||
# mbr:
|
||||
# downlink:
|
||||
# value: 82
|
||||
# unit: 1 # 0: bps, 1: Kbps, 2: Mbps, 3: Gbps, 4: Tbps
|
||||
# uplink:
|
||||
# value: 82
|
||||
# unit: 1
|
||||
# gbr:
|
||||
# downlink:
|
||||
# value: 82
|
||||
# unit: 1
|
||||
# uplink:
|
||||
# value: 82
|
||||
# unit: 1
|
||||
# flow:
|
||||
# - direction: 2
|
||||
# description: "permit out icmp from any to assigned"
|
||||
# - direction: 1
|
||||
# description: "permit out icmp from any to assigned"
|
||||
# - direction: 2
|
||||
# description: "permit out udp from 10.200.136.98/32 23455 to assigned 1-65535"
|
||||
# - direction: 1
|
||||
# description: "permit out udp from 10.200.136.98/32 1-65535 to assigned 50021"
|
||||
# - qos:
|
||||
# index: 2 # Allowed values as above
|
||||
# arp:
|
||||
# priority_level: 4 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 2 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 2 # 1: Disabled, 2: Enabled
|
||||
# mbr:
|
||||
# downlink:
|
||||
# value: 802
|
||||
# unit: 1
|
||||
# uplink:
|
||||
# value: 802
|
||||
# unit: 1
|
||||
# gbr:
|
||||
# downlink:
|
||||
# value: 802
|
||||
# unit: 1
|
||||
# uplink:
|
||||
# value: 802
|
||||
# unit: 1
|
||||
#
|
||||
# - supi_range: # Filter policies by SUPI only
|
||||
# - 001010000000001-001019999999999
|
||||
# session: # Define session based on DNN
|
||||
# - name: internet
|
||||
# type: 3 # 1: IPv4, 2: IPv6, 3: IPv4v6
|
||||
# ambr:
|
||||
# downlink:
|
||||
# value: 1
|
||||
# unit: 3
|
||||
# uplink:
|
||||
# value: 1
|
||||
# unit: 3
|
||||
# qos:
|
||||
# index: 9 # Allowed values as above
|
||||
# arp:
|
||||
# priority_level: 8 # Allowed values: 1 to 15
|
||||
# pre_emption_vulnerability: 1 # 1: Disabled, 2: Enabled
|
||||
# pre_emption_capability: 1 # 1: Disabled, 2: Enabled
|
||||
|
||||
@@ -63,28 +63,78 @@ scp:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-scp.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-scp.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: scp.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.200 and advertise as open5gs-scp.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.200
|
||||
# port: 7777
|
||||
# advertise: open5gs-scp.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.200
|
||||
# port: 7777
|
||||
# advertise: open5gs-scp.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
################################################################################
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect Communication by Delegating to Next-SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the Next-SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
################################################################################
|
||||
@@ -105,6 +155,27 @@ scp:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/scp.key
|
||||
# cert: @sysconfdir@/open5gs/tls/scp.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/scp-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/scp-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: scp.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -148,6 +148,36 @@ sepp:
|
||||
# uri: https://sepp2.localdomain
|
||||
# resolve: 127.0.2.251
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# private_key: @sysconfdir@/open5gs/tls/sepp1.key
|
||||
# cert: @sysconfdir@/open5gs/tls/sepp1.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/sepp1-server-sslkeylog.log
|
||||
# client:
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/sepp1-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.1.250
|
||||
# port: 7777
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# n32:
|
||||
# server:
|
||||
# - sender: sepp1.localdomain
|
||||
# scheme: https
|
||||
# address: 127.0.1.251
|
||||
# client:
|
||||
# sepp:
|
||||
# - receiver: sepp2.localdomain
|
||||
# uri: https://sepp2.localdomain
|
||||
# resolve: 127.0.2.251
|
||||
#
|
||||
# o Add client TLS verification to N32 interface
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -14,8 +14,10 @@ sepp:
|
||||
server:
|
||||
private_key: @sysconfdir@/open5gs/tls/sepp2.key
|
||||
cert: @sysconfdir@/open5gs/tls/sepp2.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/sepp2-server-sslkeylog.log
|
||||
client:
|
||||
cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/sepp2-client-sslkeylog.log
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.2.250
|
||||
@@ -148,6 +150,36 @@ sepp:
|
||||
# uri: https://sepp1.localdomain
|
||||
# resolve: 127.0.1.251
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# private_key: @sysconfdir@/open5gs/tls/sepp2.key
|
||||
# cert: @sysconfdir@/open5gs/tls/sepp2.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/sepp2-server-sslkeylog.log
|
||||
# client:
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/sepp2-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.2.250
|
||||
# port: 7777
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# n32:
|
||||
# server:
|
||||
# - sender: sepp2.localdomain
|
||||
# scheme: https
|
||||
# address: 127.0.2.251
|
||||
# client:
|
||||
# sepp:
|
||||
# - receiver: sepp1.localdomain
|
||||
# uri: https://sepp1.localdomain
|
||||
# resolve: 127.0.1.251
|
||||
#
|
||||
# o Add client TLS verification to N32 interface
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -186,43 +186,83 @@ smf:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-smf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-smf.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: smf.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.4 and advertise as open5gs-smf.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.4
|
||||
# port: 7777
|
||||
# advertise: open5gs-smf.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.4
|
||||
# port: 7777
|
||||
# advertise: open5gs-smf.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
################################################################################
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect communication with delegated discovery
|
||||
# o Indirect Communication by Delegating to SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect communication without delegated discovery
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# discovery:
|
||||
# delegated: no
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: no # Directly communicate NRF discovery
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegated Discovery
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: yes # Delegate discovery to SCP
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -244,6 +284,27 @@ smf:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/smf.key
|
||||
# cert: @sysconfdir@/open5gs/tls/smf.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/smf-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/smf-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: smf.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -38,7 +38,6 @@ udm:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
#
|
||||
################################################################################
|
||||
# Home Network Public Key
|
||||
################################################################################
|
||||
@@ -82,43 +81,83 @@ udm:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-udm.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-udm.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: udm.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.12 and advertise as open5gs-udm.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.12
|
||||
# port: 7777
|
||||
# advertise: open5gs-udm.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.12
|
||||
# port: 7777
|
||||
# advertise: open5gs-udm.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
################################################################################
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect communication with delegated discovery
|
||||
# o Indirect Communication by Delegating to SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect communication without delegated discovery
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# discovery:
|
||||
# delegated: no
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: no # Directly communicate NRF discovery
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegated Discovery
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: yes # Delegate discovery to SCP
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -140,6 +179,27 @@ udm:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/udm.key
|
||||
# cert: @sysconfdir@/open5gs/tls/udm.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/udm-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/udm-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: udm.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -23,43 +23,83 @@ udr:
|
||||
################################################################################
|
||||
# SBI Server
|
||||
################################################################################
|
||||
# o Override SBI address to be advertised to NRF
|
||||
# o Bind to the address on the eth0 and advertise as open5gs-udr.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - dev: eth0
|
||||
# - dev:eth0
|
||||
# advertise: open5gs-udr.svc.local
|
||||
#
|
||||
# o Specify a custom port number 7777 while binding to the given address
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: localhost
|
||||
# advertise:
|
||||
# - 127.0.0.99
|
||||
# - ::1
|
||||
# - address: udr.localdomain
|
||||
# port: 7777
|
||||
#
|
||||
# o Bind to 127.0.0.20 and advertise as open5gs-udr.svc.local
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.20
|
||||
# port: 7777
|
||||
# advertise: open5gs-udr.svc.local
|
||||
#
|
||||
# o Bind to port 7777 but advertise with a different port number 8888
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: 127.0.0.20
|
||||
# port: 7777
|
||||
# advertise: open5gs-udr.svc.local:8888
|
||||
#
|
||||
################################################################################
|
||||
# SBI Client
|
||||
################################################################################
|
||||
# o Direct communication with NRF interaction
|
||||
# o Direct Communication with NRF
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
#
|
||||
# o Indirect communication with delegated discovery
|
||||
# o Indirect Communication by Delegating to SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
#
|
||||
# o Indirect communication without delegated discovery
|
||||
# o Indirect Communication without Delegation
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# discovery:
|
||||
# delegated: no
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: no # Directly communicate NRF discovery
|
||||
# scp:
|
||||
# next: no # Do not delegate to SCP for next-hop
|
||||
#
|
||||
# o Indirect Communication with Delegated Discovery
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# delegated:
|
||||
# nrf:
|
||||
# nfm: no # Directly communicate NRF management functions
|
||||
# disc: yes # Delegate discovery to SCP
|
||||
# scp:
|
||||
# next: yes # Delegate to SCP for next-hop communications
|
||||
#
|
||||
# o Default delegation: all communications are delegated to the SCP
|
||||
# sbi:
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: http://127.0.0.10:7777
|
||||
# scp:
|
||||
# - uri: http://127.0.0.200:7777
|
||||
# # No 'delegated' section; defaults to AUTO delegation
|
||||
#
|
||||
################################################################################
|
||||
# HTTPS scheme with TLS
|
||||
@@ -81,6 +121,27 @@ udr:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Enable SSL key logging for Wireshark
|
||||
# - This configuration allows capturing SSL/TLS session keys
|
||||
# for debugging or analysis purposes using Wireshark.
|
||||
# default:
|
||||
# tls:
|
||||
# server:
|
||||
# scheme: https
|
||||
# private_key: @sysconfdir@/open5gs/tls/udr.key
|
||||
# cert: @sysconfdir@/open5gs/tls/udr.crt
|
||||
# sslkeylogfile: @localstatedir@/log/open5gs/tls/udr-server-sslkeylog.log
|
||||
# client:
|
||||
# scheme: https
|
||||
# cacert: @sysconfdir@/open5gs/tls/ca.crt
|
||||
# client_sslkeylogfile: @localstatedir@/log/open5gs/tls/udr-client-sslkeylog.log
|
||||
# sbi:
|
||||
# server:
|
||||
# - address: udr.localdomain
|
||||
# client:
|
||||
# nrf:
|
||||
# - uri: https://nrf.localdomain
|
||||
#
|
||||
# o Add client TLS verification
|
||||
# default:
|
||||
# tls:
|
||||
|
||||
@@ -67,7 +67,7 @@ mme:
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 901
|
||||
mnc: 70
|
||||
mnc: 70
|
||||
tac: 7
|
||||
security:
|
||||
integrity_order : [ EIA2, EIA1, EIA0 ]
|
||||
|
||||
266
configs/transfer-error-case.yaml.in
Normal file
266
configs/transfer-error-case.yaml.in
Normal file
@@ -0,0 +1,266 @@
|
||||
db_uri: mongodb://localhost/open5gs
|
||||
|
||||
logger:
|
||||
|
||||
test:
|
||||
serving:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
|
||||
global:
|
||||
parameter:
|
||||
# no_nrf: true
|
||||
no_scp: true
|
||||
no_sepp: true
|
||||
# no_amf: true
|
||||
# no_smf: true
|
||||
# no_upf: true
|
||||
# no_ausf: true
|
||||
# no_udm: true
|
||||
# no_pcf: true
|
||||
# no_nssf: true
|
||||
# no_bsf: true
|
||||
# no_udr: true
|
||||
no_mme: true
|
||||
no_sgwc: true
|
||||
no_sgwu: true
|
||||
no_pcrf: true
|
||||
no_hss: true
|
||||
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
client:
|
||||
upf:
|
||||
- address: 127.0.0.7
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
port: 9090
|
||||
session:
|
||||
- subnet: 10.45.0.0/16
|
||||
gateway: 10.45.0.1
|
||||
- subnet: 2001:db8:cafe::/48
|
||||
gateway: 2001:db8:cafe::1
|
||||
dns:
|
||||
- 8.8.8.8
|
||||
- 8.8.4.4
|
||||
- 2001:4860:4860::8888
|
||||
- 2001:4860:4860::8844
|
||||
mtu: 1400
|
||||
freeDiameter:
|
||||
identity: smf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.0.4
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: pcrf.localdomain
|
||||
address: 127.0.0.9
|
||||
|
||||
amf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
ngap:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
port: 9090
|
||||
guami:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
amf_id:
|
||||
region: 2
|
||||
set: 1
|
||||
pointer: 31
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
tac: 1
|
||||
plmn_support:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
s_nssai:
|
||||
- sst: 1
|
||||
security:
|
||||
integrity_order : [ NIA2, NIA1, NIA0 ]
|
||||
ciphering_order : [ NEA0, NEA1, NEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
amf_name: open5gs-amf0
|
||||
time:
|
||||
t3512:
|
||||
value: 540 # 9 mintues * 60 = 540 seconds
|
||||
|
||||
# amf #2
|
||||
amf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.50
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
ngap:
|
||||
server:
|
||||
- address: 127.0.0.50
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.50
|
||||
port: 9090
|
||||
guami:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
amf_id:
|
||||
region: 2
|
||||
set: 1
|
||||
pointer: 30
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
tac: 1
|
||||
plmn_support:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
s_nssai:
|
||||
- sst: 1
|
||||
security:
|
||||
integrity_order : [ NIA2, NIA1, NIA0 ]
|
||||
ciphering_order : [ NEA0, NEA1, NEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
amf_name: open5gs-amf1
|
||||
time:
|
||||
t3512:
|
||||
value: 540 # 9 mintues * 60 = 540 seconds
|
||||
|
||||
upf:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
session:
|
||||
- subnet: 10.45.0.0/16
|
||||
gateway: 10.45.0.1
|
||||
- subnet: 2001:db8:cafe::/48
|
||||
gateway: 2001:db8:cafe::1
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
port: 9090
|
||||
|
||||
nrf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.10
|
||||
port: 7777
|
||||
serving:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
|
||||
ausf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.11
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
|
||||
udm:
|
||||
hnet:
|
||||
- id: 1
|
||||
scheme: 1
|
||||
key: @build_configs_dir@/open5gs/hnet/curve25519-1.key
|
||||
- id: 2
|
||||
scheme: 2
|
||||
key: @build_configs_dir@/open5gs/hnet/secp256r1-2.key
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.12
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
|
||||
pcf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.13
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.13
|
||||
port: 9090
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.14
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
nsi:
|
||||
- uri: http://127.0.0.10:7777
|
||||
s_nssai:
|
||||
sst: 1
|
||||
bsf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.15
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.20
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
271
configs/transfer.yaml.in
Normal file
271
configs/transfer.yaml.in
Normal file
@@ -0,0 +1,271 @@
|
||||
db_uri: mongodb://localhost/open5gs
|
||||
|
||||
logger:
|
||||
|
||||
test:
|
||||
serving:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
|
||||
global:
|
||||
parameter:
|
||||
# no_nrf: true
|
||||
# no_scp: true
|
||||
no_sepp: true
|
||||
# no_amf: true
|
||||
# no_smf: true
|
||||
# no_upf: true
|
||||
# no_ausf: true
|
||||
# no_udm: true
|
||||
# no_pcf: true
|
||||
# no_nssf: true
|
||||
# no_bsf: true
|
||||
# no_udr: true
|
||||
no_mme: true
|
||||
no_sgwc: true
|
||||
no_sgwu: true
|
||||
no_pcrf: true
|
||||
no_hss: true
|
||||
|
||||
smf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
client:
|
||||
upf:
|
||||
- address: 127.0.0.7
|
||||
gtpc:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.4
|
||||
port: 9090
|
||||
session:
|
||||
- subnet: 10.45.0.0/16
|
||||
gateway: 10.45.0.1
|
||||
- subnet: 2001:db8:cafe::/48
|
||||
gateway: 2001:db8:cafe::1
|
||||
dns:
|
||||
- 8.8.8.8
|
||||
- 8.8.4.4
|
||||
- 2001:4860:4860::8888
|
||||
- 2001:4860:4860::8844
|
||||
mtu: 1400
|
||||
freeDiameter:
|
||||
identity: smf.localdomain
|
||||
realm: localdomain
|
||||
listen_on: 127.0.0.4
|
||||
no_fwd: true
|
||||
load_extension:
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dbg_msg_dumps.fdx
|
||||
conf: 0x8888
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_rfc5777.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_mip6i.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nasreq.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_nas_mipv6.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca.fdx
|
||||
- module: @build_subprojects_freeDiameter_extensions_dir@/dict_dcca_3gpp/dict_dcca_3gpp.fdx
|
||||
connect:
|
||||
- identity: pcrf.localdomain
|
||||
address: 127.0.0.9
|
||||
|
||||
amf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
ngap:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.5
|
||||
port: 9090
|
||||
guami:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
amf_id:
|
||||
region: 2
|
||||
set: 1
|
||||
pointer: 31
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
tac: 1
|
||||
plmn_support:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
s_nssai:
|
||||
- sst: 1
|
||||
security:
|
||||
integrity_order : [ NIA2, NIA1, NIA0 ]
|
||||
ciphering_order : [ NEA0, NEA1, NEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
amf_name: open5gs-amf0
|
||||
time:
|
||||
t3512:
|
||||
value: 540 # 9 mintues * 60 = 540 seconds
|
||||
|
||||
# amf #2
|
||||
amf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.50
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
ngap:
|
||||
server:
|
||||
- address: 127.0.0.50
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.50
|
||||
port: 9090
|
||||
guami:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
amf_id:
|
||||
region: 2
|
||||
set: 1
|
||||
pointer: 30
|
||||
tai:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
tac: 1
|
||||
plmn_support:
|
||||
- plmn_id:
|
||||
mcc: 999
|
||||
mnc: 70
|
||||
s_nssai:
|
||||
- sst: 1
|
||||
security:
|
||||
integrity_order : [ NIA2, NIA1, NIA0 ]
|
||||
ciphering_order : [ NEA0, NEA1, NEA2 ]
|
||||
network_name:
|
||||
full: Open5GS
|
||||
amf_name: open5gs-amf1
|
||||
time:
|
||||
t3512:
|
||||
value: 540 # 9 mintues * 60 = 540 seconds
|
||||
|
||||
upf:
|
||||
pfcp:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
gtpu:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
session:
|
||||
- subnet: 10.45.0.0/16
|
||||
gateway: 10.45.0.1
|
||||
- subnet: 2001:db8:cafe::/48
|
||||
gateway: 2001:db8:cafe::1
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.7
|
||||
port: 9090
|
||||
|
||||
nrf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.10
|
||||
port: 7777
|
||||
|
||||
scp:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.200
|
||||
port: 7777
|
||||
client:
|
||||
nrf:
|
||||
- uri: http://127.0.0.10:7777
|
||||
|
||||
ausf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.11
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
udm:
|
||||
hnet:
|
||||
- id: 1
|
||||
scheme: 1
|
||||
key: @build_configs_dir@/open5gs/hnet/curve25519-1.key
|
||||
- id: 2
|
||||
scheme: 2
|
||||
key: @build_configs_dir@/open5gs/hnet/secp256r1-2.key
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.12
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
pcf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.13
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
metrics:
|
||||
server:
|
||||
- address: 127.0.0.13
|
||||
port: 9090
|
||||
|
||||
nssf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.14
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
nsi:
|
||||
- uri: http://127.0.0.10:7777
|
||||
s_nssai:
|
||||
sst: 1
|
||||
bsf:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.15
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
|
||||
udr:
|
||||
sbi:
|
||||
server:
|
||||
- address: 127.0.0.20
|
||||
port: 7777
|
||||
client:
|
||||
scp:
|
||||
- uri: http://127.0.0.200:7777
|
||||
108
debian/changelog
vendored
108
debian/changelog
vendored
@@ -1,3 +1,111 @@
|
||||
open5gs (2.7.6) unstable; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sat, 19 Jul 2025 10:02:38 +0900
|
||||
|
||||
open5gs (2.7.6~plucky) plucky; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sat, 19 Jul 2025 09:59:50 +0900
|
||||
|
||||
open5gs (2.7.6~oracular) oracular; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sat, 19 Jul 2025 09:57:14 +0900
|
||||
|
||||
open5gs (2.7.6~noble) noble; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sat, 19 Jul 2025 09:55:32 +0900
|
||||
|
||||
open5gs (2.7.6~jammy) jammy; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sat, 19 Jul 2025 09:53:39 +0900
|
||||
|
||||
open5gs (2.7.6~focal) focal; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sat, 19 Jul 2025 09:51:57 +0900
|
||||
|
||||
open5gs (2.7.6~bionic) bionic; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sat, 19 Jul 2025 09:49:35 +0900
|
||||
|
||||
open5gs (2.7.5) unstable; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 30 Mar 2025 22:01:17 +0900
|
||||
|
||||
open5gs (2.7.5~oracular) oracular; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 30 Mar 2025 22:00:22 +0900
|
||||
|
||||
open5gs (2.7.5~noble) noble; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 30 Mar 2025 21:59:27 +0900
|
||||
|
||||
open5gs (2.7.5~jammy) jammy; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 30 Mar 2025 21:58:02 +0900
|
||||
|
||||
open5gs (2.7.5~focal) focal; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 30 Mar 2025 21:56:59 +0900
|
||||
|
||||
open5gs (2.7.5~bionic) bionic; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 30 Mar 2025 21:55:48 +0900
|
||||
|
||||
open5gs (2.7.2) unstable; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 04 Aug 2024 21:03:45 +0900
|
||||
|
||||
open5gs (2.7.2~jammy1) jammy; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 04 Aug 2024 21:02:06 +0900
|
||||
|
||||
open5gs (2.7.2~focal1) focal; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 04 Aug 2024 21:00:24 +0900
|
||||
|
||||
open5gs (2.7.2~noble1) noble; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 04 Aug 2024 20:58:44 +0900
|
||||
|
||||
open5gs (2.7.2~bionic1) bionic; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
-- Sukchan Lee <acetcom@gmail.com> Sun, 04 Aug 2024 20:56:49 +0900
|
||||
|
||||
open5gs (2.7.1) unstable; urgency=medium
|
||||
|
||||
* Bug Fixed
|
||||
|
||||
2
debian/control
vendored
2
debian/control
vendored
@@ -13,7 +13,7 @@ Build-Depends: debhelper (>= 11),
|
||||
libgnutls28-dev,
|
||||
libgcrypt-dev,
|
||||
libssl-dev,
|
||||
libidn11-dev,
|
||||
libidn-dev | libidn11-dev,
|
||||
libmongoc-dev,
|
||||
libbson-dev,
|
||||
libsctp-dev,
|
||||
|
||||
2
debian/open5gs-common.dirs
vendored
2
debian/open5gs-common.dirs
vendored
@@ -1 +1 @@
|
||||
var/log/open5gs
|
||||
var/log/open5gs/tls
|
||||
|
||||
@@ -13,7 +13,7 @@ RUN apk update && \
|
||||
sudo
|
||||
|
||||
ARG username=acetcom
|
||||
RUN adduser -u 1000 acetcom -D && \
|
||||
RUN adduser -u 2000 acetcom -D && \
|
||||
echo "${username} ALL=(root) NOPASSWD:ALL" > /etc/sudoers.d/${username} && \
|
||||
chmod 0440 /etc/sudoers.d/${username}
|
||||
|
||||
|
||||
@@ -22,7 +22,6 @@ RUN apt-get update && \
|
||||
libgnutls28-dev \
|
||||
libgcrypt-dev \
|
||||
libssl-dev \
|
||||
libidn11-dev \
|
||||
libmongoc-dev \
|
||||
libbson-dev \
|
||||
libyaml-dev \
|
||||
@@ -35,4 +34,9 @@ RUN apt-get update && \
|
||||
ca-certificates \
|
||||
netbase \
|
||||
pkg-config && \
|
||||
apt-get clean
|
||||
if apt-cache show libidn-dev > /dev/null 2>&1; then \
|
||||
apt-get install -y --no-install-recommends libidn-dev; \
|
||||
else \
|
||||
apt-get install -y --no-install-recommends libidn11-dev; \
|
||||
fi && \
|
||||
apt-get clean && rm -rf /var/lib/apt/lists/*
|
||||
|
||||
@@ -27,7 +27,7 @@ RUN apt-get update && \
|
||||
COPY setup.sh /root
|
||||
|
||||
ARG username=acetcom
|
||||
RUN useradd -m --uid=1000 ${username} && \
|
||||
RUN useradd -m --uid=2000 ${username} && \
|
||||
echo "${username} ALL=(root) NOPASSWD:ALL" > /etc/sudoers.d/${username} && \
|
||||
chmod 0440 /etc/sudoers.d/${username}
|
||||
|
||||
|
||||
@@ -16,7 +16,7 @@ RUN dnf -y install \
|
||||
COPY setup.sh /root
|
||||
|
||||
ARG username=acetcom
|
||||
RUN useradd -m --uid=1000 ${username} && \
|
||||
RUN useradd -m --uid=2000 ${username} && \
|
||||
echo "${username} ALL=(root) NOPASSWD:ALL" > /etc/sudoers.d/${username} && \
|
||||
chmod 0440 /etc/sudoers.d/${username}
|
||||
|
||||
|
||||
@@ -22,7 +22,6 @@ RUN apt-get update && \
|
||||
libgnutls28-dev \
|
||||
libgcrypt-dev \
|
||||
libssl-dev \
|
||||
libidn11-dev \
|
||||
libmongoc-dev \
|
||||
libbson-dev \
|
||||
libyaml-dev \
|
||||
@@ -35,4 +34,9 @@ RUN apt-get update && \
|
||||
ca-certificates \
|
||||
netbase \
|
||||
pkg-config && \
|
||||
apt-get clean
|
||||
if apt-cache show libidn-dev > /dev/null 2>&1; then \
|
||||
apt-get install -y --no-install-recommends libidn-dev; \
|
||||
else \
|
||||
apt-get install -y --no-install-recommends libidn11-dev; \
|
||||
fi && \
|
||||
apt-get clean && rm -rf /var/lib/apt/lists/*
|
||||
|
||||
@@ -33,7 +33,7 @@ RUN apt-get update && \
|
||||
COPY setup.sh /root
|
||||
|
||||
ARG username=acetcom
|
||||
RUN useradd -m --uid=1000 ${username} && \
|
||||
RUN useradd -m --uid=2000 ${username} && \
|
||||
echo "${username} ALL=(root) NOPASSWD:ALL" > /etc/sudoers.d/${username} && \
|
||||
chmod 0440 /etc/sudoers.d/${username}
|
||||
|
||||
|
||||
@@ -26,6 +26,9 @@ google_analytics: G-12MQZTB3JH
|
||||
|
||||
# Build settings
|
||||
markdown: kramdown
|
||||
kramdown:
|
||||
parse_block_html: true
|
||||
|
||||
plugins:
|
||||
- jekyll-feed
|
||||
- jekyll-seo-tag
|
||||
|
||||
@@ -80,14 +80,14 @@ Import the public key used by the package management system.
|
||||
```bash
|
||||
$ sudo apt update
|
||||
$ sudo apt install gnupg
|
||||
$ curl -fsSL https://pgp.mongodb.com/server-6.0.asc | sudo gpg -o /usr/share/keyrings/mongodb-server-6.0.gpg --dearmor
|
||||
$ curl -fsSL https://pgp.mongodb.com/server-8.0.asc | sudo gpg -o /usr/share/keyrings/mongodb-server-8.0.gpg --dearmor
|
||||
```
|
||||
|
||||
Create the list file /etc/apt/sources.list.d/mongodb-org-6.0.list for your version of Ubuntu.
|
||||
Create the list file /etc/apt/sources.list.d/mongodb-org-8.0.list for your version of Ubuntu.
|
||||
|
||||
On ubuntu 22.04 (Jammy)
|
||||
```bash
|
||||
$ echo "deb [ arch=amd64,arm64 signed-by=/usr/share/keyrings/mongodb-server-6.0.gpg] https://repo.mongodb.org/apt/ubuntu jammy/mongodb-org/6.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-6.0.list
|
||||
$ echo "deb [ arch=amd64,arm64 signed-by=/usr/share/keyrings/mongodb-server-8.0.gpg] https://repo.mongodb.org/apt/ubuntu jammy/mongodb-org/8.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-8.0.list
|
||||
```
|
||||
|
||||
Install the MongoDB packages.
|
||||
|
||||
@@ -18,14 +18,14 @@ Import the public key used by the package management system.
|
||||
```bash
|
||||
$ sudo apt update
|
||||
$ sudo apt install gnupg
|
||||
$ curl -fsSL https://pgp.mongodb.com/server-6.0.asc | sudo gpg -o /usr/share/keyrings/mongodb-server-6.0.gpg --dearmor
|
||||
$ curl -fsSL https://pgp.mongodb.com/server-8.0.asc | sudo gpg -o /usr/share/keyrings/mongodb-server-8.0.gpg --dearmor
|
||||
```
|
||||
|
||||
Create the list file /etc/apt/sources.list.d/mongodb-org-6.0.list for your version of Ubuntu.
|
||||
Create the list file /etc/apt/sources.list.d/mongodb-org-8.0.list for your version of Ubuntu.
|
||||
|
||||
On ubuntu 22.04 (Jammy)
|
||||
```bash
|
||||
$ echo "deb [ arch=amd64,arm64 signed-by=/usr/share/keyrings/mongodb-server-6.0.gpg] https://repo.mongodb.org/apt/ubuntu jammy/mongodb-org/6.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-6.0.list
|
||||
$ echo "deb [ arch=amd64,arm64 signed-by=/usr/share/keyrings/mongodb-server-8.0.gpg] https://repo.mongodb.org/apt/ubuntu jammy/mongodb-org/8.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-8.0.list
|
||||
```
|
||||
|
||||
Install the MongoDB packages.
|
||||
@@ -58,10 +58,19 @@ $ sudo ip link set ogstun up
|
||||
### Building Open5GS
|
||||
---
|
||||
|
||||
Install the dependencies for building the source code.
|
||||
Install the common dependencies for building the source code.
|
||||
|
||||
```bash
|
||||
$ sudo apt install python3-pip python3-setuptools python3-wheel ninja-build build-essential flex bison git cmake libsctp-dev libgnutls28-dev libgcrypt-dev libssl-dev libidn11-dev libmongoc-dev libbson-dev libyaml-dev libnghttp2-dev libmicrohttpd-dev libcurl4-gnutls-dev libnghttp2-dev libtins-dev libtalloc-dev meson
|
||||
$ sudo apt install python3-pip python3-setuptools python3-wheel ninja-build build-essential flex bison git cmake libsctp-dev libgnutls28-dev libgcrypt-dev libssl-dev libmongoc-dev libbson-dev libyaml-dev libnghttp2-dev libmicrohttpd-dev libcurl4-gnutls-dev libnghttp2-dev libtins-dev libtalloc-dev meson
|
||||
```
|
||||
|
||||
Install libidn-dev or libidn11-dev depending on your system
|
||||
```bash
|
||||
$ if apt-cache show libidn-dev > /dev/null 2>&1; then
|
||||
sudo apt-get install -y --no-install-recommends libidn-dev
|
||||
else
|
||||
sudo apt-get install -y --no-install-recommends libidn11-dev
|
||||
fi
|
||||
```
|
||||
|
||||
Git clone.
|
||||
@@ -447,7 +456,7 @@ $ cp open5gs* /usr/bin/
|
||||
For convenience, you can execute all NFs at once by using the following command.
|
||||
```bash
|
||||
$ ./build/tests/app/5gc ## 5G Core Only with ./build/configs/sample.yaml
|
||||
$ ./build/tests/app/epc -c ./build/configs/srslte.yaml ## EPC Only with ./build/configs/srslte.yaml
|
||||
$ ./build/tests/app/epc -c ./build/configs/srsenb.yaml ## EPC Only with ./build/configs/srsenb.yaml
|
||||
$ ./build/tests/app/app ## Both 5G Core and EPC with ./build/configs/sample.yaml
|
||||
```
|
||||
|
||||
|
||||
@@ -19,12 +19,15 @@ If you have tested radio hardware from a vendor not listed with Open5GS, please
|
||||
* CableFree Small Cell Indoor radios (5G n77, n78 and other bands)
|
||||
* CableFree Macro (BBU+RRH) radios (4G and 5G, various bands)
|
||||
* Ericsson Baseband 6630 (21.Q3 Software) + Radio 2217, Radio 2219 (4G and 5G, various bands)
|
||||
* Ericsson Baseband 6648/6651 IRU 8848 Dots 4475 (N78, N1,N3)
|
||||
* Ericsson StreetMacro 6701 (21.Q3 Software) (5G mmWave, n261) (Baseband 6318 and AIR 1281 packaged together)
|
||||
* Huawei BTS5900
|
||||
* Huawei BTS5900 V100R019C10SPC220 (N78, N28)
|
||||
* LIONS RANathon O-CU and O-DU + RANathon RS8601 Indoor O-RU + RANathon XG8600 Fronthaul Gateway
|
||||
* NOKIA AEQE (SW: 5G20A)
|
||||
* NOKIA AEQD (SW: 5G20A)
|
||||
* NOKIA AEQP (SW: 5G21A)
|
||||
* MOSO Networks Canopy 5GID1 Indoor 2T2R (5G n48 n78)
|
||||
* ZTE ITBBU ITRAN-PNF V5.65.20.20F10 (n78, n1, n3)
|
||||
|
||||
### Commercial 4G
|
||||
---
|
||||
@@ -42,10 +45,12 @@ If you have tested radio hardware from a vendor not listed with Open5GS, please
|
||||
* Baicells Nova 436Q
|
||||
* Baicells Nova 227 (EBS & CBRS)
|
||||
* Baicells Nova 233
|
||||
* Ericsson Baseband 6630 (21Q1 Software)
|
||||
* Baicells Nova 430i (band 48/CBRS, SW version BaiBLQ_3.0.12)
|
||||
* Ericsson Baseband 6630/6648/6651 (21Q1 Software)
|
||||
* Ericsson RBS 6402 (18.Q1 software, B2 B25 B4 B7 B252 B255)
|
||||
* Ericsson RBS 6601 + DUL 20 01 + RUS 01 B8
|
||||
* Gemtek WLTGFC-101 (S/W version 2.1.1746.1116)
|
||||
* Gemtek WLTGFC-105 (band 3, SW version 2.1.2277.1720-wltgfc105-gemtek-fdd)
|
||||
* Huawei BTS3900 (S/W version V100R011C10SPC230)
|
||||
* Huawei BBU5900 with RRU5304W Band 7 FDD 2600Mhz 40W Version V100R016C10
|
||||
* Klas VoyagerCell Duo 4GAP1000/4GAP1000X
|
||||
@@ -55,7 +60,11 @@ If you have tested radio hardware from a vendor not listed with Open5GS, please
|
||||
* Nokia FW2FA Flexi Zone Mini-Macro Outdoor BTS, 2x20w Band 39
|
||||
* Nokia FWGR Flexi Zone Mini-Macro Outdoor BTS, 2x20w Band 1
|
||||
* Nokia FWHG Flexi Zone Indoor Pico BTS, 2x250 mW Band 7
|
||||
* Nokia FW2HHD Flexi Zone Multiband Indoor Pico BTS, Band 38/41(S/W TLS18SP_ENB)
|
||||
* Mikrotik Intercell B1+B3 IC322GC-b1D+b3D
|
||||
* Ruckus Q710 and Q910
|
||||
* Sercomm SCE4255W "Englewood" (band 48/CBRS, SW version DG3934v3@2308041842)
|
||||
* ZTE ITBBU ITRAN-PNF V5.65.20.20F10
|
||||
|
||||
### 4G/5G Software Stacks + SDRs
|
||||
---
|
||||
@@ -63,9 +72,11 @@ If you have tested radio hardware from a vendor not listed with Open5GS, please
|
||||
* [Amarisoft](https://www.amarisoft.com/) + LimeSDR, USRP, Amarisoft PCI Express Card
|
||||
* Open Air Interface 5G ([NR_SA_F1AP_5GRECORDS branch](https://gitlab.eurecom.fr/oai/openairinterface5g/-/tree/NR_SA_F1AP_5GRECORDS)) + USRP B210
|
||||
* [srsLTE / srsENB](https://github.com/srsLTE/srsLTE) + LimeSDR, USRP, BladeRF x40 (BladeRF Not stable)
|
||||
* [srsRAN_Project](https://github.com/srsran/srsRAN_Project) 5G O-RAN CU/DU based on USRP SDR.
|
||||
|
||||
### Misc Radio Hardware
|
||||
---
|
||||
* [OpenAirInterface v1.0.3](https://gitlab.eurecom.fr/oai/openairinterface5g/-/tree/v1.0.3) 4G RAN Simulator
|
||||
* [OsmoBTS](https://osmocom.org/projects/osmobts/wiki) controlled ip.access NanoBTS (Used for CSFB with Osmocom)
|
||||
* [UERANSIM](https://github.com/aligungr/UERANSIM) 5G RAN Simulator
|
||||
* [PacketRusher](https://github.com/HewlettPackard/PacketRusher) 5G performance testing and validation tool
|
||||
|
||||
@@ -3,10 +3,10 @@ title: FreeBSD
|
||||
head_inline: "<style> .blue { color: blue; } </style>"
|
||||
---
|
||||
|
||||
This guide is based on **FreeBSD-13.1-STABLE**.
|
||||
This guide is based on **FreeBSD-14.1-STABLE**.
|
||||
{: .blue}
|
||||
|
||||
## Install **FreeBSD-13.1-STABLE** from Vagrant box (optional)
|
||||
## Install **FreeBSD-14.1-STABLE** from Vagrant box (optional)
|
||||
---
|
||||
Vagrant provides a simple way to create and deploy Virtual Machines from
|
||||
pre-built images using VirtualBox, libvirt, or VMWare as a hypervisor engine.
|
||||
@@ -20,13 +20,13 @@ The instructions to install Vagrant are provided at
|
||||
[vagrantup.com](https://www.vagrantup.com/).
|
||||
|
||||
|
||||
### Create a FreeBSD-13.1-STABLE Virtual Machine using Vagrant
|
||||
### Create a FreeBSD-14.1-STABLE Virtual Machine using Vagrant
|
||||
---
|
||||
|
||||
Use the supplied `Vagrantfile` in the `vagrant` directory to create the
|
||||
virtual machine.
|
||||
|
||||
Note that this Vagrantfile is identical to the base FreeBSD 13 box, with
|
||||
Note that this Vagrantfile is identical to the base FreeBSD 14 box, with
|
||||
the exception that the amount of virtual memory has been increased to 1GB:
|
||||
|
||||
```bash
|
||||
@@ -37,7 +37,7 @@ vagrant up --provider virtualbox
|
||||
### Log into the newly created FreeBSD VM
|
||||
---
|
||||
|
||||
Use SSH to log into the FreeBSD 13 VM:
|
||||
Use SSH to log into the FreeBSD 14 VM:
|
||||
|
||||
```bash
|
||||
vagrant ssh
|
||||
@@ -45,10 +45,10 @@ vagrant ssh
|
||||
|
||||
Note that the Open5GS source is *not* copied into the VM. The instructions
|
||||
below provide the step by step instructions for setting up Open5GS for
|
||||
either a bare metal or virtual FreeBSD 13 system.
|
||||
either a bare metal or virtual FreeBSD 14 system.
|
||||
|
||||
The rest of the commands below are performed inside the FreeBSD VM as the
|
||||
user 'vagrant', or on your bare metal FreeBSD 13 system as any normal user.
|
||||
user 'vagrant', or on your bare metal FreeBSD 14 system as any normal user.
|
||||
|
||||
### Getting MongoDB
|
||||
---
|
||||
@@ -171,7 +171,7 @@ $ meson build --prefix=`pwd`/install
|
||||
$ ninja -C build
|
||||
```
|
||||
|
||||
**Note:** No source code changes are required for FreeBSD 11.x version. However, in FreeBSD 12.x/13.x version, we'll getting a crash with segmentation fault when calling basename(3). To avoid this, you need to change the freeDiameter source code as below.
|
||||
**Note:** No source code changes are required for FreeBSD 11.x version. However, in FreeBSD 12.x/13.x/14.x version, we'll getting a crash with segmentation fault when calling basename(3). To avoid this, you need to change the freeDiameter source code as below.
|
||||
{: .blue}
|
||||
|
||||
```diff
|
||||
|
||||
@@ -1356,7 +1356,7 @@ $ DIST=debian TAG=stretch docker-compose run dev
|
||||
```bash
|
||||
$ sudo dpkg --add-architecture armel
|
||||
$ sudo apt update
|
||||
$ sudo apt install libsctp-dev:armel libyaml-dev:armel libgnutls28-dev:armel libgcrypt-dev:armel libidn11-dev:armel libssl-dev:armel libmongoc-dev:armel libbson-dev:armel
|
||||
$ sudo apt install libsctp-dev:armel libyaml-dev:armel libgnutls28-dev:armel libgcrypt-dev:armel libidn-dev:armel libssl-dev:armel libmongoc-dev:armel libbson-dev:armel
|
||||
$ sudo apt install crossbuild-essential-armel
|
||||
$ sudo apt install qemu
|
||||
$ git clone https://github.com/{{ site.github_username }}/open5gs
|
||||
|
||||
@@ -165,8 +165,8 @@ $ make test
|
||||
The Open5GS package is available on the recent versions of *Ubuntu*.
|
||||
```bash
|
||||
# Install the MongoDB Packages
|
||||
$ curl -fsSL https://pgp.mongodb.com/server-6.0.asc | sudo gpg -o /usr/share/keyrings/mongodb-server-6.0.gpg --dearmor
|
||||
$ echo "deb [ arch=amd64,arm64 signed-by=/usr/share/keyrings/mongodb-server-6.0.gpg] https://repo.mongodb.org/apt/ubuntu jammy/mongodb-org/6.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-6.0.list
|
||||
$ curl -fsSL https://pgp.mongodb.com/server-8.0.asc | sudo gpg -o /usr/share/keyrings/mongodb-server-8.0.gpg --dearmor
|
||||
$ echo "deb [ arch=amd64,arm64 signed-by=/usr/share/keyrings/mongodb-server-8.0.gpg] https://repo.mongodb.org/apt/ubuntu jammy/mongodb-org/8.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-8.0.list
|
||||
$ sudo apt update
|
||||
$ sudo apt install mongodb-org
|
||||
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
478
docs/_docs/tutorial/06-Open5GS-with-5G-Sharp-Orchestrator.md
Normal file
478
docs/_docs/tutorial/06-Open5GS-with-5G-Sharp-Orchestrator.md
Normal file
@@ -0,0 +1,478 @@
|
||||
---
|
||||
title: Open5GS with 5G Sharp Orchestrator
|
||||
---
|
||||
|
||||
This tutorial is a guide to configure the tool 5G Sharp Orchestrator with Open5GS.
|
||||
|
||||
5G Sharp Orchestrator is a tool that serves as a comprehensive wrapper for configuring, deploying and monitoring 5G open-source network components, simplifying the orchestration process.
|
||||
|
||||
For more information on 5G Sharp Orchestrator please visit: https://github.com/Ethon-Shield/5g-sharp-orchestrator
|
||||
|
||||
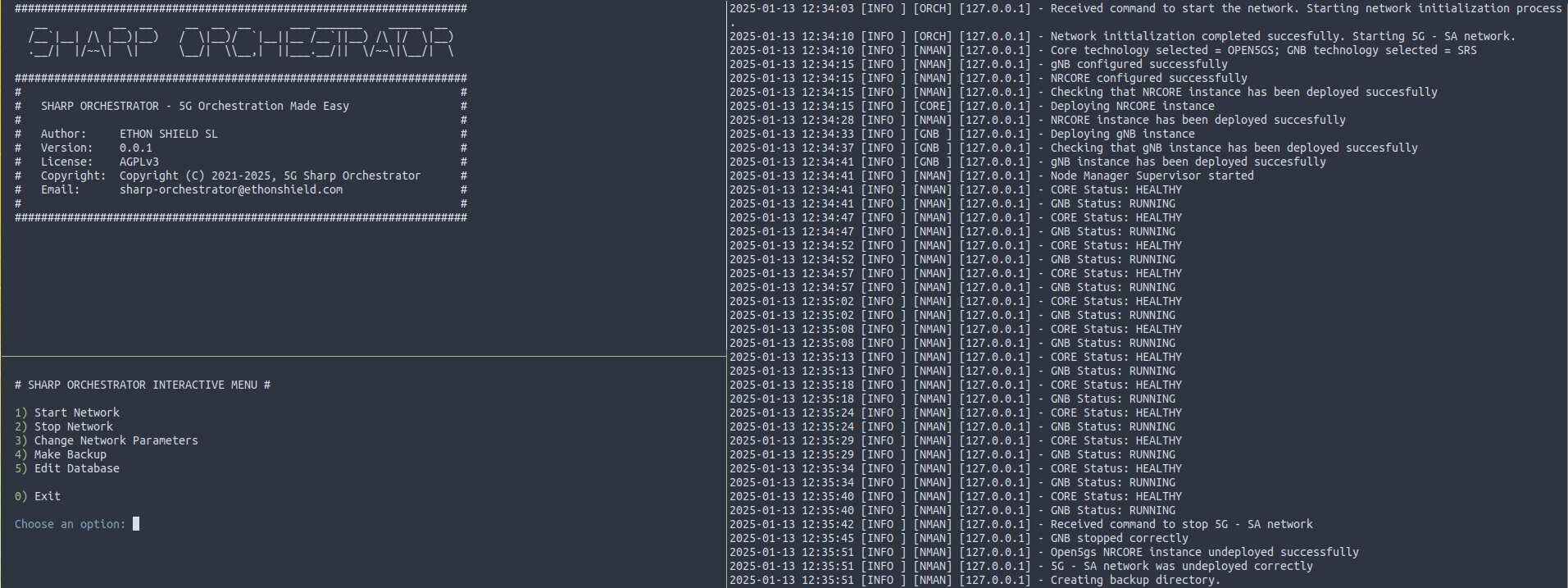
|
||||
|
||||
|
||||
# Usage
|
||||
|
||||
To correctly execute the 5G Sharp Orchestrator with Open5GS you will need to:
|
||||
|
||||
**0. Install prerequisites**
|
||||
**1. Configure the project**
|
||||
**2. Check the configuration is valid**
|
||||
**3. Execute the tool**
|
||||
|
||||
This tutorial has been described with the following setup:
|
||||
- Physical machine:
|
||||
- i7 processor
|
||||
- Ubuntu 22.04 LTS
|
||||
- User "test"
|
||||
- Connectivity - Offline
|
||||
- Open5GS cloned and compiled in /home/test/open5gs
|
||||
- srsRAN cloned and compiled in /home/test/srsRAN_Project
|
||||
- Network parameters:
|
||||
- MCC: 001
|
||||
- MNC: 01
|
||||
- TAC: 1
|
||||
- SDR device:
|
||||
- Ettus B200 mini
|
||||
|
||||
## 0. Install prerequisites
|
||||
|
||||
To be able to use the 5G Sharp Orchestrator tool, you will need to meet the following prerequisites.
|
||||
|
||||
<details>
|
||||
<summary><strong>Software prerequisites</strong></summary>
|
||||
|
||||
This project needs certain binaries to be installed.
|
||||
|
||||
- The project has been successfully tested with **Ubuntu 22.04**
|
||||
- UHD built from source (https://files.ettus.com/manual/page_build_guide.html)
|
||||
- docker **version 19.03.0 or higher** (https://docs.docker.com/engine/install/ubuntu/)
|
||||
```
|
||||
# User going to be used should be in the docker group
|
||||
sudo usermod -aG docker <user>
|
||||
newgrp docker
|
||||
```
|
||||
- docker-compose **version 1.29.2 or higher** (https://docs.docker.com/compose/install/linux/)
|
||||
- tmux **version 3.5a** (https://github.com/tmux/tmux/releases)
|
||||
|
||||
```bash
|
||||
wget https://github.com/tmux/tmux/releases/download/3.5a/tmux-3.5a.tar.gz
|
||||
tar -zxf tmux-3.5a.tar.gz
|
||||
cd tmux-3.5a
|
||||
./configure
|
||||
make
|
||||
sudo make install
|
||||
```
|
||||
|
||||
- wireshark, tshark, expect
|
||||
|
||||
```bash
|
||||
sudo add-apt-repository ppa:wireshark-dev/stable
|
||||
sudo apt update
|
||||
sudo apt install wireshark tshark expect
|
||||
```
|
||||
|
||||
</details>
|
||||
<details>
|
||||
<summary><strong>Install Open5GS Core</strong></summary>
|
||||
|
||||
Official documentation: https://open5gs.org/open5gs/docs/guide/02-building-open5gs-from-sources/
|
||||
|
||||
To work with Open5GS core, it is recommended to build the project from source.
|
||||
|
||||
**1. Getting MongoDB**
|
||||
|
||||
- Install GNU Privacy Guard tool:
|
||||
|
||||
```
|
||||
sudo apt update
|
||||
sudo apt install gnupg
|
||||
```
|
||||
|
||||
- Import the public key used by the package management system:
|
||||
|
||||
```
|
||||
curl -fsSL https://pgp.mongodb.com/server-7.0.asc | sudo gpg -o /usr/share/keyrings/mongodb-server-7.0.gpg --dearmor
|
||||
|
||||
echo "deb [ arch=amd64,arm64 signed-by=/usr/share/keyrings/mongodb-server-7.0.gpg ] https://repo.mongodb.org/apt/ubuntu jammy/mongodb-org/7.0 multiverse" | sudo tee /etc/apt/sources.list.d/mongodb-org-7.0.list
|
||||
```
|
||||
|
||||
- Install the MongoDB packages:
|
||||
```
|
||||
sudo apt update
|
||||
sudo apt install -y mongodb-org
|
||||
```
|
||||
|
||||
**NOTE**: MongoDB service needs to be running in order to execute the project. This can be done using the command ``sudo systemctl start mongod ``
|
||||
|
||||
**2. Building Open5GS**
|
||||
|
||||
Install the required dependencies:
|
||||
|
||||
```
|
||||
sudo apt install python3-pip python3-setuptools python3-wheel ninja-build build-essential flex bison git cmake libsctp-dev libgnutls28-dev libgcrypt-dev libssl-dev libidn11-dev libmongoc-dev libbson-dev libyaml-dev libnghttp2-dev libmicrohttpd-dev libcurl4-gnutls-dev libnghttp2-dev libtins-dev libtalloc-dev meson
|
||||
```
|
||||
Clone the official project repository:
|
||||
```
|
||||
git clone https://github.com/open5gs/open5gs
|
||||
```
|
||||
Compile with <i>meson</i> and build with <i>ninja</i>:
|
||||
```
|
||||
cd open5gs/ meson build --prefix=`pwd`/install
|
||||
ninja -C build
|
||||
```
|
||||
Check wether the compilation is correct:
|
||||
```
|
||||
./build/tests/registration/registration
|
||||
```
|
||||
Run all test programs:
|
||||
```
|
||||
cd build
|
||||
sudo meson test -v
|
||||
```
|
||||
Perform the installation process:
|
||||
```
|
||||
cd build
|
||||
ninja install
|
||||
cd ../
|
||||
```
|
||||
</details>
|
||||
|
||||
<details>
|
||||
<summary><strong>Install srsRAN gNB</strong></summary>
|
||||
|
||||
Official documentation: https://docs.srsran.com/projects/project/en/latest/user_manuals/source/installation.html
|
||||
|
||||
**1. Installing build tools and dependencies**
|
||||
|
||||
The required build tools and dependencies for the project can be installed in Ubuntu using the following command:
|
||||
```
|
||||
sudo apt-get install cmake make gcc g++ pkg-config libfftw3-dev libmbedtls-dev libsctp-dev libyaml-cpp-dev libgtest-devg
|
||||
```
|
||||
|
||||
**2. Clone and build**
|
||||
|
||||
Clone the project repository:
|
||||
```
|
||||
git clone https://github.com/srsRAN/srsRAN_Project.git
|
||||
```
|
||||
|
||||
Build the code-base:
|
||||
```
|
||||
cd srsRAN_Project
|
||||
mkdir build
|
||||
cd build
|
||||
cmake ../
|
||||
make -j $(nproc)
|
||||
make test -j $(nproc)
|
||||
sudo make install
|
||||
```
|
||||
</details>
|
||||
|
||||
<details>
|
||||
<summary><strong>Hardware prerequisites</strong></summary>
|
||||
|
||||
|
||||
- USRP devices.
|
||||
- USB 3.0 port to connect the SDR.
|
||||
- It is recommended to at least have an i7 processor.
|
||||
|
||||
</details>
|
||||
|
||||
|
||||
## 1. Configuring the project
|
||||
|
||||
Once the prerequisites have been fullfilled, the next step is to setup the 5G Sharp Orchestrator. First of all, clone the repository:
|
||||
|
||||
```
|
||||
cd ~/
|
||||
git clone https://github.com/Ethon-Shield/5g-sharp-orchestrator.git
|
||||
```
|
||||
|
||||
To configure the 5G Sharp Orchestrator with Open5GS you will need to modify the corresponding parameters in the file `./conf/sharp-orchestrator.src` . In this file you will be able to set different network parameters such as the MCC, MNC or TAC, encryption and integrity alogrithms, as well as defining the file paths of the corresponding binaries.
|
||||
|
||||
The following variables are set based on the example setup described at the start of the tutorial.
|
||||
|
||||
**SHARP ORCHESTRATOR**:
|
||||
- **SHARP_ORCHESTRATOR_IP_ADDRESS**=127.0.0.1
|
||||
- **SHARP_ORCHESTRATOR_USERNAME**="test"
|
||||
- **SHARP_ORCHESTRATOR_WORKING_DIR**="/home/test/5g-sharp-orhcestrator/"
|
||||
|
||||
**GENERAL**:
|
||||
|
||||
- **MCC**=001
|
||||
- **MNC**=01
|
||||
- **TAC**=1
|
||||
- **DEBUG**="false"
|
||||
- **DNS_IP_ADDRESS**="8.8.8.8"
|
||||
- **DEPLOY_NRCORE_ONLY**="false"
|
||||
- **BACKUP_DIR_PREFIX**=""
|
||||
|
||||
**NRCORE**:
|
||||
|
||||
- **NRCORE_TECH**=OPEN5GS
|
||||
- **INT_ALGO_PRIORITY_LIST**=NIA1,NIA2,NIA0
|
||||
- **CIPH_ALGO_PRIORITY_LIST**=NEA1,NEA2,NEA0
|
||||
- **NRCORE_OPEN5GS_WD**="/home/test/open5gs"
|
||||
|
||||
**GNB**:
|
||||
|
||||
- **GNB_TECH**=SRS
|
||||
- **GNB_IP_ADDRESS**=127.0.0.1
|
||||
- **GNB_USERNAME**="test"
|
||||
- **GNB_WORKING_DIR**="/home/test/Desktop/gnb"
|
||||
- **ARFCN**="641280"
|
||||
- **SRS_GNB_BIN**="/home/test/srsRAN_Project/build/apps/gnb/gnb"
|
||||
- **BAND**="78"
|
||||
- **CHANNEL_BW**="20"
|
||||
- **SCS**="15"
|
||||
|
||||
### SUDOERS file
|
||||
|
||||
It will be necessary to modify /etc/.sudoers file (via visudo for example) in order to be able to execute certain commands that need root privileges:
|
||||
|
||||
```bash
|
||||
test ALL=(ALL) NOPASSWD: \
|
||||
/usr/bin/kill -9 *, \
|
||||
/usr/bin/chown -R * /tmp, \
|
||||
/usr/bin/chown -R * /logs, \
|
||||
/usr/sbin/ip tuntap add name ogstun mode tun, \
|
||||
/usr/sbin/ip addr del 10.45.0.1/16 dev ogstun, \
|
||||
/usr/sbin/ip addr add 10.45.0.1/16 dev ogstun, \
|
||||
/usr/sbin/ip addr del 2001\:db8\:cafe\:\:1/48 dev ogstun, \
|
||||
/usr/sbin/ip addr add 2001\:db8\:cafe\:\:1/48 dev ogstun, \
|
||||
/usr/sbin/ip link set ogstun up, \
|
||||
/usr/sbin/sysctl net.ipv4.conf.all.forwarding=1, \
|
||||
/usr/sbin/iptables -P FORWARD ACCEPT, \
|
||||
/usr/sbin/iptables -S, \
|
||||
/usr/sbin/ip route del *, \
|
||||
/usr/sbin/ip route add *, \
|
||||
/usr/bin/unbuffer *, \
|
||||
/usr/bin/kill -9 *
|
||||
```
|
||||
|
||||
### SSH KEYS
|
||||
|
||||
Furthermore, although in this example setup we are only using one physical machine, the nodes will talk to each other via ssh. Consequently, it is important to store the public ssh key of the corresponding user.
|
||||
|
||||
1. Generate ssh key pair: `ssh-key-gen -t rsa`
|
||||
2. Copy public pair into remote machine (in this example setup - localhost): `ssh-copy-id -i ~/.ssh/id_rsa.pub test@127.0.0.1`
|
||||
|
||||
|
||||
## 2. Checking the configuation is valid
|
||||
|
||||
Once the project has been configured accordingly, check if it has been correctly configured executing the next script: `./bin/check_conf.sh`. All checks should have a **YES**.
|
||||
|
||||
<details>
|
||||
<summary><strong> Example output </strong></summary>
|
||||
|
||||
```
|
||||
##################################
|
||||
Checking basic variables
|
||||
##################################
|
||||
BASIC variables are OK
|
||||
|
||||
##################################
|
||||
Checking necessary binaries
|
||||
##################################
|
||||
tshark ... YES
|
||||
expect ... YES
|
||||
tmux ... YES
|
||||
uhd_find_devices ... YES
|
||||
uhd_usrp_probe ... YES
|
||||
open5gs-nrfd ... YES
|
||||
open5gs-scpd ... YES
|
||||
open5gs-amfd ... YES
|
||||
open5gs-smfd ... YES
|
||||
open5gs-upfd ... YES
|
||||
open5gs-ausfd ... YES
|
||||
open5gs-udmd ... YES
|
||||
open5gs-pcfd ... YES
|
||||
open5gs-nssfd ... YES
|
||||
open5gs-bsfd ... YES
|
||||
open5gs-udrd ... YES
|
||||
|
||||
##################################
|
||||
Checking CORE IP address, username and working dir
|
||||
##################################
|
||||
|
||||
CORE IP ADDRESS ... YES
|
||||
CORE USERNAME ... YES
|
||||
CORE WORKING DIR ... YES
|
||||
|
||||
Checking if open5gs services are active
|
||||
|
||||
MongoDB is running ... YES
|
||||
|
||||
##################################
|
||||
Checking SSH connections
|
||||
##################################
|
||||
|
||||
CORE --> GNB ... YES
|
||||
GNB --> CORE ... YES
|
||||
|
||||
##################################
|
||||
Checking necessary repositories & binaries
|
||||
##################################
|
||||
|
||||
OPEN5GS CORE
|
||||
/home/test/open5gs/ directory ... YES
|
||||
NOTES:
|
||||
- /home/test/open5gs/ in TAG v2.7.2-65-g6d80d4322
|
||||
gNB
|
||||
SRS gnb bin ... YES
|
||||
|
||||
##################################
|
||||
Checking sudoers file
|
||||
##################################
|
||||
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/bin/kill -9 \* ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/bin/chown -R \* /tmp ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/bin/chown -R \* /logs ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/ip tuntap add name ogstun mode tun ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/ip addr del 10.45.0.1/16 dev ogstun ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/ip addr add 10.45.0.1/16 dev ogstun ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/ip addr del 2001\:db8\:cafe\:\:1/48 dev ogstun ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/ip addr add 2001\:db8\:cafe\:\:1/48 dev ogstun ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/ip link set ogstun up ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/sysctl net.ipv4.conf.all.forwarding\=1 ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/iptables -P FORWARD ACCEPT ... YES
|
||||
NOPASSWD in ORCH & CORE for test for command /usr/sbin/iptables -S ... YES
|
||||
NOPASSWD in GNB for test for command /usr/sbin/ip route del \* in GNB ... YES
|
||||
NOPASSWD in GNB for test for command /usr/sbin/ip route add \* in GNB ... YES
|
||||
NOPASSWD in GNB for test for command /usr/bin/unbuffer \* in GNB ... YES
|
||||
NOPASSWD in GNB for test for command /usr/bin/kill -9 \* in GNB ... YES
|
||||
|
||||
##################################
|
||||
Checking sharp-orchestrator.src parameters
|
||||
##################################
|
||||
|
||||
MCC 001 ... YES
|
||||
MNC 01 ... YES
|
||||
DEBUG false ... YES
|
||||
DEPLOY_NRCORE_ONLY false ... YES
|
||||
DNS_IP_ADDRESS 8.8.8.8 ... YES
|
||||
AMF_IP_ADDRESS 127.0.0.100 ... YES
|
||||
SHARP_ORCHESTRATOR_IP_ADDRESS 127.0.0.1 ... YES
|
||||
NRCORE_IP_ADDRESS 127.0.0.1 ... YES
|
||||
GNB_IP_ADDRESS 127.0.0.1 ... YES
|
||||
|
||||
##################################
|
||||
Checking gNB directory
|
||||
##################################
|
||||
|
||||
GNB directory ... YES
|
||||
```
|
||||
|
||||
</details>
|
||||
|
||||
## 3. Executing the tool
|
||||
|
||||
After checking the configuration file and setting every paramater correctly, you will be able to start the orchestration process.
|
||||
|
||||
##### STARTING THE ORCHESTRATOR APP
|
||||
|
||||
To start the orchestrator app execute the following command:
|
||||
```bash
|
||||
./tui.sh
|
||||
```
|
||||
|
||||
You will have an interactive menu to perform all the needed actions.
|
||||
|
||||
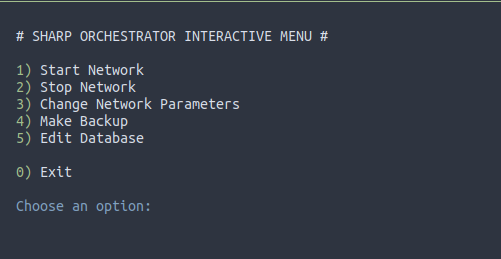
|
||||
|
||||
##### STARTING THE NETWORK
|
||||
|
||||
Choose the "Start network" option in the interactive menu --> "1"
|
||||
|
||||
##### STOPPING THE NETWORK
|
||||
|
||||
Choose the "Stop network" option in the interactive menu --> "2"
|
||||
|
||||
##### UPDATE GNB PARAMETERS ON REAL-TIME
|
||||
|
||||
Some parameters in the gNB can be updated on real-time. This is done to prevent the undeployment of the core network and slowing the whole process.
|
||||
|
||||
The current supported parameters for the srs gNB to be updated are:
|
||||
- ARFCN
|
||||
- BAND
|
||||
- CHANNEL_BW
|
||||
- SCS
|
||||
|
||||
Choose the "Change network parameters" option in the interactive menu --> "3"
|
||||
|
||||
This will show a sub menu with the different options:
|
||||
- Setting the different parameters
|
||||
- Updating them
|
||||
|
||||
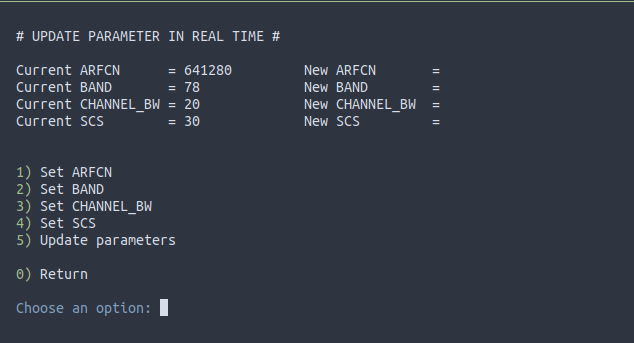
|
||||
|
||||
Before updating any parameter, you need to set the value. For that, choose the corresponding "set" option and the value to set will be asked.
|
||||
The new set value will appear in the menu, as it is shown in the images below
|
||||
|
||||
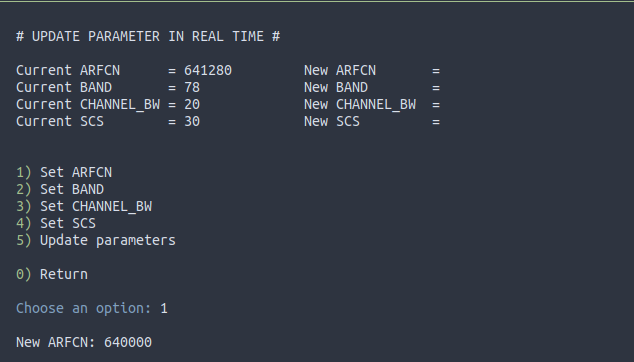
|
||||
|
||||
|
||||
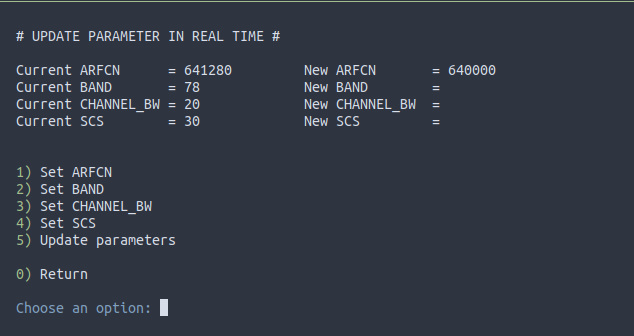
|
||||
|
||||
|
||||
After setting all the values you want to update, choose the "Update parameters" option in the interactive menu for the changes to take place.
|
||||
This action will stop the running gNB instance and start a new one with the updated parameters.
|
||||
Any error in the gNB execution due to invalid parameters selection will be prompted in the log screen.
|
||||
|
||||
|
||||
##### BACKING UP FILES DURING EXECUTION
|
||||
|
||||
Stopping the network will automatically perform a backup. This options is used if you want to perform a backup during the execution without stopping the network.
|
||||
The backup will be saved in the sharp-orchestrator/backups directory.
|
||||
|
||||
Making a backup will save the following files:
|
||||
```
|
||||
├── logs -> DIR that includes all the logs from the network nodes
|
||||
├── pcaps -> DIR that includes all the pcaps from the network nodes
|
||||
├── conf -> DIR that includes the latest configuration files of the network nodes
|
||||
└── sharp_orchestrator.log -> Orchestration log
|
||||
```
|
||||
|
||||
Choose the "Make backup" option in the interactive menu --> "4"
|
||||
|
||||
##### MANAGE SUBSCRIBERS IN DATABASE
|
||||
|
||||
To be able to connect subscribers to the deployed network they need to be provisioned in the corresponding databases.
|
||||
|
||||
Choose the "Edit Database" option in the interactive menu --> "5"
|
||||
|
||||
This will show a sub menu with the different options:
|
||||
- Setting the different parameters (IMSI, KI, OPC)
|
||||
- Adding a subscriber to the database - needed parameters: IMSI, KI, OPC
|
||||
- Updating a subscriber in the database - needed parameters: IMSI, KI, OPC
|
||||
- Removing a subscriber from the database - needed parameters: IMSI
|
||||
|
||||
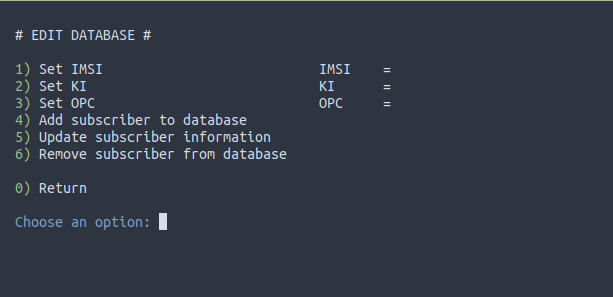
|
||||
|
||||
|
||||
Before performing an action to a subscriber, you need to add the required information. For that set the different parameters.
|
||||
|
||||
The next image shows an example of setting the IMSI:
|
||||
|
||||
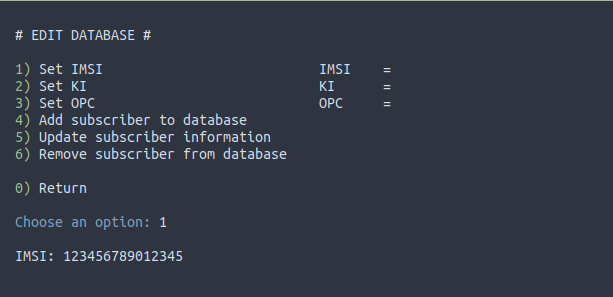
|
||||
|
||||
|
||||
After setting the IMSI, you would be able to remove it from the database, by chossing the option "Remove subscriber from the database" --> 6
|
||||
|
||||
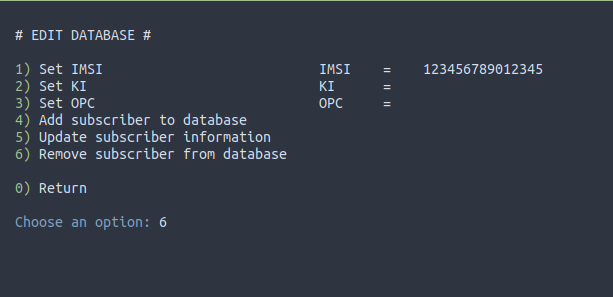
|
||||
|
||||
|
||||
</details>
|
||||
|
||||
# More configuration options
|
||||
|
||||
- If you only want to deploy the Open5GS nrcore network without the radio node, set the DEPLOY_NRCORE_ONLY variable to "true"
|
||||
|
||||
|
||||
# Viewing PCAP files
|
||||
|
||||
- Go to Analyze --> Enabled Protocols --> check the box mac_nr and mac_nr_udp
|
||||
- Sometimes, when debugging the PCAP files, the traffic is encrypted using EEA0. To view this traffic, in Wireshark go to Edit -> Preferences -> Protocols -> NAS-5GS -> check box "Try to detect and decode 5G-EA0 ciphered message"
|
||||
|
||||
|
||||
@@ -20,7 +20,7 @@ head_inline: "<style> ul { padding-bottom: 1em; } </style>"
|
||||
|
||||
- In the lab
|
||||
- [A Demonstration of 30 Gbps Load Testing for Accelerated UPF with Open5gs](https://nextepc.com/technology)
|
||||
- [Measurement of UPF Performance](https://github.com/s5uishida/simple_measurement_of_upf_performance)
|
||||
- [Measurement of UPF Performance](https://github.com/s5uishida/sample_config_misc_for_mobile_network#performance_measurement)
|
||||
|
||||
- Troubleshooting
|
||||
- [Simple Issues](troubleshoot/01-simple-issues)
|
||||
@@ -43,12 +43,14 @@ head_inline: "<style> ul { padding-bottom: 1em; } </style>"
|
||||
- [SMF Code Explanation](https://medium.com/@aditya.koranga/open5gs-smf-code-explanation-with-flow-charts-a3b3cd38c991)
|
||||
|
||||
- @infinitydon
|
||||
- [OAI's O-RAN Integration With Open5gs 5G Core](https://futuredon.medium.com/integrating-disaggregated-openairinterface-o-ran-components-with-open5gs-5g-core-76e5deac1730)
|
||||
- [Open5GS on Amazon Elastic Kubernetes Service](https://aws.amazon.com/blogs/opensource/open-source-mobile-core-network-implementation-on-amazon-elastic-kubernetes-service/)
|
||||
- [Kubernetes Open5GS Deployment](https://dev.to/infinitydon/virtual-4g-simulation-using-kubernetes-and-gns3-3b7k?fbclid=IwAR1p99h13a-mCfejanbBQe0H0-jp5grXkn5mWf1WrTHf47UtegB2-UHGGZQ)
|
||||
- [5G Core SBI mTLS Using External Certificate PKI](https://futuredon.medium.com/5g-core-sbi-mtls-using-external-certificate-pki-4ffc02ac7728)
|
||||
- [5G Frame Routing](https://futuredon.medium.com/5g-frame-routing-6e34d8587123)
|
||||
- [5G SCTP LoadBalancer Using LoxiLB](https://futuredon.medium.com/5g-sctp-loadbalancer-using-loxilb-b525198a9103)([Video Link](https://youtu.be/k3ICc7MXcC8))
|
||||
- [5G Roaming With Mutual TLS](https://futuredon.medium.com/5g-roaming-with-mutual-tls-1468d109129c)
|
||||
- [Building a Cloud-Native 5G Roaming Architecture with Open5GS](https://futuredon.medium.com/building-a-cloud-native-5g-roaming-architecture-with-open5gs-cert-manager-and-openbao-supporting-08168a937ddc)
|
||||
|
||||
- @nickvsnetworking
|
||||
- [My first 5G Core : Open5GS and UERANSIM](http://nickvsnetworking.com/my-first-5g-core-open5gs-and-ueransim/)
|
||||
@@ -75,8 +77,14 @@ head_inline: "<style> ul { padding-bottom: 1em; } </style>"
|
||||
- [srsRAN with eUPF(eBPF/XDP UPF)](https://github.com/s5uishida/open5gs_epc_srsran_eupf_sample_config)
|
||||
|
||||
- @gradiant helm charts
|
||||
- [Open5GS EPC and SRS LTE in kubernetes](https://gradiant.github.io/openverso-charts/open5gs-srslte.html)
|
||||
- [Open5GS NGC and UERANSIM in kubernetes](https://gradiant.github.io/openverso-charts/open5gs-ueransim-gnb.html)
|
||||
- [Open5GS NGC and OpenAirInterface GNB with ettus USRP in kubernetes](https://gradiant.github.io/openverso-charts/open5gs-oaignb.html)
|
||||
- [Open5GS EPC and SRS ENB with ettus USRP in kubernetes](https://gradiant.github.io/openverso-charts/open5gs-srsenb.html)
|
||||
- [Open5GS with Service Communication Proxy in kubernetes](https://gradiant.github.io/openverso-charts/open5gs-scp.html)
|
||||
- [Open5GS and srsRAN-5G in kubernetes](https://gradiant.github.io/5g-charts/open5gs-srsran-5g-zmq.html)
|
||||
- [Open5GS and srsLTE in kubernetes](https://gradiant.github.io/5g-charts/open5gs-srslte.html)
|
||||
- [Open5GS and UERANSIM](https://gradiant.github.io/5g-charts/open5gs-ueransim-gnb.html)
|
||||
- [Open5GS and PacketRusher](https://gradiant.github.io/5g-charts/open5gs-packetrusher.html)
|
||||
- [Open5GS and OAI-GNB](https://gradiant.github.io/5g-charts/open5gs-oaignb.html)
|
||||
- [Open5GS and srsenb](https://gradiant.github.io/5g-charts/open5gs-srsenb.html)
|
||||
- [Open5GS with SCP(Service Communication Proxy](https://gradiant.github.io/5g-charts/open5gs-scp.html)
|
||||
|
||||
- @loxilb
|
||||
- [Exploring 5G SCP with Open5GS and LoxiLB](https://dev.to/nikhilmalik/5g-service-communication-proxy-with-loxilb-4242)
|
||||
- [NGAP Load Balancing with Open5GS and LoxiLB](https://www.loxilb.io/post/ngap-load-balancing-with-loxilb)
|
||||
|
||||
@@ -5,18 +5,18 @@ subject: Support
|
||||
permalink: /support/
|
||||
---
|
||||
|
||||
###### Updated Sep, 2022
|
||||
Open5GS receives strong and ongoing support from [NewPlane Inc.](https://newplane.io), which proudly backs the project and contributes to its continuous development and success.
|
||||
|
||||
### Open5GS Licensing
|
||||
### Licensing Options:
|
||||
|
||||
Open5GS is licensed under a dual licensing model designed to meet the development and distribution needs of both commercial and open source projects.
|
||||
- **Commercial License**: Available for those who wish to develop and distribute their software without adhering to open-source license requirements. This option allows for full utilization of Open5GS capabilities and involves a strategic partnership with NewPlane. For more information, reach out to NewPlane at
|
||||
[sales@newplane.io](mailto:sales@newplane.io).
|
||||
|
||||
The commercial Open5GS license gives you the full rights to create and distribute software on your own terms without any open source license obligations. You can grow with Open5GS by establishing a close strategic relationship with [NeoPlane](https://neoplane.io).
|
||||
- **AGPL-3.0 License**: Ideal for open-source projects, academic research, and internal use where compliance with AGPL-3.0 is feasible. This license supports the open-source ethos and is suitable for a wide range of uses. If you have concerns about AGPL compliance, consider the commercial licensing option instead.
|
||||
|
||||
### Support and Customization:
|
||||
|
||||
Open5GS is also available under AGPL-3.0 open source licenses. The Open5GS open source licensing is ideal for use cases such as open source projects with open source distribution, student/academic purposes, hobby projects, internal research projects without external distribution, or other projects where all AGPL-3.0 obligations can be met.
|
||||
|
||||
If your legal department has policies regarding use of software licensed under the AGPL, you may prefer to have a commercial license. Contact [Sukchan Lee \<sales@neoplane.io\>](mailto:sales@neoplane.io) for more information on commercial licenses.
|
||||
NewPlane offers comprehensive support and customization services to enhance your experience with Open5GS. Their team is equipped to assist with troubleshooting, address specific issues, and implement customized solutions. For support and customization inquiries, please contact NewPlane at [support@newplane.io](mailto:support@newplane.io).
|
||||
|
||||
### Our Partners
|
||||
|
||||
|
||||
15
docs/_posts/2024-04-19-release-v2.7.1.md
Normal file
15
docs/_posts/2024-04-19-release-v2.7.1.md
Normal file
@@ -0,0 +1,15 @@
|
||||
---
|
||||
title: "v2.7.1 - Bug Fixed"
|
||||
date: 2024-04-19 21:23:00 +0900
|
||||
categories:
|
||||
- Release
|
||||
tags:
|
||||
- News
|
||||
- Release
|
||||
head_inline: "<style> ul { padding-bottom: 1em; } .blue { color: blue; }</style>"
|
||||
---
|
||||
|
||||
See [Release Note](https://github.com/open5gs/open5gs/releases/tag/v2.7.1)
|
||||
|
||||
Download -- [v2.7.1.tar.gz](https://github.com/open5gs/open5gs/archive/v2.7.1.tar.gz)
|
||||
{: .notice--info}
|
||||
15
docs/_posts/2024-08-04-release-v2.7.2.md
Normal file
15
docs/_posts/2024-08-04-release-v2.7.2.md
Normal file
@@ -0,0 +1,15 @@
|
||||
---
|
||||
title: "v2.7.2 - ogs_pool_cycle() removed"
|
||||
date: 2024-08-04 21:13:00 +0900
|
||||
categories:
|
||||
- Release
|
||||
tags:
|
||||
- News
|
||||
- Release
|
||||
head_inline: "<style> ul { padding-bottom: 1em; } .blue { color: blue; }</style>"
|
||||
---
|
||||
|
||||
See [Release Note](https://github.com/open5gs/open5gs/releases/tag/v2.7.2)
|
||||
|
||||
Download -- [v2.7.2.tar.gz](https://github.com/open5gs/open5gs/archive/v2.7.2.tar.gz)
|
||||
{: .notice--info}
|
||||
50
docs/_posts/2025-03-30-release-v2.7.5.md
Normal file
50
docs/_posts/2025-03-30-release-v2.7.5.md
Normal file
@@ -0,0 +1,50 @@
|
||||
---
|
||||
title: "v2.7.5 - Bug fixed"
|
||||
date: 2025-03-30 22:05:00 +0900
|
||||
categories:
|
||||
- Release
|
||||
tags:
|
||||
- News
|
||||
- Release
|
||||
head_inline: "<style> ul { padding-bottom: 1em; } .blue { color: blue; }</style>"
|
||||
---
|
||||
|
||||
# Open5GS Release Note Summary
|
||||
|
||||
This release introduces numerous improvements and bug fixes across core network components, enhancing overall stability, performance, and security. Below is a concise overview of the key updates:
|
||||
|
||||
## Session & Subscription Management
|
||||
- **SMF Enhancements:**
|
||||
Improved handling of SDM subscriptions to UDM during the PDU session lifetime.
|
||||
- **Optional PLMN-ID:**
|
||||
Added support for an optional PLMN-ID parameter in SDM GET queries (AMF/SMF).
|
||||
- **5GMM Cause Reporting:**
|
||||
AMF now sends a 5GMM cause in the request to SMF when initiating a session release.
|
||||
|
||||
## Mobility & Authentication Improvements
|
||||
- **Mobility Fixes:**
|
||||
Corrected QoS values for 2G to 4G mobility and fixed issues with UE context release and cell reselection.
|
||||
- **Security & Authentication:**
|
||||
Enhanced UE authentication processes, prevented crashes during security mode command failures, and implemented HSS selection improvements.
|
||||
|
||||
## Interface & Protocol Enhancements
|
||||
- **Diameter & PFCP:**
|
||||
- Integrated statistics into the main loop for Diameter interfaces, with enhanced debug logging for HSS and PCRF.
|
||||
- Addressed multiple PFCP issues, including memory management, header handling, and correct TEID restoration.
|
||||
- **NAS Module:**
|
||||
Fixed a heap-buffer overflow vulnerability in NAS message decoding.
|
||||
|
||||
## SBI and Other Module Updates
|
||||
- **SBI Enhancements:**
|
||||
Enabled custom User-Agent header information for HTTP/2 requests, support for custom port numbers, and direct NRF communication.
|
||||
- **Additional Fixes:**
|
||||
- Resolved UE context handling issues during handovers and state transitions.
|
||||
- Implemented various cosmetic fixes, typo corrections, and documentation updates.
|
||||
- Introduced support for new parameters and refined subscription conditions.
|
||||
|
||||
Overall, this release emphasizes improved network reliability, enhanced security measures, and better support for 5G core operations while also addressing legacy issues.
|
||||
|
||||
See [Release Note](https://github.com/open5gs/open5gs/releases/tag/v2.7.5)
|
||||
|
||||
Download -- [v2.7.5.tar.gz](https://github.com/open5gs/open5gs/archive/v2.7.5.tar.gz)
|
||||
{: .notice--info}
|
||||
15
docs/_posts/2025-07-19-release-v2.7.6.md
Normal file
15
docs/_posts/2025-07-19-release-v2.7.6.md
Normal file
@@ -0,0 +1,15 @@
|
||||
---
|
||||
title: "v2.7.6 - Bug fixed"
|
||||
date: 2025-07-19 22:05:00 +0900
|
||||
categories:
|
||||
- Release
|
||||
tags:
|
||||
- News
|
||||
- Release
|
||||
head_inline: "<style> ul { padding-bottom: 1em; } .blue { color: blue; }</style>"
|
||||
---
|
||||
|
||||
See [Release Note](https://github.com/open5gs/open5gs/releases/tag/v2.7.6)
|
||||
|
||||
Download -- [v2.7.6.tar.gz](https://github.com/open5gs/open5gs/archive/v2.7.6.tar.gz)
|
||||
{: .notice--info}
|
||||
BIN
docs/assets/pcapng/5g-roaming-hr.pcapng
Normal file
BIN
docs/assets/pcapng/5g-roaming-hr.pcapng
Normal file
Binary file not shown.
@@ -60,8 +60,8 @@ void ogs_app_config_final(void)
|
||||
|
||||
static void recalculate_pool_size(void)
|
||||
{
|
||||
ogs_app()->pool.packet =
|
||||
global_conf.max.ue * OGS_MAX_NUM_OF_PACKET_BUFFER;
|
||||
ogs_app()->pool.gtpu =
|
||||
global_conf.max.ue * OGS_MAX_NUM_OF_GTPU_BUFFER;
|
||||
|
||||
#define MAX_NUM_OF_TUNNEL 3 /* Num of Tunnel per Bearer */
|
||||
ogs_app()->pool.sess = global_conf.max.ue * OGS_MAX_NUM_OF_SESS;
|
||||
@@ -105,7 +105,7 @@ ogs_app_local_conf_t *ogs_local_conf(void)
|
||||
return &local_conf;
|
||||
}
|
||||
|
||||
static int global_conf_prepare(void)
|
||||
int ogs_app_global_conf_prepare(void)
|
||||
{
|
||||
global_conf.sockopt.no_delay = true;
|
||||
|
||||
@@ -134,6 +134,30 @@ static int global_conf_validation(void)
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
int ogs_app_count_nf_conf_sections(const char *conf_section)
|
||||
{
|
||||
if (!strcmp(conf_section, "amf"))
|
||||
global_conf.parameter.amf_count++;
|
||||
else if (!strcmp(conf_section, "smf"))
|
||||
global_conf.parameter.smf_count++;
|
||||
else if (!strcmp(conf_section, "upf"))
|
||||
global_conf.parameter.upf_count++;
|
||||
else if (!strcmp(conf_section, "ausf"))
|
||||
global_conf.parameter.ausf_count++;
|
||||
else if (!strcmp(conf_section, "udm"))
|
||||
global_conf.parameter.udm_count++;
|
||||
else if (!strcmp(conf_section, "pcf"))
|
||||
global_conf.parameter.pcf_count++;
|
||||
else if (!strcmp(conf_section, "nssf"))
|
||||
global_conf.parameter.nssf_count++;
|
||||
else if (!strcmp(conf_section, "bsf"))
|
||||
global_conf.parameter.bsf_count++;
|
||||
else if (!strcmp(conf_section, "udr"))
|
||||
global_conf.parameter.udr_count++;
|
||||
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
int ogs_app_parse_global_conf(ogs_yaml_iter_t *parent)
|
||||
{
|
||||
int rv;
|
||||
@@ -141,9 +165,6 @@ int ogs_app_parse_global_conf(ogs_yaml_iter_t *parent)
|
||||
|
||||
ogs_assert(parent);
|
||||
|
||||
rv = global_conf_prepare();
|
||||
if (rv != OGS_OK) return rv;
|
||||
|
||||
ogs_yaml_iter_recurse(parent, &global_iter);
|
||||
while (ogs_yaml_iter_next(&global_iter)) {
|
||||
const char *global_key = ogs_yaml_iter_key(&global_iter);
|
||||
@@ -226,6 +247,12 @@ int ogs_app_parse_global_conf(ogs_yaml_iter_t *parent)
|
||||
} else if (!strcmp(parameter_key, "use_openair")) {
|
||||
global_conf.parameter.use_openair =
|
||||
ogs_yaml_iter_bool(¶meter_iter);
|
||||
} else if (!strcmp(parameter_key, "use_upg_vpp")) {
|
||||
global_conf.parameter.use_upg_vpp =
|
||||
ogs_yaml_iter_bool(¶meter_iter);
|
||||
} else if (!strcmp(parameter_key, "fake_csfb")) {
|
||||
global_conf.parameter.fake_csfb =
|
||||
ogs_yaml_iter_bool(¶meter_iter);
|
||||
} else if (!strcmp(parameter_key,
|
||||
"no_ipv4v6_local_addr_in_packet_filter")) {
|
||||
global_conf.parameter.
|
||||
@@ -408,8 +435,8 @@ static int local_conf_prepare(void)
|
||||
* Heartbeat Interval(e.g: 10 seconds) + No Heartbeat Margin(1 second) */
|
||||
local_conf.time.nf_instance.no_heartbeat_margin = 1;
|
||||
|
||||
/* 3600 seconds = 1 hour */
|
||||
local_conf.time.nf_instance.validity_duration = 3600;
|
||||
/* 30 seconds */
|
||||
local_conf.time.nf_instance.validity_duration = 30;
|
||||
|
||||
/* 86400 seconds = 1 day */
|
||||
local_conf.time.subscription.validity_duration = 86400;
|
||||
@@ -459,6 +486,7 @@ int ogs_app_parse_local_conf(const char *local)
|
||||
int rv;
|
||||
yaml_document_t *document = NULL;
|
||||
ogs_yaml_iter_t root_iter;
|
||||
int idx = 0;
|
||||
|
||||
document = ogs_app()->document;
|
||||
ogs_assert(document);
|
||||
@@ -470,7 +498,8 @@ int ogs_app_parse_local_conf(const char *local)
|
||||
while (ogs_yaml_iter_next(&root_iter)) {
|
||||
const char *root_key = ogs_yaml_iter_key(&root_iter);
|
||||
ogs_assert(root_key);
|
||||
if (!strcmp(root_key, local)) {
|
||||
if (!strcmp(root_key, local) &&
|
||||
(idx++ == ogs_app()->config_section_id)) {
|
||||
ogs_yaml_iter_t local_iter;
|
||||
ogs_yaml_iter_recurse(&root_iter, &local_iter);
|
||||
while (ogs_yaml_iter_next(&local_iter)) {
|
||||
@@ -724,9 +753,83 @@ int ogs_app_parse_sockopt_config(
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
/*----------------------------------------------------------------------
|
||||
* Function: ogs_app_parse_supi_range_conf
|
||||
*
|
||||
* Parse the supi_range configuration from a YAML iterator.
|
||||
*
|
||||
* The expected YAML format is:
|
||||
*
|
||||
* supi_range:
|
||||
* - 999700000000001-999700000099999
|
||||
* - 310789000000005-310789000000888
|
||||
*
|
||||
* Both start and end must be provided.
|
||||
*
|
||||
* Returns:
|
||||
* OGS_OK on success, OGS_ERROR on failure.
|
||||
*----------------------------------------------------------------------*/
|
||||
int ogs_app_parse_supi_range_conf(
|
||||
ogs_yaml_iter_t *parent, ogs_supi_range_t *supi_range)
|
||||
{
|
||||
ogs_yaml_iter_t range_iter;
|
||||
|
||||
ogs_assert(parent);
|
||||
ogs_assert(supi_range);
|
||||
|
||||
memset(supi_range, 0, sizeof(ogs_supi_range_t));
|
||||
|
||||
/* Recurse into the supi_range array node */
|
||||
ogs_yaml_iter_recurse(parent, &range_iter);
|
||||
ogs_assert(ogs_yaml_iter_type(&range_iter) != YAML_MAPPING_NODE);
|
||||
|
||||
do {
|
||||
char *v = NULL;
|
||||
char *start_str = NULL, *end_str = NULL;
|
||||
|
||||
if (ogs_yaml_iter_type(&range_iter) == YAML_SEQUENCE_NODE) {
|
||||
if (!ogs_yaml_iter_next(&range_iter))
|
||||
break;
|
||||
}
|
||||
|
||||
v = (char *)ogs_yaml_iter_value(&range_iter);
|
||||
|
||||
if (v) {
|
||||
ogs_assert(supi_range->num < OGS_MAX_NUM_OF_SUPI_RANGE);
|
||||
|
||||
/* Split the string on '-' */
|
||||
start_str = strsep(&v, "-");
|
||||
if (start_str == NULL || strlen(start_str) == 0) {
|
||||
ogs_error("Invalid supi_range starter bound: %s", v);
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
end_str = v;
|
||||
if (end_str == NULL || strlen(end_str) == 0) {
|
||||
ogs_error("Invalid supi_range upper bound: %s", v);
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
supi_range->start[supi_range->num] =
|
||||
ogs_uint64_from_string_decimal(start_str);
|
||||
supi_range->end[supi_range->num] =
|
||||
ogs_uint64_from_string_decimal(end_str);
|
||||
|
||||
supi_range->num++;
|
||||
}
|
||||
|
||||
} while (ogs_yaml_iter_type(&range_iter) == YAML_SEQUENCE_NODE);
|
||||
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
static int parse_br_conf(ogs_yaml_iter_t *parent, ogs_bitrate_t *br)
|
||||
{
|
||||
ogs_yaml_iter_t br_iter;
|
||||
|
||||
ogs_assert(parent);
|
||||
ogs_assert(br);
|
||||
|
||||
ogs_yaml_iter_recurse(parent, &br_iter);
|
||||
|
||||
while (ogs_yaml_iter_next(&br_iter)) {
|
||||
@@ -1162,11 +1265,12 @@ int ogs_app_parse_session_conf(
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
ogs_app_policy_conf_t *ogs_app_policy_conf_add(ogs_plmn_id_t *plmn_id)
|
||||
ogs_app_policy_conf_t *ogs_app_policy_conf_add(
|
||||
ogs_supi_range_t *supi_range, ogs_plmn_id_t *plmn_id)
|
||||
{
|
||||
ogs_app_policy_conf_t *policy_conf = NULL;
|
||||
|
||||
ogs_assert(plmn_id);
|
||||
ogs_assert(supi_range || plmn_id);
|
||||
|
||||
ogs_pool_alloc(&policy_conf_pool, &policy_conf);
|
||||
if (!policy_conf) {
|
||||
@@ -1176,7 +1280,25 @@ ogs_app_policy_conf_t *ogs_app_policy_conf_add(ogs_plmn_id_t *plmn_id)
|
||||
}
|
||||
memset(policy_conf, 0, sizeof *policy_conf);
|
||||
|
||||
memcpy(&policy_conf->plmn_id, plmn_id, sizeof(ogs_plmn_id_t));
|
||||
if (supi_range) {
|
||||
int i;
|
||||
|
||||
memcpy(&policy_conf->supi_range, supi_range, sizeof(ogs_supi_range_t));
|
||||
|
||||
ogs_info("SUPI[%d]", policy_conf->supi_range.num);
|
||||
for (i = 0; i < policy_conf->supi_range.num; i++)
|
||||
ogs_info(" START[%lld]-END[%lld]",
|
||||
(long long)policy_conf->supi_range.start[i],
|
||||
(long long)policy_conf->supi_range.end[i]);
|
||||
|
||||
}
|
||||
if (plmn_id) {
|
||||
policy_conf->plmn_id_valid = true;
|
||||
memcpy(&policy_conf->plmn_id, plmn_id, sizeof(ogs_plmn_id_t));
|
||||
ogs_info("PLMN_ID[MCC:%03d.MNC:%03d]",
|
||||
ogs_plmn_id_mcc(&policy_conf->plmn_id),
|
||||
ogs_plmn_id_mnc(&policy_conf->plmn_id));
|
||||
}
|
||||
|
||||
ogs_list_init(&policy_conf->slice_list);
|
||||
|
||||
@@ -1187,19 +1309,60 @@ ogs_app_policy_conf_t *ogs_app_policy_conf_add(ogs_plmn_id_t *plmn_id)
|
||||
return policy_conf;
|
||||
}
|
||||
|
||||
ogs_app_policy_conf_t *ogs_app_policy_conf_find_by_plmn_id(
|
||||
ogs_plmn_id_t *plmn_id)
|
||||
ogs_app_policy_conf_t *ogs_app_policy_conf_find(
|
||||
const char *supi, const ogs_plmn_id_t *plmn_id)
|
||||
{
|
||||
ogs_app_policy_conf_t *policy_conf = NULL;
|
||||
ogs_app_policy_conf_t *policy_conf;
|
||||
int i;
|
||||
|
||||
ogs_assert(plmn_id);
|
||||
char *supi_type = NULL;
|
||||
char *supi_id = NULL;
|
||||
uint64_t supi_decimal;
|
||||
|
||||
ogs_assert(supi);
|
||||
|
||||
supi_type = ogs_id_get_type(supi);
|
||||
ogs_assert(supi_type);
|
||||
supi_id = ogs_id_get_value(supi);
|
||||
ogs_assert(supi_id);
|
||||
|
||||
supi_decimal = ogs_uint64_from_string_decimal(supi_id);
|
||||
|
||||
ogs_free(supi_type);
|
||||
ogs_free(supi_id);
|
||||
|
||||
ogs_list_for_each(&local_conf.policy_list, policy_conf) {
|
||||
if (memcmp(&policy_conf->plmn_id, plmn_id, sizeof(ogs_plmn_id_t)) == 0)
|
||||
break;
|
||||
/* If supi_range is set, check if supi_decimal falls within
|
||||
* any of the defined ranges.
|
||||
*/
|
||||
if (policy_conf->supi_range.num > 0) {
|
||||
int in_range = 0;
|
||||
for (i = 0; i < policy_conf->supi_range.num; i++) {
|
||||
if ((supi_decimal >= policy_conf->supi_range.start[i]) &&
|
||||
(supi_decimal <= policy_conf->supi_range.end[i])) {
|
||||
in_range = 1;
|
||||
break;
|
||||
}
|
||||
}
|
||||
if (!in_range) {
|
||||
continue;
|
||||
}
|
||||
}
|
||||
|
||||
/* If a plmn_id is set and it does not match the
|
||||
* current policy's plmn_id, skip this policy.
|
||||
*/
|
||||
if (policy_conf->plmn_id_valid &&
|
||||
memcmp(&policy_conf->plmn_id, plmn_id,
|
||||
sizeof(ogs_plmn_id_t)) != 0) {
|
||||
continue;
|
||||
}
|
||||
|
||||
/* Both conditions met; return this policy configuration */
|
||||
return policy_conf;
|
||||
}
|
||||
|
||||
return policy_conf;
|
||||
return NULL;
|
||||
}
|
||||
void ogs_app_policy_conf_remove(ogs_app_policy_conf_t *policy_conf)
|
||||
{
|
||||
@@ -1223,13 +1386,12 @@ void ogs_app_policy_conf_remove_all(void)
|
||||
}
|
||||
|
||||
ogs_app_slice_conf_t *ogs_app_slice_conf_add(
|
||||
ogs_app_policy_conf_t *policy_conf, ogs_s_nssai_t *s_nssai)
|
||||
ogs_app_policy_conf_t *policy_conf, const ogs_s_nssai_t *s_nssai)
|
||||
{
|
||||
ogs_app_slice_conf_t *slice_conf = NULL;
|
||||
|
||||
ogs_assert(policy_conf);
|
||||
ogs_assert(s_nssai);
|
||||
ogs_assert(s_nssai->sst);
|
||||
|
||||
ogs_pool_alloc(&slice_conf_pool, &slice_conf);
|
||||
if (!slice_conf) {
|
||||
@@ -1254,13 +1416,12 @@ ogs_app_slice_conf_t *ogs_app_slice_conf_add(
|
||||
}
|
||||
|
||||
ogs_app_slice_conf_t *ogs_app_slice_conf_find_by_s_nssai(
|
||||
ogs_app_policy_conf_t *policy_conf, ogs_s_nssai_t *s_nssai)
|
||||
ogs_app_policy_conf_t *policy_conf, const ogs_s_nssai_t *s_nssai)
|
||||
{
|
||||
ogs_app_slice_conf_t *slice_conf = NULL;
|
||||
|
||||
ogs_assert(policy_conf);
|
||||
ogs_assert(s_nssai);
|
||||
ogs_assert(s_nssai->sst);
|
||||
|
||||
ogs_list_for_each(&policy_conf->slice_list, slice_conf) {
|
||||
if (slice_conf->data.s_nssai.sst == s_nssai->sst &&
|
||||
@@ -1325,7 +1486,7 @@ int ogs_app_check_policy_conf(void)
|
||||
}
|
||||
|
||||
ogs_app_session_conf_t *ogs_app_session_conf_add(
|
||||
ogs_app_slice_conf_t *slice_conf, char *name)
|
||||
ogs_app_slice_conf_t *slice_conf, const char *name)
|
||||
{
|
||||
ogs_app_session_conf_t *session_conf = NULL;
|
||||
|
||||
@@ -1357,7 +1518,7 @@ ogs_app_session_conf_t *ogs_app_session_conf_add(
|
||||
return session_conf;
|
||||
}
|
||||
ogs_app_session_conf_t *ogs_app_session_conf_find_by_dnn(
|
||||
ogs_app_slice_conf_t *slice_conf, char *name)
|
||||
ogs_app_slice_conf_t *slice_conf, const char *name)
|
||||
{
|
||||
ogs_app_session_conf_t *session_conf = NULL;
|
||||
|
||||
@@ -1400,29 +1561,27 @@ void ogs_app_session_conf_remove_all(ogs_app_slice_conf_t *slice_conf)
|
||||
}
|
||||
|
||||
int ogs_app_config_session_data(
|
||||
ogs_plmn_id_t *plmn_id, ogs_s_nssai_t *s_nssai, char *dnn,
|
||||
const char *supi, const ogs_plmn_id_t *plmn_id,
|
||||
const ogs_s_nssai_t *s_nssai, const char *dnn,
|
||||
ogs_session_data_t *session_data)
|
||||
{
|
||||
ogs_app_policy_conf_t *policy_conf = NULL;
|
||||
ogs_app_slice_conf_t *slice_conf = NULL;
|
||||
ogs_app_session_conf_t *session_conf = NULL;
|
||||
|
||||
ogs_assert(supi);
|
||||
ogs_assert(dnn);
|
||||
ogs_assert(session_data);
|
||||
|
||||
if (plmn_id) {
|
||||
policy_conf = ogs_app_policy_conf_find_by_plmn_id(plmn_id);
|
||||
if (!policy_conf) {
|
||||
ogs_error("No POLICY [MCC:%03d,MNC:%03d]",
|
||||
ogs_plmn_id_mcc(plmn_id), ogs_plmn_id_mnc(plmn_id));
|
||||
return OGS_ERROR;
|
||||
}
|
||||
} else {
|
||||
policy_conf = ogs_list_first(&ogs_local_conf()->policy_list);
|
||||
if (!policy_conf) {
|
||||
ogs_error("No default POLICY for EPC");
|
||||
return OGS_ERROR;
|
||||
}
|
||||
policy_conf = ogs_app_policy_conf_find(supi, plmn_id);
|
||||
if (!policy_conf) {
|
||||
if (plmn_id)
|
||||
ogs_error("No POLICY [SUPI:%s] [MCC:%03d,MNC:%03d]",
|
||||
supi, ogs_plmn_id_mcc(plmn_id), ogs_plmn_id_mnc(plmn_id));
|
||||
else
|
||||
ogs_error("No POLICY [SUPI:%s]", supi);
|
||||
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
if (s_nssai) {
|
||||
|
||||
@@ -52,6 +52,16 @@ typedef struct ogs_global_conf_s {
|
||||
int no_scp;
|
||||
int no_nrf;
|
||||
|
||||
int amf_count;
|
||||
int smf_count;
|
||||
int upf_count;
|
||||
int ausf_count;
|
||||
int udm_count;
|
||||
int pcf_count;
|
||||
int nssf_count;
|
||||
int bsf_count;
|
||||
int udr_count;
|
||||
|
||||
/* Network */
|
||||
int no_ipv4;
|
||||
int no_ipv6;
|
||||
@@ -59,6 +69,8 @@ typedef struct ogs_global_conf_s {
|
||||
int multicast;
|
||||
|
||||
int use_openair;
|
||||
int fake_csfb;
|
||||
int use_upg_vpp;
|
||||
int no_ipv4v6_local_addr_in_packet_filter;
|
||||
|
||||
int no_pfcp_rr_select;
|
||||
@@ -132,9 +144,24 @@ typedef struct ogs_local_conf_s {
|
||||
|
||||
} ogs_app_local_conf_t;
|
||||
|
||||
/* Structure for SUPI-range */
|
||||
typedef struct {
|
||||
int num;
|
||||
#define OGS_MAX_NUM_OF_SUPI_RANGE 16
|
||||
uint64_t start[OGS_MAX_NUM_OF_SUPI_RANGE];
|
||||
uint64_t end[OGS_MAX_NUM_OF_SUPI_RANGE];
|
||||
} ogs_supi_range_t;
|
||||
|
||||
|
||||
/* Policy configuration structure. In a real system, additional fields
|
||||
* (e.g., for plmn_id, slice list, etc.) would be added.
|
||||
*/
|
||||
typedef struct ogs_app_policy_conf_s {
|
||||
ogs_lnode_t lnode;
|
||||
|
||||
ogs_supi_range_t supi_range;
|
||||
|
||||
bool plmn_id_valid;
|
||||
ogs_plmn_id_t plmn_id;
|
||||
|
||||
ogs_list_t slice_list;
|
||||
@@ -163,39 +190,46 @@ void ogs_app_config_final(void);
|
||||
ogs_app_global_conf_t *ogs_global_conf(void);
|
||||
ogs_app_local_conf_t *ogs_local_conf(void);
|
||||
|
||||
int ogs_app_count_nf_conf_sections(const char *conf_section);
|
||||
int ogs_app_global_conf_prepare(void);
|
||||
int ogs_app_parse_global_conf(ogs_yaml_iter_t *parent);
|
||||
int ogs_app_parse_local_conf(const char *local);
|
||||
|
||||
int ogs_app_parse_sockopt_config(
|
||||
ogs_yaml_iter_t *parent, ogs_sockopt_t *option);
|
||||
|
||||
int ogs_app_parse_supi_range_conf(
|
||||
ogs_yaml_iter_t *parent, ogs_supi_range_t *supi_range);
|
||||
|
||||
int ogs_app_check_policy_conf(void);
|
||||
int ogs_app_parse_session_conf(
|
||||
ogs_yaml_iter_t *parent, ogs_app_slice_conf_t *slice_conf);
|
||||
|
||||
ogs_app_policy_conf_t *ogs_app_policy_conf_add(ogs_plmn_id_t *plmn_id);
|
||||
ogs_app_policy_conf_t *ogs_app_policy_conf_find_by_plmn_id(
|
||||
ogs_plmn_id_t *plmn_id);
|
||||
ogs_app_policy_conf_t *ogs_app_policy_conf_add(
|
||||
ogs_supi_range_t *supi_range, ogs_plmn_id_t *plmn_id);
|
||||
ogs_app_policy_conf_t *ogs_app_policy_conf_find(
|
||||
const char *supi, const ogs_plmn_id_t *plmn_id);
|
||||
void ogs_app_policy_conf_remove(ogs_app_policy_conf_t *policy_conf);
|
||||
void ogs_app_policy_conf_remove_all(void);
|
||||
|
||||
ogs_app_slice_conf_t *ogs_app_slice_conf_add(
|
||||
ogs_app_policy_conf_t *policy_conf, ogs_s_nssai_t *s_nssai);
|
||||
ogs_app_policy_conf_t *policy_conf, const ogs_s_nssai_t *s_nssai);
|
||||
ogs_app_slice_conf_t *ogs_app_slice_conf_find_by_s_nssai(
|
||||
ogs_app_policy_conf_t *policy_conf, ogs_s_nssai_t *s_nssai);
|
||||
ogs_app_policy_conf_t *policy_conf, const ogs_s_nssai_t *s_nssai);
|
||||
void ogs_app_slice_conf_remove(ogs_app_slice_conf_t *slice_conf);
|
||||
void ogs_app_slice_conf_remove_all(ogs_app_policy_conf_t *policy_conf);
|
||||
|
||||
ogs_app_session_conf_t *ogs_app_session_conf_add(
|
||||
ogs_app_slice_conf_t *slice_conf, char *name);
|
||||
ogs_app_slice_conf_t *slice_conf, const char *name);
|
||||
ogs_app_session_conf_t *ogs_app_session_conf_find_by_dnn(
|
||||
ogs_app_slice_conf_t *slice_conf, char *name);
|
||||
ogs_app_slice_conf_t *slice_conf, const char *name);
|
||||
void ogs_app_session_conf_remove(ogs_app_session_conf_t *session_conf);
|
||||
void ogs_app_session_conf_remove_all(
|
||||
ogs_app_slice_conf_t *slice_conf);
|
||||
|
||||
int ogs_app_config_session_data(
|
||||
ogs_plmn_id_t *plmn_id, ogs_s_nssai_t *s_nssai, char *dnn,
|
||||
const char *supi, const ogs_plmn_id_t *plmn_id,
|
||||
const ogs_s_nssai_t *s_nssai, const char *dnn,
|
||||
ogs_session_data_t *session_data);
|
||||
|
||||
#ifdef __cplusplus
|
||||
|
||||
@@ -56,7 +56,7 @@ typedef struct ogs_app_context_s {
|
||||
} usrsctp;
|
||||
|
||||
struct {
|
||||
uint64_t packet;
|
||||
uint64_t gtpu;
|
||||
|
||||
uint64_t sess;
|
||||
uint64_t bearer;
|
||||
@@ -85,6 +85,8 @@ typedef struct ogs_app_context_s {
|
||||
uint64_t max_specs;
|
||||
} metrics;
|
||||
|
||||
int config_section_id;
|
||||
|
||||
} ogs_app_context_t;
|
||||
|
||||
int ogs_app_context_init(void);
|
||||
|
||||
@@ -35,6 +35,7 @@ int ogs_app_initialize(
|
||||
char *log_file;
|
||||
char *log_level;
|
||||
char *domain_mask;
|
||||
char *config_section_id;
|
||||
} optarg;
|
||||
|
||||
ogs_core_initialize();
|
||||
@@ -50,7 +51,7 @@ int ogs_app_initialize(
|
||||
memset(&optarg, 0, sizeof(optarg));
|
||||
|
||||
ogs_getopt_init(&options, (char**)argv);
|
||||
while ((opt = ogs_getopt(&options, "c:l:e:m:")) != -1) {
|
||||
while ((opt = ogs_getopt(&options, "c:l:e:m:k:")) != -1) {
|
||||
switch (opt) {
|
||||
case 'c':
|
||||
optarg.config_file = options.optarg;
|
||||
@@ -64,6 +65,9 @@ int ogs_app_initialize(
|
||||
case 'm':
|
||||
optarg.domain_mask = options.optarg;
|
||||
break;
|
||||
case 'k':
|
||||
optarg.config_section_id = options.optarg;
|
||||
break;
|
||||
case '?':
|
||||
default:
|
||||
ogs_assert_if_reached();
|
||||
@@ -124,7 +128,14 @@ int ogs_app_initialize(
|
||||
ogs_app()->db_uri = ogs_env_get("DB_URI");
|
||||
|
||||
/**************************************************************************
|
||||
* Stage 6 : Print Banner
|
||||
* Stage 6 : Setup configuration section ID for running multiple NF from
|
||||
* same config file
|
||||
*/
|
||||
if (optarg.config_section_id)
|
||||
ogs_app()->config_section_id = atoi(optarg.config_section_id);
|
||||
|
||||
/**************************************************************************
|
||||
* Stage 7 : Print Banner
|
||||
*/
|
||||
if (ogs_app()->version) {
|
||||
ogs_log_print(OGS_LOG_INFO,
|
||||
@@ -144,7 +155,7 @@ int ogs_app_initialize(
|
||||
}
|
||||
|
||||
/**************************************************************************
|
||||
* Stage 7 : Queue, Timer and Poll
|
||||
* Stage 8 : Queue, Timer and Poll
|
||||
*/
|
||||
ogs_app()->queue = ogs_queue_create(ogs_app()->pool.event);
|
||||
ogs_assert(ogs_app()->queue);
|
||||
@@ -246,9 +257,14 @@ static int read_config(void)
|
||||
|
||||
static int context_prepare(void)
|
||||
{
|
||||
int rv;
|
||||
|
||||
#define USRSCTP_LOCAL_UDP_PORT 9899
|
||||
ogs_app()->usrsctp.udp_port = USRSCTP_LOCAL_UDP_PORT;
|
||||
|
||||
rv = ogs_app_global_conf_prepare();
|
||||
if (rv != OGS_OK) return rv;
|
||||
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
@@ -347,6 +363,12 @@ static int parse_config(void)
|
||||
ogs_error("ogs_global_conf_parse_config() failed");
|
||||
return rv;
|
||||
}
|
||||
} else {
|
||||
rv = ogs_app_count_nf_conf_sections(root_key);
|
||||
if (rv != OGS_OK) {
|
||||
ogs_error("ogs_app_count_nf_conf_sections() failed");
|
||||
return rv;
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
@@ -205,8 +205,10 @@ int ogs_asn_ip_to_BIT_STRING(ogs_ip_t *ip, BIT_STRING_t *bit_string)
|
||||
bit_string->buf = CALLOC(bit_string->size, sizeof(uint8_t));
|
||||
memcpy(bit_string->buf, &ip->addr6, OGS_IPV6_LEN);
|
||||
ogs_debug(" IPv6[%s]", OGS_INET_NTOP(&ip->addr6, buf));
|
||||
} else
|
||||
ogs_assert_if_reached();
|
||||
} else {
|
||||
ogs_error("No IPv4 or IPv6");
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
@@ -152,10 +152,17 @@ abts_suite *abts_add_suite(abts_suite *suite, const char *suite_name_full)
|
||||
suite = malloc(sizeof(*suite));
|
||||
suite->head = subsuite;
|
||||
suite->tail = subsuite;
|
||||
}
|
||||
else {
|
||||
suite->tail->next = subsuite;
|
||||
suite->tail = subsuite;
|
||||
} else {
|
||||
/* Clang scan-build SA: NULL pointer dereference: add check for suite->tail=NULL */
|
||||
if (suite->tail) {
|
||||
suite->tail->next = subsuite;
|
||||
suite->tail = subsuite;
|
||||
} else {
|
||||
fprintf(stderr, "suite->tail=NULL\n");
|
||||
fflush(stderr);
|
||||
free(subsuite);
|
||||
return(NULL);
|
||||
}
|
||||
}
|
||||
|
||||
if (!should_test_run(subsuite->name)) {
|
||||
@@ -203,6 +210,13 @@ static int report(abts_suite *suite)
|
||||
end_suite(suite);
|
||||
}
|
||||
|
||||
/* Clang scan-build SA: NULL pointer dereference: suite=NULL */
|
||||
if (!suite) {
|
||||
fprintf(stderr, "suite=NULL\n");
|
||||
fflush(stderr);
|
||||
return(1);
|
||||
}
|
||||
|
||||
for (dptr = suite->head; dptr; dptr = dptr->next) {
|
||||
count += dptr->failed;
|
||||
}
|
||||
@@ -499,6 +513,7 @@ static void show_help(const char *name)
|
||||
" -q : turn off status in test\n"
|
||||
" -x : exclute test-unit (e.g. -x sctp-test)\n"
|
||||
" -l : list test-unit\n"
|
||||
" -k : use <id> config section\n"
|
||||
"\n", name);
|
||||
}
|
||||
|
||||
@@ -509,6 +524,7 @@ int abts_main(int argc, const char *const argv[], const char **argv_out)
|
||||
ogs_getopt_t options;
|
||||
struct {
|
||||
char *config_file;
|
||||
char *config_section;
|
||||
char *log_level;
|
||||
char *domain_mask;
|
||||
|
||||
@@ -519,7 +535,7 @@ int abts_main(int argc, const char *const argv[], const char **argv_out)
|
||||
memset(&optarg, 0, sizeof(optarg));
|
||||
|
||||
ogs_getopt_init(&options, (char**)argv);
|
||||
while ((opt = ogs_getopt(&options, "hvxlqc:e:m:dt")) != -1) {
|
||||
while ((opt = ogs_getopt(&options, "hvxlqc:e:m:dtk:")) != -1) {
|
||||
switch (opt) {
|
||||
case 'h':
|
||||
show_help(argv[0]);
|
||||
@@ -551,6 +567,9 @@ int abts_main(int argc, const char *const argv[], const char **argv_out)
|
||||
case 't':
|
||||
optarg.enable_trace = true;
|
||||
break;
|
||||
case 'k':
|
||||
optarg.config_section = options.optarg;
|
||||
break;
|
||||
case '?':
|
||||
fprintf(stderr, "%s: %s\n", argv[0], options.errmsg);
|
||||
show_help(argv[0]);
|
||||
@@ -588,6 +607,10 @@ int abts_main(int argc, const char *const argv[], const char **argv_out)
|
||||
argv_out[i++] = "-m";
|
||||
argv_out[i++] = optarg.domain_mask;
|
||||
}
|
||||
if (optarg.config_section) {
|
||||
argv_out[i++] = "-k";
|
||||
argv_out[i++] = optarg.config_section;
|
||||
}
|
||||
|
||||
argv_out[i] = NULL;
|
||||
|
||||
|
||||
@@ -214,17 +214,17 @@ char *ogs_uint64_to_string(uint64_t x)
|
||||
return dup;
|
||||
}
|
||||
|
||||
ogs_uint24_t ogs_uint24_from_string(char *str)
|
||||
ogs_uint24_t ogs_uint24_from_string(char *str, int base)
|
||||
{
|
||||
ogs_uint24_t x;
|
||||
|
||||
ogs_assert(str);
|
||||
|
||||
x.v = ogs_uint64_from_string(str);
|
||||
x.v = ogs_uint64_from_string(str, base);
|
||||
return x;
|
||||
}
|
||||
|
||||
uint64_t ogs_uint64_from_string(char *str)
|
||||
uint64_t ogs_uint64_from_string(char *str, int base)
|
||||
{
|
||||
uint64_t x;
|
||||
|
||||
@@ -234,7 +234,7 @@ uint64_t ogs_uint64_from_string(char *str)
|
||||
return 0;
|
||||
|
||||
errno = 0;
|
||||
x = strtoll(str, NULL, 16);
|
||||
x = strtoll(str, NULL, base);
|
||||
|
||||
if ((errno == ERANGE && (x == LONG_MAX || x == LONG_MIN)) ||
|
||||
(errno != 0 && x == 0)) {
|
||||
|
||||
@@ -53,8 +53,17 @@ char *ogs_uint36_to_0string(uint64_t x);
|
||||
char *ogs_uint64_to_0string(uint64_t x);
|
||||
char *ogs_uint64_to_string(uint64_t x);
|
||||
|
||||
ogs_uint24_t ogs_uint24_from_string(char *str);
|
||||
uint64_t ogs_uint64_from_string(char *str);
|
||||
#define ogs_uint24_from_string_decimal(str) \
|
||||
ogs_uint24_from_string((str), 10)
|
||||
#define ogs_uint24_from_string_hexadecimal(str) \
|
||||
ogs_uint24_from_string((str), 16)
|
||||
ogs_uint24_t ogs_uint24_from_string(char *str, int base);
|
||||
|
||||
#define ogs_uint64_from_string_decimal(str) \
|
||||
ogs_uint64_from_string((str), 10)
|
||||
#define ogs_uint64_from_string_hexadecimal(str) \
|
||||
ogs_uint64_from_string((str), 16)
|
||||
uint64_t ogs_uint64_from_string(char *str, int base);
|
||||
|
||||
double *ogs_alloc_double(double value);
|
||||
|
||||
|
||||
@@ -1,5 +1,5 @@
|
||||
/*
|
||||
* Copyright (C) 2019 by Sukchan Lee <acetcom@gmail.com>
|
||||
* Copyright (C) 2019-2025 by Sukchan Lee <acetcom@gmail.com>
|
||||
*
|
||||
* This file is part of Open5GS.
|
||||
*
|
||||
@@ -75,7 +75,8 @@ static void epoll_init(ogs_pollset_t *pollset)
|
||||
|
||||
context->epfd = epoll_create(pollset->capacity);
|
||||
if (context->epfd < 0) {
|
||||
ogs_log_message(OGS_LOG_FATAL, ogs_errno, "epoll_create() failed");
|
||||
ogs_log_message(OGS_LOG_FATAL, ogs_errno,
|
||||
"epoll_create() failed [%d]", pollset->capacity);
|
||||
ogs_assert_if_reached();
|
||||
return;
|
||||
}
|
||||
@@ -231,22 +232,7 @@ static int epoll_process(ogs_pollset_t *pollset, ogs_time_t timeout)
|
||||
|
||||
received = context->event_list[i].events;
|
||||
if (received & EPOLLERR) {
|
||||
/*
|
||||
* The libevent library has OGS_POLLOUT turned on in EPOLLERR.
|
||||
*
|
||||
* However, SIGPIPE can occur if write() is called
|
||||
* when the peer connection is closed.
|
||||
*
|
||||
* Therefore, Open5GS turns off OGS_POLLOUT
|
||||
* so that write() cannot be called in case of EPOLLERR.
|
||||
*
|
||||
* See also #2411 and #2312
|
||||
*/
|
||||
#if 0
|
||||
when = OGS_POLLIN|OGS_POLLOUT;
|
||||
#else
|
||||
when = OGS_POLLIN;
|
||||
#endif
|
||||
} else if ((received & EPOLLHUP) && !(received & EPOLLRDHUP)) {
|
||||
when = OGS_POLLIN|OGS_POLLOUT;
|
||||
} else {
|
||||
|
||||
@@ -222,6 +222,9 @@ static ogs_inline ogs_uint24_t ogs_htobe24(ogs_uint24_t x)
|
||||
((__oBJ)->reference_count)--
|
||||
#define OGS_OBJECT_IS_REF(__oBJ) ((__oBJ)->reference_count > 1)
|
||||
|
||||
#define OGS_POINTER_TO_UINT(u) ((uintptr_t)(u))
|
||||
#define OGS_UINT_TO_POINTER(u) ((void *)(uintptr_t)(u))
|
||||
|
||||
#ifdef __cplusplus
|
||||
}
|
||||
#endif
|
||||
|
||||
@@ -28,7 +28,11 @@
|
||||
extern "C" {
|
||||
#endif
|
||||
|
||||
typedef uint32_t ogs_pool_id_t;
|
||||
#define OGS_INVALID_POOL_ID 0
|
||||
#define OGS_MIN_POOL_ID 1
|
||||
#define OGS_MAX_POOL_ID 0x7fffffff
|
||||
|
||||
typedef int32_t ogs_pool_id_t;
|
||||
|
||||
#define OGS_POOL(pool, type) \
|
||||
struct { \
|
||||
@@ -36,6 +40,9 @@ typedef uint32_t ogs_pool_id_t;
|
||||
int head, tail; \
|
||||
int size, avail; \
|
||||
type **free, *array, **index; \
|
||||
\
|
||||
ogs_hash_t *id_hash; \
|
||||
ogs_pool_id_t id; \
|
||||
} pool
|
||||
|
||||
/*
|
||||
@@ -57,6 +64,9 @@ typedef uint32_t ogs_pool_id_t;
|
||||
(pool)->free[i] = &((pool)->array[i]); \
|
||||
(pool)->index[i] = NULL; \
|
||||
} \
|
||||
\
|
||||
(pool)->id_hash = ogs_hash_make(); \
|
||||
ogs_assert((pool)->id_hash); \
|
||||
} while (0)
|
||||
|
||||
/*
|
||||
@@ -70,6 +80,9 @@ typedef uint32_t ogs_pool_id_t;
|
||||
free((pool)->free); \
|
||||
free((pool)->array); \
|
||||
free((pool)->index); \
|
||||
\
|
||||
ogs_assert((pool)->id_hash); \
|
||||
ogs_hash_destroy((pool)->id_hash); \
|
||||
} while (0)
|
||||
|
||||
/*
|
||||
@@ -93,6 +106,9 @@ typedef uint32_t ogs_pool_id_t;
|
||||
(pool)->free[i] = &((pool)->array[i]); \
|
||||
(pool)->index[i] = NULL; \
|
||||
} \
|
||||
\
|
||||
(pool)->id_hash = ogs_hash_make(); \
|
||||
ogs_assert((pool)->id_hash); \
|
||||
} while (0)
|
||||
|
||||
/*
|
||||
@@ -108,14 +124,11 @@ typedef uint32_t ogs_pool_id_t;
|
||||
ogs_free((pool)->free); \
|
||||
ogs_free((pool)->array); \
|
||||
ogs_free((pool)->index); \
|
||||
\
|
||||
ogs_assert((pool)->id_hash); \
|
||||
ogs_hash_destroy((pool)->id_hash); \
|
||||
} while (0)
|
||||
|
||||
#define ogs_pool_index(pool, node) (((node) - (pool)->array)+1)
|
||||
#define ogs_pool_find(pool, _index) \
|
||||
(_index > 0 && _index <= (pool)->size) ? (pool)->index[_index-1] : NULL
|
||||
#define ogs_pool_cycle(pool, node) \
|
||||
ogs_pool_find((pool), ogs_pool_index((pool), (node)))
|
||||
|
||||
#define ogs_pool_alloc(pool, node) do { \
|
||||
*(node) = NULL; \
|
||||
if ((pool)->avail > 0) { \
|
||||
@@ -136,6 +149,31 @@ typedef uint32_t ogs_pool_id_t;
|
||||
} \
|
||||
} while (0)
|
||||
|
||||
#define ogs_pool_index(pool, node) (((node) - (pool)->array)+1)
|
||||
#define ogs_pool_find(pool, _index) \
|
||||
(_index > 0 && _index <= (pool)->size) ? (pool)->index[_index-1] : NULL
|
||||
|
||||
#define ogs_pool_id_calloc(pool, node) do { \
|
||||
ogs_pool_alloc(pool, node); \
|
||||
if (*node) { \
|
||||
memset(*(node), 0, sizeof(**(node))); \
|
||||
(*(node))->id = OGS_NEXT_ID((pool)->id, 1, OGS_MAX_POOL_ID); \
|
||||
ogs_hash_set((pool)->id_hash, \
|
||||
&((*(node))->id), sizeof(ogs_pool_id_t), *(node)); \
|
||||
} \
|
||||
} while (0)
|
||||
|
||||
#define ogs_pool_id_free(pool, node) do { \
|
||||
ogs_assert(((node)->id) >= OGS_MIN_POOL_ID && \
|
||||
((node)->id) <= OGS_MAX_POOL_ID); \
|
||||
ogs_hash_set((pool)->id_hash, \
|
||||
&((node)->id), sizeof(ogs_pool_id_t), NULL); \
|
||||
ogs_pool_free(pool, node); \
|
||||
} while (0)
|
||||
|
||||
#define ogs_pool_find_by_id(pool, id) \
|
||||
ogs_hash_get((pool)->id_hash, &id, sizeof(ogs_pool_id_t))
|
||||
|
||||
#define ogs_pool_size(pool) ((pool)->size)
|
||||
#define ogs_pool_avail(pool) ((pool)->avail)
|
||||
|
||||
|
||||
@@ -370,9 +370,17 @@ int ogs_proc_join(ogs_proc_t *const process, int *const out_return_code)
|
||||
}
|
||||
|
||||
if (process->child != waitpid(process->child, &status, 0)) {
|
||||
process->child = 0;
|
||||
ogs_error("waitpid failed: %d", status);
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
process->child = 0;
|
||||
if (process->nf_name) {
|
||||
ogs_free(process->nf_name);
|
||||
process->nf_name = NULL;
|
||||
}
|
||||
|
||||
if (out_return_code) {
|
||||
if (WIFEXITED(status)) {
|
||||
*out_return_code = WEXITSTATUS(status);
|
||||
@@ -416,9 +424,17 @@ int ogs_proc_terminate(ogs_proc_t *const process)
|
||||
return OGS_ERROR;
|
||||
}
|
||||
#else
|
||||
if (kill(process->child, SIGTERM) == -1) {
|
||||
return OGS_ERROR;
|
||||
|
||||
if (process->child) {
|
||||
if (kill(process->child, SIGTERM) == -1) {
|
||||
if (errno == ESRCH) {
|
||||
/* No such process */
|
||||
return OGS_OK;
|
||||
}
|
||||
return OGS_ERROR;
|
||||
}
|
||||
}
|
||||
|
||||
#endif
|
||||
|
||||
return OGS_OK;
|
||||
@@ -434,8 +450,14 @@ int ogs_proc_kill(ogs_proc_t *const process)
|
||||
return OGS_ERROR;
|
||||
}
|
||||
#else
|
||||
if (kill(process->child, SIGKILL) == -1) {
|
||||
return OGS_ERROR;
|
||||
if (process->child) {
|
||||
if (kill(process->child, SIGKILL) == -1) {
|
||||
if (errno == ESRCH) {
|
||||
/* No such process */
|
||||
return OGS_OK;
|
||||
}
|
||||
return OGS_ERROR;
|
||||
}
|
||||
}
|
||||
#endif
|
||||
|
||||
|
||||
@@ -73,6 +73,10 @@ typedef struct ogs_proc_s {
|
||||
unsigned long dwProcessId;
|
||||
#else
|
||||
pid_t child;
|
||||
|
||||
// to force kill the right NF in tests if needed.
|
||||
char *nf_name;
|
||||
int index;
|
||||
#endif
|
||||
} ogs_proc_t;
|
||||
|
||||
|
||||
@@ -15,7 +15,7 @@
|
||||
*/
|
||||
|
||||
/*
|
||||
* Copyright (C) 2019 by Sukchan Lee <acetcom@gmail.com>
|
||||
* Copyright (C) 2019-2025 by Sukchan Lee <acetcom@gmail.com>
|
||||
*
|
||||
* This file is part of Open5GS.
|
||||
*
|
||||
@@ -277,9 +277,20 @@ static void remove_sync_sigs(sigset_t *sig_mask)
|
||||
#ifdef SIGIOT
|
||||
sigdelset(sig_mask, SIGIOT);
|
||||
#endif
|
||||
|
||||
/*
|
||||
* SIGPIPE can occur if write() is called when the peer connection is closed.
|
||||
*
|
||||
* Therefore, Open5GS ignore SIGPIE signal
|
||||
*
|
||||
* See also #2411 and #2312
|
||||
*/
|
||||
#if 0
|
||||
#ifdef SIGPIPE
|
||||
sigdelset(sig_mask, SIGPIPE);
|
||||
#endif
|
||||
#endif
|
||||
|
||||
#ifdef SIGSEGV
|
||||
sigdelset(sig_mask, SIGSEGV);
|
||||
#endif
|
||||
|
||||
@@ -55,6 +55,10 @@
|
||||
#undef OGS_LOG_DOMAIN
|
||||
#define OGS_LOG_DOMAIN __ogs_sock_domain
|
||||
|
||||
static bool ogs_sockaddr_compare(const ogs_sockaddr_t *a,
|
||||
const ogs_sockaddr_t *b,
|
||||
bool compare_port);
|
||||
|
||||
/* If you want to use getnameinfo,
|
||||
* you need to consider DNS query delay (about 10 seconds) */
|
||||
#if 0
|
||||
@@ -99,11 +103,18 @@ int ogs_addaddrinfo(ogs_sockaddr_t **sa_list,
|
||||
int rc;
|
||||
char service[NI_MAXSERV];
|
||||
struct addrinfo hints, *ai, *ai_list;
|
||||
ogs_sockaddr_t *prev;
|
||||
ogs_sockaddr_t *prev = NULL;
|
||||
|
||||
/* Last node of original list (for appending) */
|
||||
ogs_sockaddr_t *tail = NULL;
|
||||
/* First newly added node (for cleanup on error) */
|
||||
ogs_sockaddr_t *first_new = NULL;
|
||||
|
||||
char buf[OGS_ADDRSTRLEN];
|
||||
|
||||
ogs_assert(sa_list);
|
||||
|
||||
/* Prepare hints for getaddrinfo() */
|
||||
memset(&hints, 0, sizeof(hints));
|
||||
hints.ai_family = family;
|
||||
hints.ai_socktype = SOCK_STREAM;
|
||||
@@ -114,24 +125,41 @@ int ogs_addaddrinfo(ogs_sockaddr_t **sa_list,
|
||||
rc = getaddrinfo(hostname, service, &hints, &ai_list);
|
||||
if (rc != 0) {
|
||||
ogs_log_message(OGS_LOG_ERROR, ogs_socket_errno,
|
||||
"getaddrinfo(%d:%s:%d:0x%x) failed",
|
||||
family, hostname, port, flags);
|
||||
"getaddrinfo(%d:%s:%d:0x%x) failed: %s",
|
||||
family, hostname ? hostname : "(null)",
|
||||
port, flags, gai_strerror(rc));
|
||||
/* Non-fatal: log the error and return */
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
prev = NULL;
|
||||
/* Find the end of the existing list, so new entries can be appended */
|
||||
if (*sa_list) {
|
||||
prev = *sa_list;
|
||||
while(prev->next) prev = prev->next;
|
||||
tail = *sa_list;
|
||||
while (tail->next)
|
||||
tail = tail->next;
|
||||
prev = tail;
|
||||
}
|
||||
|
||||
/* Iterate over each result from getaddrinfo and add to the linked list */
|
||||
for (ai = ai_list; ai; ai = ai->ai_next) {
|
||||
ogs_sockaddr_t *new, tmp;
|
||||
if (ai->ai_family != AF_INET && ai->ai_family != AF_INET6)
|
||||
continue;
|
||||
continue; /* Skip unsupported address families */
|
||||
|
||||
new = ogs_calloc(1, sizeof(ogs_sockaddr_t));
|
||||
if (!new) {
|
||||
ogs_error("ogs_calloc() failed");
|
||||
/* Clean up any partially added entries on memory failure */
|
||||
if (first_new) {
|
||||
if (tail) {
|
||||
/* detach new sub-list from original list */
|
||||
tail->next = NULL;
|
||||
} else {
|
||||
*sa_list = NULL; /* no original list, reset head */
|
||||
}
|
||||
ogs_freeaddrinfo(first_new);
|
||||
}
|
||||
freeaddrinfo(ai_list);
|
||||
return OGS_ERROR;
|
||||
}
|
||||
memcpy(&new->sa, ai->ai_addr, ai->ai_addrlen);
|
||||
@@ -139,30 +167,49 @@ int ogs_addaddrinfo(ogs_sockaddr_t **sa_list,
|
||||
|
||||
if (hostname) {
|
||||
if (ogs_inet_pton(ai->ai_family, hostname, &tmp) == OGS_OK) {
|
||||
/* It's a valid IP address */
|
||||
/* Input string is a valid numeric IP address */
|
||||
ogs_debug("addr:%s, port:%d", OGS_ADDR(new, buf), port);
|
||||
} else {
|
||||
/* INVALID IP address! We assume it is a hostname */
|
||||
/* Input string is not a numeric IP; treat it as a hostname */
|
||||
new->hostname = ogs_strdup(hostname);
|
||||
ogs_assert(new->hostname);
|
||||
if (!new->hostname) {
|
||||
ogs_error("ogs_strdup() failed");
|
||||
/* Free the new node and any previously added nodes */
|
||||
ogs_free(new);
|
||||
if (first_new) {
|
||||
if (tail) {
|
||||
tail->next = NULL;
|
||||
} else {
|
||||
*sa_list = NULL;
|
||||
}
|
||||
ogs_freeaddrinfo(first_new);
|
||||
}
|
||||
freeaddrinfo(ai_list);
|
||||
return OGS_ERROR;
|
||||
}
|
||||
ogs_debug("name:%s, port:%d", new->hostname, port);
|
||||
}
|
||||
}
|
||||
|
||||
if (!prev)
|
||||
/* Link the new node into the list */
|
||||
if (!prev) {
|
||||
*sa_list = new;
|
||||
else
|
||||
} else {
|
||||
prev->next = new;
|
||||
|
||||
}
|
||||
prev = new;
|
||||
if (!first_new) {
|
||||
first_new = new; /* mark the first new node added */
|
||||
}
|
||||
}
|
||||
|
||||
freeaddrinfo(ai_list);
|
||||
|
||||
if (prev == NULL) {
|
||||
if (first_new == NULL) {
|
||||
/* No addresses were added (e.g., no AF_INET/AF_INET6 results) */
|
||||
ogs_log_message(OGS_LOG_ERROR, ogs_socket_errno,
|
||||
"ogs_getaddrinfo(%d:%s:%d:%d) failed",
|
||||
family, hostname, port, flags);
|
||||
"ogs_addaddrinfo(%d:%s:%d:0x%x) returned no addresses",
|
||||
family, hostname ? hostname : "(null)", port, flags);
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
@@ -264,6 +311,60 @@ int ogs_sortaddrinfo(ogs_sockaddr_t **sa_list, int family)
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
/*--------------------------------------------------------------------------
|
||||
* Merge a single node if not already in "dest" list
|
||||
*--------------------------------------------------------------------------
|
||||
*/
|
||||
void ogs_merge_single_addrinfo(
|
||||
ogs_sockaddr_t **dest, const ogs_sockaddr_t *item)
|
||||
{
|
||||
ogs_sockaddr_t *p;
|
||||
ogs_sockaddr_t *new_sa;
|
||||
|
||||
ogs_assert(dest);
|
||||
ogs_assert(item);
|
||||
|
||||
p = *dest;
|
||||
|
||||
while (p) {
|
||||
if (ogs_sockaddr_is_equal(p, item)) {
|
||||
/* Already exists */
|
||||
return;
|
||||
}
|
||||
p = p->next;
|
||||
}
|
||||
new_sa = (ogs_sockaddr_t *)ogs_malloc(sizeof(*new_sa));
|
||||
ogs_assert(new_sa);
|
||||
memcpy(new_sa, item, sizeof(*new_sa));
|
||||
if (item->hostname) {
|
||||
new_sa->hostname = ogs_strdup(item->hostname);
|
||||
ogs_assert(new_sa->hostname);
|
||||
}
|
||||
new_sa->next = NULL;
|
||||
if (!(*dest)) {
|
||||
*dest = new_sa;
|
||||
} else {
|
||||
p = *dest;
|
||||
while (p->next)
|
||||
p = p->next;
|
||||
p->next = new_sa;
|
||||
}
|
||||
}
|
||||
|
||||
/*--------------------------------------------------------------------------
|
||||
* Merge an entire src list into dest
|
||||
*--------------------------------------------------------------------------
|
||||
*/
|
||||
void ogs_merge_addrinfo(ogs_sockaddr_t **dest, const ogs_sockaddr_t *src)
|
||||
{
|
||||
const ogs_sockaddr_t *cur;
|
||||
cur = src;
|
||||
while (cur) {
|
||||
ogs_merge_single_addrinfo(dest, cur);
|
||||
cur = cur->next;
|
||||
}
|
||||
}
|
||||
|
||||
ogs_sockaddr_t *ogs_link_local_addr(const char *dev, const ogs_sockaddr_t *sa)
|
||||
{
|
||||
#if defined(HAVE_GETIFADDRS)
|
||||
@@ -419,13 +520,16 @@ socklen_t ogs_sockaddr_len(const void *sa)
|
||||
}
|
||||
}
|
||||
|
||||
bool ogs_sockaddr_is_equal(const void *p, const void *q)
|
||||
/*
|
||||
* Helper function to compare two addresses.
|
||||
* If compare_port is true, compare both port and address.
|
||||
* Otherwise, compare address only.
|
||||
*/
|
||||
static bool ogs_sockaddr_compare(const ogs_sockaddr_t *a,
|
||||
const ogs_sockaddr_t *b,
|
||||
bool compare_port)
|
||||
{
|
||||
const ogs_sockaddr_t *a, *b;
|
||||
|
||||
a = p;
|
||||
ogs_assert(a);
|
||||
b = q;
|
||||
ogs_assert(b);
|
||||
|
||||
if (a->ogs_sa_family != b->ogs_sa_family)
|
||||
@@ -433,23 +537,68 @@ bool ogs_sockaddr_is_equal(const void *p, const void *q)
|
||||
|
||||
switch (a->ogs_sa_family) {
|
||||
case AF_INET:
|
||||
if (a->sin.sin_port != b->sin.sin_port)
|
||||
if (compare_port && (a->sin.sin_port != b->sin.sin_port))
|
||||
return false;
|
||||
if (memcmp(&a->sin.sin_addr, &b->sin.sin_addr, sizeof(struct in_addr)) != 0)
|
||||
if (memcmp(&a->sin.sin_addr, &b->sin.sin_addr,
|
||||
sizeof(struct in_addr)) != 0)
|
||||
return false;
|
||||
return true;
|
||||
case AF_INET6:
|
||||
if (a->sin6.sin6_port != b->sin6.sin6_port)
|
||||
if (compare_port && (a->sin6.sin6_port != b->sin6.sin6_port))
|
||||
return false;
|
||||
if (memcmp(&a->sin6.sin6_addr, &b->sin6.sin6_addr, sizeof(struct in6_addr)) != 0)
|
||||
if (memcmp(&a->sin6.sin6_addr, &b->sin6.sin6_addr,
|
||||
sizeof(struct in6_addr)) != 0)
|
||||
return false;
|
||||
return true;
|
||||
default:
|
||||
ogs_error("Unexpected address faimily %u", a->ogs_sa_family);
|
||||
ogs_error("Unexpected address family %u", a->ogs_sa_family);
|
||||
ogs_abort();
|
||||
return false; /* Defensive return */
|
||||
}
|
||||
}
|
||||
|
||||
/* Compare addresses including port */
|
||||
bool ogs_sockaddr_is_equal(const void *p, const void *q)
|
||||
{
|
||||
const ogs_sockaddr_t *a = (const ogs_sockaddr_t *)p;
|
||||
const ogs_sockaddr_t *b = (const ogs_sockaddr_t *)q;
|
||||
return ogs_sockaddr_compare(a, b, true);
|
||||
}
|
||||
|
||||
/* Compare addresses without considering port */
|
||||
bool ogs_sockaddr_is_equal_addr(const void *p, const void *q)
|
||||
{
|
||||
const ogs_sockaddr_t *a = (const ogs_sockaddr_t *)p;
|
||||
const ogs_sockaddr_t *b = (const ogs_sockaddr_t *)q;
|
||||
return ogs_sockaddr_compare(a, b, false);
|
||||
}
|
||||
|
||||
bool ogs_sockaddr_check_any_match(
|
||||
ogs_sockaddr_t *base,
|
||||
ogs_sockaddr_t *list, const ogs_sockaddr_t *single, bool compare_port)
|
||||
{
|
||||
ogs_sockaddr_t *p = NULL;
|
||||
|
||||
while (list) {
|
||||
p = base;
|
||||
while (p) {
|
||||
if (ogs_sockaddr_compare(p, list, compare_port) == true)
|
||||
return true;
|
||||
p = p->next;
|
||||
}
|
||||
list = list->next;
|
||||
}
|
||||
if (single) {
|
||||
p = base;
|
||||
while (p) {
|
||||
if (ogs_sockaddr_compare(p, single, compare_port) == true)
|
||||
return true;
|
||||
p = p->next;
|
||||
}
|
||||
}
|
||||
return false;
|
||||
}
|
||||
|
||||
static int parse_network(ogs_ipsubnet_t *ipsub, const char *network)
|
||||
{
|
||||
/* legacy syntax for ip addrs: a.b.c. ==> a.b.c.0/24 for example */
|
||||
@@ -666,3 +815,65 @@ char *ogs_ipstrdup(ogs_sockaddr_t *addr)
|
||||
|
||||
return ogs_strdup(buf);
|
||||
}
|
||||
|
||||
char *ogs_sockaddr_to_string_static(ogs_sockaddr_t *sa_list)
|
||||
{
|
||||
static char dumpstr[OGS_HUGE_LEN] = { 0, };
|
||||
char *p, *last;
|
||||
ogs_sockaddr_t *addr = NULL;
|
||||
|
||||
last = dumpstr + OGS_HUGE_LEN;
|
||||
p = dumpstr;
|
||||
|
||||
addr = (ogs_sockaddr_t *)sa_list;
|
||||
while (addr) {
|
||||
char buf[OGS_ADDRSTRLEN];
|
||||
p = ogs_slprintf(p, last, "[%s]:%d ",
|
||||
OGS_ADDR(addr, buf), OGS_PORT(addr));
|
||||
addr = addr->next;
|
||||
}
|
||||
|
||||
if (p > dumpstr) {
|
||||
/* If there is more than one addr, remove the last character */
|
||||
*(p-1) = 0;
|
||||
|
||||
return dumpstr;
|
||||
}
|
||||
|
||||
/* No address */
|
||||
return NULL;
|
||||
}
|
||||
|
||||
int ogs_sockaddr_from_ip_or_fqdn(ogs_sockaddr_t **sa_list,
|
||||
int family, const char *ip_or_fqdn, uint16_t port)
|
||||
{
|
||||
int rc;
|
||||
int flags = 0;
|
||||
ogs_sockaddr_t tmp;
|
||||
|
||||
ogs_assert(sa_list);
|
||||
ogs_assert(ip_or_fqdn);
|
||||
|
||||
/* Determine if the input is an IP literal (numeric address).
|
||||
* If so, use AI_NUMERICHOST to avoid DNS lookup. */
|
||||
if (ogs_inet_pton(AF_INET, ip_or_fqdn, &tmp) == OGS_OK ||
|
||||
ogs_inet_pton(AF_INET6, ip_or_fqdn, &tmp) == OGS_OK) {
|
||||
flags |= AI_NUMERICHOST;
|
||||
}
|
||||
|
||||
/* Use ogs_addaddrinfo
|
||||
* to perform resolution and construct the sockaddr list */
|
||||
*sa_list = NULL;
|
||||
rc = ogs_addaddrinfo(sa_list, family, ip_or_fqdn, port, flags);
|
||||
if (rc != OGS_OK) {
|
||||
ogs_error("Failed to resolve address: %s", ip_or_fqdn);
|
||||
/* Cleanup: free any nodes that might have been added before failure */
|
||||
if (*sa_list) {
|
||||
ogs_freeaddrinfo(*sa_list);
|
||||
*sa_list = NULL;
|
||||
}
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
return OGS_OK;
|
||||
}
|
||||
|
||||
@@ -67,20 +67,8 @@ struct ogs_sockaddr_s {
|
||||
* If there is a name in the configuration file,
|
||||
* it is set in the 'hostname' of ogs_sockaddr_t.
|
||||
* Then, it immediately call getaddrinfo() to fill addr in ogs_sockaddr_t.
|
||||
*
|
||||
* When it was always possible to convert DNS to addr, that was no problem.
|
||||
* However, in some environments, such as Roaming, there are situations
|
||||
* where it is difficult to always change the DNS to addr.
|
||||
*
|
||||
* So, 'fqdn' was created for the purpose of first use in ogs_sbi_client_t.
|
||||
* 'fqdn' always do not change with addr.
|
||||
* This value is used as it is in the actual client connection.
|
||||
*
|
||||
* Note that 'hostname' is still in use for server or other client
|
||||
* except for ogs_sbi_client_t.
|
||||
*/
|
||||
char *hostname;
|
||||
char *fqdn;
|
||||
|
||||
ogs_sockaddr_t *next;
|
||||
};
|
||||
@@ -103,6 +91,10 @@ int ogs_copyaddrinfo(
|
||||
int ogs_filteraddrinfo(ogs_sockaddr_t **sa_list, int family);
|
||||
int ogs_sortaddrinfo(ogs_sockaddr_t **sa_list, int family);
|
||||
|
||||
void ogs_merge_single_addrinfo(
|
||||
ogs_sockaddr_t **dest, const ogs_sockaddr_t *item);
|
||||
void ogs_merge_addrinfo(ogs_sockaddr_t **dest, const ogs_sockaddr_t *src);
|
||||
|
||||
ogs_sockaddr_t *ogs_link_local_addr(const char *dev, const ogs_sockaddr_t *sa);
|
||||
ogs_sockaddr_t *ogs_link_local_addr_by_dev(const char *dev);
|
||||
ogs_sockaddr_t *ogs_link_local_addr_by_sa(const ogs_sockaddr_t *sa);
|
||||
@@ -119,12 +111,20 @@ int ogs_inet_pton(int family, const char *src, void *sa);
|
||||
|
||||
socklen_t ogs_sockaddr_len(const void *sa);
|
||||
bool ogs_sockaddr_is_equal(const void *p, const void *q);
|
||||
bool ogs_sockaddr_is_equal_addr(const void *p, const void *q);
|
||||
|
||||
bool ogs_sockaddr_check_any_match(
|
||||
ogs_sockaddr_t *base,
|
||||
ogs_sockaddr_t *list, const ogs_sockaddr_t *single, bool compare_port);
|
||||
|
||||
int ogs_ipsubnet(ogs_ipsubnet_t *ipsub,
|
||||
const char *ipstr, const char *mask_or_numbits);
|
||||
|
||||
char *ogs_gethostname(ogs_sockaddr_t *addr);
|
||||
char *ogs_ipstrdup(ogs_sockaddr_t *addr);
|
||||
char *ogs_sockaddr_to_string_static(ogs_sockaddr_t *sa_list);
|
||||
int ogs_sockaddr_from_ip_or_fqdn(ogs_sockaddr_t **sa_list,
|
||||
int family, const char *ip_or_fqdn, uint16_t port);
|
||||
|
||||
#ifdef __cplusplus
|
||||
}
|
||||
|
||||
@@ -84,8 +84,11 @@ typedef int64_t ogs_time_t;
|
||||
/** @return ogs_time_t as a msec */
|
||||
#define ogs_time_msec(time) (((time) / 1000) % 1000)
|
||||
|
||||
/** @return ogs_time_t as a msec */
|
||||
/** @return ogs_time_t to msec */
|
||||
#define ogs_time_to_msec(time) ((time) ? (1 + ((time) - 1) / 1000) : 0)
|
||||
/** @return ogs_time_t to sec */
|
||||
#define ogs_time_to_sec(time) \
|
||||
((time) ? (1 + ((time) - 1) / OGS_USEC_PER_SEC) : 0)
|
||||
|
||||
/** @return milliseconds as an ogs_time_t */
|
||||
#define ogs_time_from_msec(msec) ((ogs_time_t)(msec) * 1000)
|
||||
|
||||
@@ -73,12 +73,6 @@ void ogs_timer_mgr_destroy(ogs_timer_mgr_t *manager)
|
||||
ogs_free(manager);
|
||||
}
|
||||
|
||||
static ogs_timer_t *ogs_timer_cycle(ogs_timer_mgr_t *manager, ogs_timer_t *timer)
|
||||
{
|
||||
ogs_assert(manager);
|
||||
return ogs_pool_cycle(&manager->pool, timer);
|
||||
}
|
||||
|
||||
ogs_timer_t *ogs_timer_add(
|
||||
ogs_timer_mgr_t *manager, void (*cb)(void *data), void *data)
|
||||
{
|
||||
@@ -106,11 +100,6 @@ void ogs_timer_delete_debug(ogs_timer_t *timer, const char *file_line)
|
||||
ogs_assert(timer);
|
||||
manager = timer->manager;
|
||||
ogs_assert(manager);
|
||||
timer = ogs_timer_cycle(manager, timer);
|
||||
if (!timer) {
|
||||
ogs_fatal("ogs_timer_delete() failed in %s", file_line);
|
||||
ogs_assert_if_reached();
|
||||
}
|
||||
|
||||
ogs_timer_stop(timer);
|
||||
|
||||
@@ -126,11 +115,6 @@ void ogs_timer_start_debug(
|
||||
|
||||
manager = timer->manager;
|
||||
ogs_assert(manager);
|
||||
timer = ogs_timer_cycle(manager, timer);
|
||||
if (!timer) {
|
||||
ogs_fatal("ogs_timer_start() failed in %s", file_line);
|
||||
ogs_assert_if_reached();
|
||||
}
|
||||
|
||||
if (timer->running == true)
|
||||
ogs_rbtree_delete(&manager->tree, timer);
|
||||
@@ -145,11 +129,6 @@ void ogs_timer_stop_debug(ogs_timer_t *timer, const char *file_line)
|
||||
ogs_assert(timer);
|
||||
manager = timer->manager;
|
||||
ogs_assert(manager);
|
||||
timer = ogs_timer_cycle(manager, timer);
|
||||
if (!timer) {
|
||||
ogs_fatal("ogs_timer_stop() failed in %s", file_line);
|
||||
ogs_assert_if_reached();
|
||||
}
|
||||
|
||||
if (timer->running == false)
|
||||
return;
|
||||
|
||||
@@ -1075,6 +1075,11 @@ int ecc_make_key(uint8_t p_publicKey[ECC_BYTES+1], uint8_t p_privateKey[ECC_BYTE
|
||||
EccPoint l_public;
|
||||
unsigned l_tries = 0;
|
||||
|
||||
/* Clang scan-build SA: Branch condition evaluates to garbage value: In 1st pass thru the do loop the struct l_public
|
||||
* will not contain a value in the while() check if vli_isZero(l_private)==true and the continue branch is taken.
|
||||
* Initialize l_public to fix the issue. */
|
||||
memset(&l_public, 0, sizeof(EccPoint));
|
||||
|
||||
do
|
||||
{
|
||||
if(!getRandomNumber(l_private) || (l_tries++ >= MAX_TRIES))
|
||||
@@ -1255,6 +1260,11 @@ int ecdsa_sign(const uint8_t p_privateKey[ECC_BYTES], const uint8_t p_hash[ECC_B
|
||||
EccPoint p;
|
||||
unsigned l_tries = 0;
|
||||
|
||||
/* Clang scan-build SA: Branch condition evaluates to garbage value: In 1st pass thru the do loop the struct "p"
|
||||
* will not contain a value in the while() check if vli_isZero(k)==true and the continue branch is taken.
|
||||
* Initialize "p" to fix the issue. */
|
||||
memset(&p, 0, sizeof(EccPoint));
|
||||
|
||||
do
|
||||
{
|
||||
if(!getRandomNumber(k) || (l_tries++ >= MAX_TRIES))
|
||||
|
||||
@@ -292,7 +292,13 @@ void kasumi_f8(u8 *key, u32 count, u32 bearer, u32 dir, u8 *data, int length)
|
||||
/* Construct the modified key and then "kasumi" A */
|
||||
for( n=0; n<16; ++n )
|
||||
ModKey[n] = (u8)(key[n] ^ 0x55);
|
||||
|
||||
/* Clang scan-build SA: Result of operation is garbage: The function kasumi_key_schedule() is reporting that
|
||||
* the array parameter "k" (ModKey) has garbage/uninitialized values. Don't see how that is possible
|
||||
* because the array is fully populated by the loop above. */
|
||||
#ifndef __clang_analyzer__
|
||||
kasumi_key_schedule( ModKey );
|
||||
#endif
|
||||
|
||||
kasumi( A.b8 ); /* First encryption to create modifier */
|
||||
|
||||
@@ -454,7 +460,13 @@ u8 *kasumi_f9(u8 *key, u32 count, u32 fresh, u32 dir, u8 *data, int length)
|
||||
* key XORd with 0xAAAA..... */
|
||||
for( n=0; n<16; ++n )
|
||||
ModKey[n] = (u8)*key++ ^ 0xAA;
|
||||
|
||||
/* Clang scan-build SA: Result of operation is garbage: The function kasumi_key_schedule() is reporting that
|
||||
* the array parameter "k" (ModKey) has garbage/uninitialized values. Don't see how that is possible
|
||||
* because the array is fully populated by the loop above. */
|
||||
#ifndef __clang_analyzer__
|
||||
kasumi_key_schedule( ModKey );
|
||||
#endif
|
||||
kasumi( B.b8 );
|
||||
|
||||
/* We return the left-most 32-bits of the result */
|
||||
|
||||
@@ -1255,6 +1255,12 @@ int ogs_aes_cbc_encrypt(const uint8_t *key, const uint32_t keybits,
|
||||
|
||||
*outlen = ((inlen - 1) / OGS_AES_BLOCK_SIZE + 1) * OGS_AES_BLOCK_SIZE;
|
||||
|
||||
/* Clang scan-build SA: Result of operation is garbage: The function ogs_aes_encrypt() is reporting that the
|
||||
* array parameter rk has garbage/uninitialized values. The garbage values are because the SA is taking a path
|
||||
* through ogs_aes_setup_enc() that doesn't match a valid keybits value and therefore the function is not
|
||||
* populating rk. Fix the issue by initializing rk to 0 here. */
|
||||
memset(rk, 0, sizeof(rk));
|
||||
|
||||
nrounds = ogs_aes_setup_enc(rk, key, keybits);
|
||||
|
||||
while (len >= OGS_AES_BLOCK_SIZE)
|
||||
@@ -1310,6 +1316,12 @@ int ogs_aes_cbc_decrypt(const uint8_t *key, const uint32_t keybits,
|
||||
|
||||
*outlen = inlen;
|
||||
|
||||
/* Clang scan-build SA: Result of operation is garbage: The function ogs_aes_decrypt() is reporting that the
|
||||
* array parameter rk has garbage/uninitialized values. The garbage values are because the SA is taking a path
|
||||
* through ogs_aes_setup_enc() (from ogs_aes_setup_dec()) that doesn't match a valid keybits value and
|
||||
* therefore the function is not populating rk. Fix the issue by initializing rk to 0 here. */
|
||||
memset(rk, 0, sizeof(rk));
|
||||
|
||||
nrounds = ogs_aes_setup_dec(rk, key, keybits);
|
||||
|
||||
if (in != out)
|
||||
|
||||
@@ -327,12 +327,18 @@ void zuc_eea3(u8* CK, u32 COUNT, u32 BEARER, u32 DIRECTION,
|
||||
C[i] = M[i] ^ ((z[i/4] >> (3-i%4)*8) & 0xff);
|
||||
}
|
||||
|
||||
/*
|
||||
* Issues #3349
|
||||
* Valgrind memcheck: Invalid read & write: Add {}.
|
||||
*/
|
||||
|
||||
/* zero last bits of data in case its length is not word-aligned (32 bits)
|
||||
this is an addition to the C reference code, which did not handle it */
|
||||
if (lastbits)
|
||||
if (lastbits) {
|
||||
i--;
|
||||
C[i] &= 0x100 - (1<<lastbits);
|
||||
|
||||
}
|
||||
|
||||
ogs_free(z);
|
||||
}
|
||||
/* end of EEA3.c */
|
||||
|
||||
219
lib/dbi/ims.c
219
lib/dbi/ims.c
@@ -120,7 +120,8 @@ int ogs_dbi_ims_data(char *supi, ogs_ims_data_t *ims_data)
|
||||
bson_error_t error;
|
||||
const bson_t *document;
|
||||
bson_iter_t iter;
|
||||
bson_iter_t child1_iter;
|
||||
bson_iter_t child1_iter, child2_iter, child3_iter, child4_iter, child5_iter;
|
||||
bson_iter_t child6_iter, child7_iter, child8_iter, child9_iter;
|
||||
const char *utf8 = NULL;
|
||||
uint32_t length = 0;
|
||||
|
||||
@@ -190,6 +191,222 @@ int ogs_dbi_ims_data(char *supi, ogs_ims_data_t *ims_data)
|
||||
}
|
||||
}
|
||||
ims_data->num_of_msisdn = msisdn_index;
|
||||
} else if (!strcmp(key, "ifc") &&
|
||||
BSON_ITER_HOLDS_ARRAY(&iter)) {
|
||||
int ifc_index = 0;
|
||||
bson_iter_recurse(&iter, &child2_iter);
|
||||
while (bson_iter_next(&child2_iter)) {
|
||||
ogs_assert(ifc_index < OGS_MAX_NUM_OF_IFC);
|
||||
bson_iter_recurse(&child2_iter, &child3_iter);
|
||||
while (bson_iter_next(&child3_iter)) {
|
||||
const char *child3_key = bson_iter_key(&child3_iter);
|
||||
if (!strcmp(child3_key, "priority") &&
|
||||
BSON_ITER_HOLDS_INT32(&child3_iter)) {
|
||||
ims_data->ifc[ifc_index].priority =
|
||||
bson_iter_int32(&child3_iter);
|
||||
} else if (!strcmp(child3_key, "application_server") &&
|
||||
BSON_ITER_HOLDS_DOCUMENT(&child3_iter)) {
|
||||
bson_iter_recurse(&child3_iter, &child4_iter);
|
||||
while (bson_iter_next(&child4_iter)) {
|
||||
const char *child4_key =
|
||||
bson_iter_key(&child4_iter);
|
||||
if (!strcmp(child4_key, "server_name") &&
|
||||
BSON_ITER_HOLDS_UTF8(&child4_iter)) {
|
||||
utf8 = bson_iter_utf8(&child4_iter, &length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.application_server.server_name =
|
||||
ogs_strndup(utf8, length);
|
||||
} else if (!strcmp(child4_key, "default_handling")
|
||||
&& BSON_ITER_HOLDS_INT32(&child4_iter)) {
|
||||
ims_data->ifc[ifc_index]
|
||||
.application_server.default_handling =
|
||||
bson_iter_int32(&child4_iter);
|
||||
}
|
||||
}
|
||||
} else if (!strcmp(child3_key, "trigger_point") &&
|
||||
BSON_ITER_HOLDS_DOCUMENT(&child3_iter)) {
|
||||
bson_iter_recurse(&child3_iter, &child5_iter);
|
||||
while (bson_iter_next(&child5_iter)) {
|
||||
const char *child5_key =
|
||||
bson_iter_key(&child5_iter);
|
||||
if (!strcmp(child5_key, "condition_type_cnf") &&
|
||||
BSON_ITER_HOLDS_INT32(&child5_iter)) {
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point.condition_type_cnf =
|
||||
bson_iter_int32(&child5_iter);
|
||||
} else if (!strcmp(child5_key, "spt") &&
|
||||
BSON_ITER_HOLDS_ARRAY(&child5_iter)) {
|
||||
int spt_index = 0;
|
||||
bson_iter_recurse(&child5_iter, &child6_iter);
|
||||
while (bson_iter_next(&child6_iter)) {
|
||||
ogs_assert(spt_index < OGS_MAX_NUM_OF_SPT);
|
||||
bson_iter_recurse(&child6_iter,
|
||||
&child7_iter);
|
||||
while (bson_iter_next(&child7_iter)) {
|
||||
const char *child7_key =
|
||||
bson_iter_key(&child7_iter);
|
||||
if (!strcmp(child7_key,
|
||||
"condition_negated") &&
|
||||
BSON_ITER_HOLDS_INT32(
|
||||
&child7_iter)) {
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.condition_negated =
|
||||
bson_iter_int32(
|
||||
&child7_iter);
|
||||
} else if (!strcmp(child7_key, "group")
|
||||
&& BSON_ITER_HOLDS_INT32(
|
||||
&child7_iter)) {
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.group = bson_iter_int32(
|
||||
&child7_iter);
|
||||
} else if (!strcmp(child7_key,
|
||||
"method") &&
|
||||
BSON_ITER_HOLDS_UTF8(
|
||||
&child7_iter)) {
|
||||
utf8 = bson_iter_utf8(&child7_iter,
|
||||
&length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.method =
|
||||
ogs_strndup(utf8, length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.type = OGS_SPT_HAS_METHOD;
|
||||
} else if (!strcmp(child7_key,
|
||||
"session_case") &&
|
||||
BSON_ITER_HOLDS_INT32(
|
||||
&child7_iter)) {
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.session_case =
|
||||
bson_iter_int32(
|
||||
&child7_iter);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.type =
|
||||
OGS_SPT_HAS_SESSION_CASE;
|
||||
} else if (!strcmp(child7_key,
|
||||
"sip_header") &&
|
||||
BSON_ITER_HOLDS_DOCUMENT(
|
||||
&child7_iter)) {
|
||||
bson_iter_recurse(&child7_iter,
|
||||
&child8_iter);
|
||||
while (bson_iter_next(
|
||||
&child8_iter)) {
|
||||
const char *child8_key =
|
||||
bson_iter_key(
|
||||
&child8_iter);
|
||||
if (!strcmp(child8_key,
|
||||
"header") &&
|
||||
BSON_ITER_HOLDS_UTF8(
|
||||
&child8_iter)) {
|
||||
utf8 = bson_iter_utf8(
|
||||
&child8_iter,
|
||||
&length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.header =
|
||||
ogs_strndup(utf8,
|
||||
length);
|
||||
} else if (!strcmp(child8_key,
|
||||
"content") &&
|
||||
BSON_ITER_HOLDS_UTF8(
|
||||
&child8_iter)) {
|
||||
utf8 = bson_iter_utf8(
|
||||
&child8_iter,
|
||||
&length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.header_content =
|
||||
ogs_strndup(utf8,
|
||||
length);
|
||||
}
|
||||
}
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.type = OGS_SPT_HAS_SIP_HEADER;
|
||||
} else if (!strcmp(child7_key,
|
||||
"sdp_line") &&
|
||||
BSON_ITER_HOLDS_DOCUMENT(
|
||||
&child7_iter)) {
|
||||
bson_iter_recurse(&child7_iter,
|
||||
&child9_iter);
|
||||
while (bson_iter_next(
|
||||
&child9_iter)) {
|
||||
const char *child9_key =
|
||||
bson_iter_key(
|
||||
&child9_iter);
|
||||
if (!strcmp(child9_key,
|
||||
"line") &&
|
||||
BSON_ITER_HOLDS_UTF8(
|
||||
&child9_iter)) {
|
||||
utf8 = bson_iter_utf8(
|
||||
&child9_iter,
|
||||
&length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.sdp_line =
|
||||
ogs_strndup(utf8,
|
||||
length);
|
||||
} else if (!strcmp(child9_key,
|
||||
"content") &&
|
||||
BSON_ITER_HOLDS_UTF8(
|
||||
&child9_iter)) {
|
||||
utf8 = bson_iter_utf8(
|
||||
&child9_iter,
|
||||
&length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.sdp_line_content =
|
||||
ogs_strndup(utf8,
|
||||
length);
|
||||
}
|
||||
}
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.type = OGS_SPT_HAS_SDP_LINE;
|
||||
} else if (!strcmp(child7_key,
|
||||
"request_uri") &&
|
||||
BSON_ITER_HOLDS_UTF8(
|
||||
&child7_iter)) {
|
||||
utf8 = bson_iter_utf8(&child7_iter,
|
||||
&length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.request_uri =
|
||||
ogs_strndup(utf8, length);
|
||||
ims_data->ifc[ifc_index]
|
||||
.trigger_point
|
||||
.spt[spt_index]
|
||||
.type = OGS_SPT_HAS_REQUEST_URI;
|
||||
}
|
||||
}
|
||||
spt_index++;
|
||||
}
|
||||
ims_data->ifc->trigger_point.num_of_spt =
|
||||
spt_index;
|
||||
}
|
||||
}
|
||||
}
|
||||
}
|
||||
ifc_index++;
|
||||
}
|
||||
ims_data->num_of_ifc = ifc_index;
|
||||
}
|
||||
}
|
||||
|
||||
|
||||
@@ -1,5 +1,5 @@
|
||||
/*
|
||||
* Copyright (C) 2019-2023 by Sukchan Lee <acetcom@gmail.com>
|
||||
* Copyright (C) 2019-2024 by Sukchan Lee <acetcom@gmail.com>
|
||||
*
|
||||
* This file is part of Open5GS.
|
||||
*
|
||||
@@ -19,7 +19,8 @@
|
||||
|
||||
#include "ogs-dbi.h"
|
||||
|
||||
int ogs_dbi_session_data(char *supi, ogs_s_nssai_t *s_nssai, char *dnn,
|
||||
int ogs_dbi_session_data(
|
||||
const char *supi, const ogs_s_nssai_t *s_nssai, const char *dnn,
|
||||
ogs_session_data_t *session_data)
|
||||
{
|
||||
int rv = OGS_OK;
|
||||
@@ -85,6 +86,7 @@ int ogs_dbi_session_data(char *supi, ogs_s_nssai_t *s_nssai, char *dnn,
|
||||
if (!strcmp(key, OGS_SLICE_STRING) && BSON_ITER_HOLDS_ARRAY(&iter)) {
|
||||
bson_iter_recurse(&iter, &child1_iter);
|
||||
while (bson_iter_next(&child1_iter)) {
|
||||
bool sst_presence = false;
|
||||
uint8_t sst;
|
||||
ogs_uint24_t sd;
|
||||
|
||||
@@ -97,6 +99,7 @@ int ogs_dbi_session_data(char *supi, ogs_s_nssai_t *s_nssai, char *dnn,
|
||||
|
||||
if (!strcmp(child2_key, OGS_SST_STRING) &&
|
||||
BSON_ITER_HOLDS_INT32(&child2_iter)) {
|
||||
sst_presence = true;
|
||||
sst = bson_iter_int32(&child2_iter);
|
||||
} else if (!strcmp(child2_key, OGS_SD_STRING) &&
|
||||
BSON_ITER_HOLDS_UTF8(&child2_iter)) {
|
||||
@@ -109,7 +112,7 @@ int ogs_dbi_session_data(char *supi, ogs_s_nssai_t *s_nssai, char *dnn,
|
||||
}
|
||||
}
|
||||
|
||||
if (!sst) {
|
||||
if (!sst_presence) {
|
||||
ogs_error("No SST");
|
||||
continue;
|
||||
}
|
||||
@@ -166,6 +169,9 @@ done:
|
||||
} else if (!strcmp(child4_key, OGS_TYPE_STRING) &&
|
||||
BSON_ITER_HOLDS_INT32(&child4_iter)) {
|
||||
session->session_type = bson_iter_int32(&child4_iter);
|
||||
} else if (!strcmp(child4_key, OGS_LBO_ROAMING_ALLOWED_STRING) &&
|
||||
BSON_ITER_HOLDS_BOOL(&child4_iter)) {
|
||||
session->lbo_roaming_allowed = bson_iter_bool(&child4_iter);
|
||||
} else if (!strcmp(child4_key, OGS_QOS_STRING) &&
|
||||
BSON_ITER_HOLDS_DOCUMENT(&child4_iter)) {
|
||||
bson_iter_recurse(&child4_iter, &child5_iter);
|
||||
|
||||
@@ -28,7 +28,8 @@
|
||||
extern "C" {
|
||||
#endif
|
||||
|
||||
int ogs_dbi_session_data(char *supi, ogs_s_nssai_t *s_nssai, char *dnn,
|
||||
int ogs_dbi_session_data(
|
||||
const char *supi, const ogs_s_nssai_t *s_nssai, const char *dnn,
|
||||
ogs_session_data_t *session_data);
|
||||
|
||||
#ifdef __cplusplus
|
||||
|
||||
@@ -1,5 +1,5 @@
|
||||
/*
|
||||
* Copyright (C) 2019-2023 by Sukchan Lee <acetcom@gmail.com>
|
||||
* Copyright (C) 2019-2024 by Sukchan Lee <acetcom@gmail.com>
|
||||
*
|
||||
* This file is part of Open5GS.
|
||||
*
|
||||
@@ -39,9 +39,16 @@ int ogs_dbi_auth_info(char *supi, ogs_dbi_auth_info_t *auth_info)
|
||||
ogs_assert(auth_info);
|
||||
|
||||
supi_type = ogs_id_get_type(supi);
|
||||
ogs_assert(supi_type);
|
||||
if (!supi_type) {
|
||||
ogs_error("Invalid supi=%s", supi);
|
||||
return OGS_ERROR;
|
||||
}
|
||||
supi_id = ogs_id_get_value(supi);
|
||||
ogs_assert(supi_id);
|
||||
if (!supi_id) {
|
||||
ogs_error("Invalid supi=%s", supi);
|
||||
ogs_free(supi_type);
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
query = BCON_NEW(supi_type, BCON_UTF8(supi_id));
|
||||
#if MONGOC_CHECK_VERSION(1, 5, 0)
|
||||
@@ -459,6 +466,7 @@ int ogs_dbi_subscription_data(char *supi,
|
||||
bson_iter_recurse(&iter, &child1_iter);
|
||||
while (bson_iter_next(&child1_iter)) {
|
||||
ogs_slice_data_t *slice_data = NULL;
|
||||
bool sst_presence = false;
|
||||
|
||||
ogs_assert(
|
||||
subscription_data->num_of_slice < OGS_MAX_NUM_OF_SLICE);
|
||||
@@ -476,6 +484,7 @@ int ogs_dbi_subscription_data(char *supi,
|
||||
if (!strcmp(child2_key, OGS_SST_STRING) &&
|
||||
BSON_ITER_HOLDS_INT32(&child2_iter)) {
|
||||
slice_data->s_nssai.sst = bson_iter_int32(&child2_iter);
|
||||
sst_presence = true;
|
||||
} else if (!strcmp(child2_key, OGS_SD_STRING) &&
|
||||
BSON_ITER_HOLDS_UTF8(&child2_iter)) {
|
||||
utf8 = bson_iter_utf8(&child2_iter, &length);
|
||||
@@ -515,6 +524,11 @@ int ogs_dbi_subscription_data(char *supi,
|
||||
BSON_ITER_HOLDS_INT32(&child4_iter)) {
|
||||
session->session_type =
|
||||
bson_iter_int32(&child4_iter);
|
||||
} else if (!strcmp(child4_key,
|
||||
OGS_LBO_ROAMING_ALLOWED_STRING) &&
|
||||
BSON_ITER_HOLDS_BOOL(&child4_iter)) {
|
||||
session->lbo_roaming_allowed =
|
||||
bson_iter_bool(&child4_iter);
|
||||
} else if (!strcmp(child4_key,
|
||||
OGS_QOS_STRING) &&
|
||||
BSON_ITER_HOLDS_DOCUMENT(&child4_iter)) {
|
||||
@@ -787,6 +801,12 @@ int ogs_dbi_subscription_data(char *supi,
|
||||
}
|
||||
}
|
||||
}
|
||||
|
||||
if (!sst_presence) {
|
||||
ogs_error("No SST");
|
||||
continue;
|
||||
}
|
||||
|
||||
subscription_data->num_of_slice++;
|
||||
}
|
||||
} else if (!strcmp(key, OGS_MME_HOST_STRING) &&
|
||||
|
||||
@@ -28,6 +28,15 @@
|
||||
extern "C" {
|
||||
#endif
|
||||
|
||||
/* Configuration for ogs_diam_stats_ctx_t: */
|
||||
typedef struct ogs_diam_config_stats_s {
|
||||
/* Frequency at which freeDiameter thread stats are updated to the app. 0 = default 60 seconds. */
|
||||
unsigned int interval_sec;
|
||||
/* Size of struct to allocate for diameters private statistics, see ogs_diam_stats_ctx_t.
|
||||
* Defaults to 0, no priv_stats allocated. */
|
||||
size_t priv_stats_size;
|
||||
} ogs_diam_config_stats_t;
|
||||
|
||||
/* This is default diameter configuration if there is no config file
|
||||
* The Configuration : No TLS, Only TCP */
|
||||
typedef struct ogs_diam_config_s {
|
||||
@@ -43,6 +52,9 @@ typedef struct ogs_diam_config_s {
|
||||
/* the local port for Diameter/TLS (default: 5658) in host byte order */
|
||||
uint16_t cnf_port_tls;
|
||||
|
||||
/* default TC timer */
|
||||
int cnf_timer_tc;
|
||||
|
||||
struct {
|
||||
/* the peer does not relay messages (0xffffff app id) */
|
||||
unsigned no_fwd: 1;
|
||||
@@ -64,8 +76,13 @@ typedef struct ogs_diam_config_s {
|
||||
const char *identity;
|
||||
const char *addr; /* IP address of the remote peer */
|
||||
uint16_t port; /* port to connect to. 0: default. */
|
||||
int tc_timer; /* TcTimer value to use for this peer, use default if 0 */
|
||||
} conn[MAX_NUM_OF_FD_CONN];
|
||||
int num_of_conn;
|
||||
|
||||
/* Configure ogs_diam_stats_ctx_t: */
|
||||
ogs_diam_config_stats_t stats;
|
||||
|
||||
} ogs_diam_config_t;
|
||||
|
||||
int ogs_diam_init(int mode, const char *conffile, ogs_diam_config_t *fd_config);
|
||||
@@ -73,7 +90,7 @@ int ogs_diam_start(void);
|
||||
void ogs_diam_final(void);
|
||||
|
||||
int ogs_diam_config_init(ogs_diam_config_t *fd_config);
|
||||
bool ogs_diam_app_connected(uint32_t app_id);
|
||||
bool ogs_diam_is_relay_or_app_advertised(uint32_t app_id);
|
||||
|
||||
int fd_avp_search_avp ( struct avp * groupedavp,
|
||||
struct dict_object * what, struct avp ** avp );
|
||||
|
||||
@@ -69,6 +69,9 @@ static int diam_config_apply(ogs_diam_config_t *fd_config)
|
||||
if (fd_config->cnf_flags.no_fwd)
|
||||
fd_g_config->cnf_flags.no_fwd = fd_config->cnf_flags.no_fwd;
|
||||
|
||||
if (fd_config->cnf_timer_tc)
|
||||
fd_g_config->cnf_timer_tc = fd_config->cnf_timer_tc;
|
||||
|
||||
/********************************************************************
|
||||
* Diameter Client
|
||||
*/
|
||||
@@ -86,6 +89,8 @@ static int diam_config_apply(ogs_diam_config_t *fd_config)
|
||||
fddpi.config.pic_flags.alg = PI_ALGPREF_SCTP;
|
||||
fddpi.config.pic_flags.sec |= PI_SEC_NONE;
|
||||
|
||||
fddpi.config.pic_tctimer = fd_config->conn[i].tc_timer;
|
||||
|
||||
fddpi.config.pic_port = fd_config->conn[i].port;
|
||||
fddpi.pi_diamid = (DiamId_t)fd_config->conn[i].identity;
|
||||
|
||||
@@ -100,7 +105,7 @@ static int diam_config_apply(ogs_diam_config_t *fd_config)
|
||||
fd_config->conn[i].addr, errno, strerror(errno));
|
||||
return OGS_ERROR;
|
||||
}
|
||||
|
||||
|
||||
CHECK_FCT_DO( fd_ep_add_merge(
|
||||
&fddpi.pi_endpoints, ai->ai_addr, ai->ai_addrlen,
|
||||
EP_FL_CONF | (disc ?: EP_ACCEPTALL) ), return OGS_ERROR);
|
||||
@@ -192,7 +197,7 @@ int ogs_diam_config_init(ogs_diam_config_t *fd_config)
|
||||
|
||||
/* Display configuration */
|
||||
b = fd_conf_dump(&buf, &len, NULL);
|
||||
LOG_SPLIT(FD_LOG_NOTICE, NULL,
|
||||
LOG_SPLIT(FD_LOG_NOTICE, NULL,
|
||||
b ?: (char*)"<Error during configuration dump...>", NULL);
|
||||
free(buf);
|
||||
|
||||
|
||||
@@ -28,6 +28,8 @@ int ogs_diam_init(int mode, const char *conffile, ogs_diam_config_t *fd_config)
|
||||
{
|
||||
int ret;
|
||||
|
||||
ogs_assert(fd_config);
|
||||
|
||||
gnutls_global_set_log_level(0);
|
||||
gnutls_global_set_log_function(diam_gnutls_log_func);
|
||||
|
||||
@@ -36,14 +38,14 @@ int ogs_diam_init(int mode, const char *conffile, ogs_diam_config_t *fd_config)
|
||||
if (ret != 0) {
|
||||
ogs_error("fd_log_handler_register() failed");
|
||||
return ret;
|
||||
}
|
||||
}
|
||||
|
||||
ret = fd_core_initialize();
|
||||
if (ret != 0) {
|
||||
ogs_error("fd_core_initialize() failed");
|
||||
return ret;
|
||||
}
|
||||
|
||||
}
|
||||
|
||||
/* Parse the configuration file */
|
||||
if (conffile) {
|
||||
CHECK_FCT_DO( fd_core_parseconf(conffile), goto error );
|
||||
@@ -55,7 +57,10 @@ int ogs_diam_init(int mode, const char *conffile, ogs_diam_config_t *fd_config)
|
||||
CHECK_FCT( ogs_diam_message_init() );
|
||||
|
||||
/* Initialize FD logger */
|
||||
CHECK_FCT_DO( ogs_diam_logger_init(mode), goto error );
|
||||
CHECK_FCT_DO( ogs_diam_logger_init(), goto error );
|
||||
|
||||
/* Initialize FD stats */
|
||||
CHECK_FCT_DO( ogs_diam_stats_init(mode, &fd_config->stats), goto error );
|
||||
|
||||
return 0;
|
||||
error:
|
||||
@@ -72,7 +77,7 @@ int ogs_diam_start(void)
|
||||
|
||||
CHECK_FCT_DO( fd_core_waitstartcomplete(), goto error );
|
||||
|
||||
CHECK_FCT( ogs_diam_logger_stats_start() );
|
||||
CHECK_FCT( ogs_diam_stats_start() );
|
||||
|
||||
return 0;
|
||||
error:
|
||||
@@ -84,6 +89,7 @@ error:
|
||||
|
||||
void ogs_diam_final()
|
||||
{
|
||||
ogs_diam_stats_final();
|
||||
ogs_diam_logger_final();
|
||||
|
||||
CHECK_FCT_DO( fd_core_shutdown(), ogs_error("fd_core_shutdown() failed") );
|
||||
@@ -118,12 +124,12 @@ static void diam_log_func(int printlevel, const char *format, va_list ap)
|
||||
ogs_log_printf(level, OGS_LOG_DOMAIN, 0, NULL, 0, NULL, 0, __VA_ARGS__)
|
||||
|
||||
switch(printlevel) {
|
||||
case FD_LOG_ANNOYING:
|
||||
case FD_LOG_ANNOYING:
|
||||
diam_log_printf(OGS_LOG_TRACE, "[%d] %s\n", printlevel, buffer);
|
||||
break;
|
||||
break;
|
||||
case FD_LOG_DEBUG:
|
||||
diam_log_printf(OGS_LOG_TRACE, "[%d] %s\n", printlevel, buffer);
|
||||
break;
|
||||
break;
|
||||
case FD_LOG_INFO:
|
||||
diam_log_printf(OGS_LOG_TRACE, "[%d] %s\n", printlevel, buffer);
|
||||
break;
|
||||
|
||||
Some files were not shown because too many files have changed in this diff Show More
Reference in New Issue
Block a user